Question
Describe any THREE characteristics of what might be regarded as a good encryption algorithm. Two of the modes under which a symmetric encryption algorithm can
Describe any THREE characteristics of what might be regarded as a good encryption algorithm. Two of the modes under which a symmetric encryption algorithm can operate are described by the following equations:
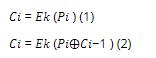
(i) Identify the modes of operation and explain the meaning of all terms in the above equations.
(ii) Explain why a practical implementation of mode (2) should require the use of mode (1) during the initial phase of the dialogue. [6 marks]
(c) Explain the meaning of the terms message integrity and authentication in the context of network security. Describe how public key encryption technology can be used to implement
(i) a message integrity protocol and
(ii) an authentication protocol.
Ci = Ek (Pi) (1) Ci = Ek (Pi@Ci-1) (2)
Step by Step Solution
3.32 Rating (116 Votes )
There are 3 Steps involved in it
Step: 1
Three Characteristics of a Good Encryption Algorithm Security A good encryption algorithm should provide a high level of security making it computationally infeasible for an unauthorized party to decr...
Get Instant Access with AI-Powered Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


