Show how the basic snooping protocol of Figure 5.6 can be changed for a write-through cache. What
Question:
Show how the basic snooping protocol of Figure 5.6 can be changed for a write-through cache. What is the major hardware functionality that is not needed with a write-through cache compared with a write-back cache?
Figure 5.6
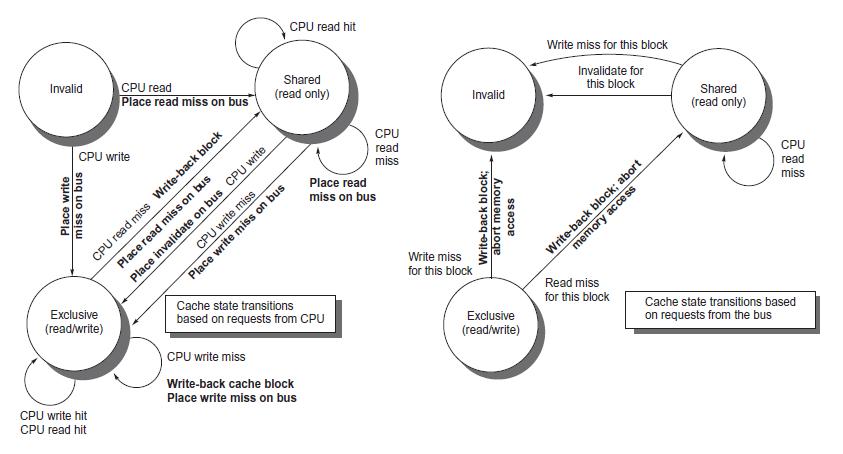
Transcribed Image Text:
Invalid CPU write Place write miss on bus CPU read Place read miss on bus Exclusive (read/write) CPU read miss Write-back block Place read miss on bus CPU write hit CPU read hit Place invalidate on bus CPU write CPU read hit Shared (read only) CPU write miss Place write miss on bus Cache state transitions based on requests from CPU CPU write miss Write-back cache block Place write miss on bus CPU read miss Place read miss on bus Invalid Write miss for this block Write-back block; abort memory access Exclusive (read/write) Write miss for this block Invalidate for this block memory access Write-back block; abort Read miss for this block Shared (read only) CPU read miss Cache state transitions based on requests from the bus
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 100% (QA)

Answered By

Wonder Dzidzormenu
As a professional accountant and a teacher, I explain account ing concepts in a more practical way that makes students more connected to the subject.
With over 10 years of teaching accounting , I offer a well constructed , easily understood and in-depth explanations to students questions.
5.00+
1+ Reviews
10+ Question Solved
Related Book For 

Computer Architecture A Quantitative Approach
ISBN: 9780128119051
6th Edition
Authors: John L. Hennessy, David A. Patterson
Question Posted:
Students also viewed these Computer science questions
-
The switched snooping protocol of Figure 4.40 assumes that memory "knows" whether a processor node is in state Modified and thus will respond with data. Real systems implement this in one of two...
-
Let A, B be sets. Define: (a) the Cartesian product (A B) (b) the set of relations R between A and B (c) the identity relation A on the set A [3 marks] Suppose S, T are relations between A and B, and...
-
can someone solve this Modern workstations typically have memory systems that incorporate two or three levels of caching. Explain why they are designed like this. [4 marks] In order to investigate...
-
A fast-food restaurant operates both a drive through facility and a walk-in facility. On a randomly selected day, let X and Y, respectively, be the proportions of the time that the drive-through and...
-
Methane is compressed adiabatically by a steady-flow compressor from 2 MPa and -10°C to 10 MPa and 110°C at a rate of 0.55 kg/s. Using the generalized charts, determine the required power...
-
For each of the following, write molecular and net ionic equations for any precipitation reaction that occurs. If no reaction occurs, indicate this. a. Solutions of barium nitrate and lithium sulfate...
-
Describe the six categories of early warning signs of potential fraud.
-
Nayak Company has recorded the following items in its financial records. Cash in bank ............ $ 41,000 Cash in plant expansion fund ...... 100,000 Cash on hand ............ 8,000 Highly liquid...
-
Laverne owns 100% stock of the Pizza Bowl, Inc. (PB), which operates a classy combination bowling alley/pizza parlor. Her basis in the stock is $24,000. In its first year of existence, PB earned...
-
Delaplane Computers gets most of its component parts from suppliers in Pacific Rim countries, who ship to the companys main distribution center near Long Beach, California, where computers are built...
-
Please answer the following problems: a. Add a clean exclusive state to the basic snooping cache coherence protocol (Figure 5.6). Show the protocol in the finite state machine format used in the...
-
In this exercise, we examine the effect of the interconnection network topology on the CPI of programs running on a 64-processor distributed-memory multiprocessor. The processor clock rate is 2.0...
-
Simplify the given expressions. Express all answers with positive exponents. 4x1/2 + 1/2x-1/ (4x + 1)
-
If sellers of scarce resources are not allowed to increase prices to equilibrate supply and demand after a disaster, how do you think these resources should be allocated among the population? What...
-
Does the presence or otherwise of a Public credit registries and or private credit Bureau explain the differences (if any) in the rankings pf countries ?
-
Explain why the long-run demand for durable goods is more income elastic than the short-run demand. Is this also the case for non-durables?
-
What is the Demand of coffee in Canada, opportunity cost of doing coffee stall in Vancouver and How it is going to be beneficial for the economy? Therefore, what would you like Government to do for...
-
A door to door vacuum cleaner salesman finds that for each housevisit he has a 20% chance to sell the vacuum cleaner. Today heplans to visit 3 houses. Assume that customers' purchase behavioris...
-
Which commentator embraces your concept of the relationship of power and good? Does power corrupt? Or is a person useful to society only if he has the power to utilize his goodness?
-
The May 2014 revenue and cost information for Houston Outfitters, Inc. follow: Sales Revenue (at standard).............. $ 540,000 Cost of Goods Sold (at standard) ..........341,000 Direct Materials...
-
What effect would you expect a wider bandwidth to have on the noise in a channel?
-
Discuss the trade-offs between fiber-optic and satellite communication in terms of costs, signal capacity, signaling method, interference, likelihood of failure and repair issues, multi-point...
-
Describe the advantages that repeaters have over amplifiers.
-
An insurance agent is trying to sell you an immediate retirement annuity that offers $16,000 per year at the end of each of the next 30 years. The price of the investment proposed by the agent is...
-
1. Suppose we have the following annual risk-free bonds Maturity Price Coupon Rate YTM 1 98 0% 2.04% 2 101 3% 2.48% 3 103 4% 2.94% 4 101 2% 1.73% 5 103 5% 4.32% a) Find the zero rates for all 5...
-
You hold a portfolio of three stocks with the following investments and individual betas. Stock A $12,000 investment has a beta of 1.75. Stock B $20,000 investment has a beta of 0.50. Stock C $12,000...

Study smarter with the SolutionInn App


