Can you suggest a security improvement to either option in Figure 6.11, using only three DES chips
Question:
Can you suggest a security improvement to either option in Figure 6.11, using only three DES chips and some number of XOR functions? Assume you are still limited to two keys.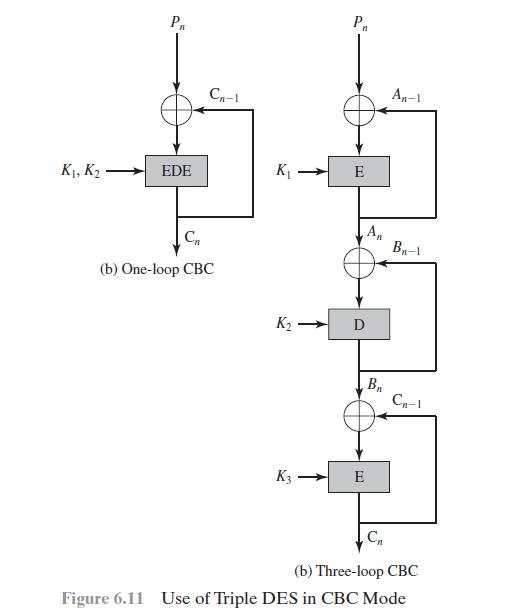
Transcribed Image Text:
K, K P EDE C-1 C (b) One-loop CBC K K K3 Pr n E D A E B C An-1 B-1 C-1 (b) Three-loop CBC Figure 6.11 Use of Triple DES in CBC Mode
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 0% (1 review)
Instead of mathrmCBCmathrmCBCmathrmCBCmathrmX use ECB mathrm...View the full answer

Answered By

PU Student
cost accounting
financial accounting
auditing
internal control
business analyst
tax
i have 3 years experience in field of management & auditing in different multinational firms. i also have 16 months experience as an accountant in different international firms. secondary school certification.
higher secondary school certification.
bachelors in mathematics.
cost & management accountant
4.80+
4+ Reviews
10+ Question Solved
Related Book For 

Question Posted:
Students also viewed these Computer science questions
-
Managing Scope Changes Case Study Scope changes on a project can occur regardless of how well the project is planned or executed. Scope changes can be the result of something that was omitted during...
-
In this exercise, we explore the concept o f marginal rates of substitution (and, in part B, its relation to utility functions) further. A: Suppose I own 3 bananas and 6 apples, and you own 5 bananas...
-
List three specific parts of the Case Guide, Objectives and Strategy Section (See below) that you had the most difficulty understanding. Describe your current understanding of these parts. Provide...
-
Dream House Builders, Inc. applies overhead by linking it to direct labor. At the start of the current period, management predicts total direct labor costs of $100,000 and total overhead costs of...
-
A meteorite melts and burn up at temperatures of 3000 K. If it hits air at 5 kPa, 50 K how high a velocity should it has to experience such a temperature?
-
The shaft is supported at its ends by two bearings A and B and is subjected to the forces applied to the pulleys fixed to the shaft. Determine the resultant internal loadings acting on the cross...
-
Presented here are the amounts of Assets, Liabilities, Stockholders Equity, Revenues, and Expenses of Camp Out, Inc., at October 31,2011. The items are listed in alphabetical order. The retained...
-
Mike and Julie Bedard are a working couple. They will file a joint income tax return. This year, they have the following taxable income: 1. $125,000 from salary and wages (ordinary income) 2. $1,000...
-
Describe the design choices organizations face in creating a mechanistic vs. an organic structure.
-
The Merkle-Hellman attack on 3DES begins by assuming a value of A = 0 (Figure 6.1b). Then, for each of the 2 56 possible values of K 1 , the plaintext P that produces A = 0 is determined. Describe...
-
You want to build a hardware device to do block encryption in the cipher block chaining (CBC) mode using an algorithm stronger than DES. 3DES is a good candidate. Figure 6.11 shows two possibilities,...
-
The following T-accounts summarize the operations of Chen Construction Company for July 2009. Required: 1. Assuming that only one transaction occurred on each day (beginning on July 2) and that no...
-
What effects do you think positive and negative thoughts, images, and self-talk have on performance? Share an example of a time when positive or negative thoughts/self-talk have affected your...
-
1.) You drive 60 miles North then 50 miles West, then 20 miles South. How far are you from where you started? Express your answer in miles. 2.) A ball is kicked from the origin at an angle = 30 with...
-
Knowing that the program's department head is not technology-savvy, what steps would you take to get these new tablets into the classroom? Describe at least 3 steps you would take to reach your goal...
-
Global climate change is frequently in the news, sometimes in a dramatic and sensational format. Informed citizens of the world need to be able to interpret these news articles and determine their...
-
Illustration #5a Pepper Company, which is a calendar-year-reporting company, purchased 65% of the common stock of Salt Company, on December 31, 2019, for 20,000 shares of common stock of Pepper...
-
Refer to Note 1. Segmental Information on page 16 of Air New Zealand 2012 Annual Report. In what geographical segments did Air New Zealand operate in 2012? Briefly explain how investors and analysts...
-
What is taxable income, and what is the formula for determining taxable income?
-
Table shows the process states for the VAX/VMS operating system. a. Can you provide a justification for the existence of so many distinct wait states? b. Why do the following states not have resident...
-
The VAX/VMS operating system makes use of four processor access modes to facilitate the protection and sharing of system resources among processes. The access mode determines Instruction execution...
-
The VMS scheme discussed in the preceding problem is often referred to as a ring protection structure, as illustrated in Figure. Indeed, the simple kernel/user scheme, as described in Section 3.3, is...
-
A portable compressed air tank is frequently used to inflate flat tires. The tank is initially filled with compressed air at 150 psia and 70F, and the air in the tire may be assumed to be at...
-
A cylinder 6 cm in diameter and 18 cm in height is to be cast from brass alloy using an open sand mould. The melting temperature of brass is 926 C, and the pouring temperature will be 1100 C. Assume...
-
Rube Goldberg was a cartoonist (NewYork Post) that became famous for drawing very complicated machinesthat performed very simple tasks. A typical Rube Goldberg devicecould not perform a job as...

Study smarter with the SolutionInn App


