Question: Please help. It is only one question. Code in Java. I had to take multiple screenshots to show all the info. File Tools View cu
Please help. It is only one question. Code in Java. I had to take multiple screenshots to show all the info.
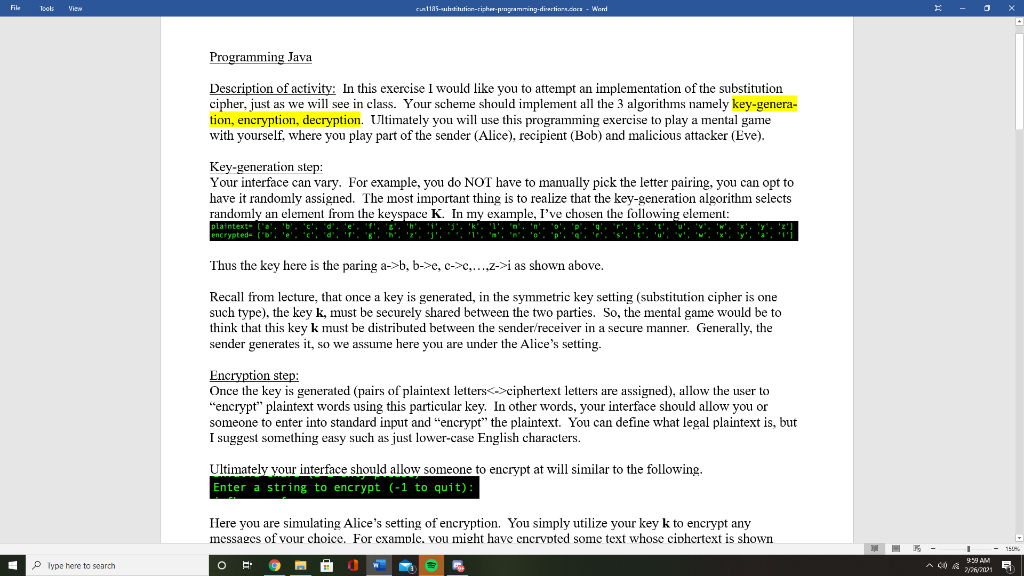
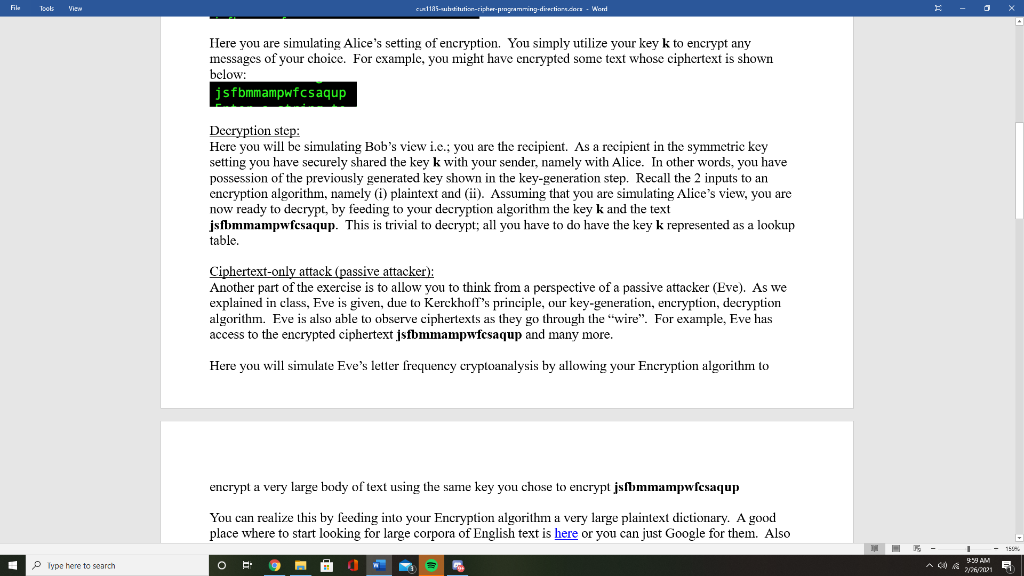
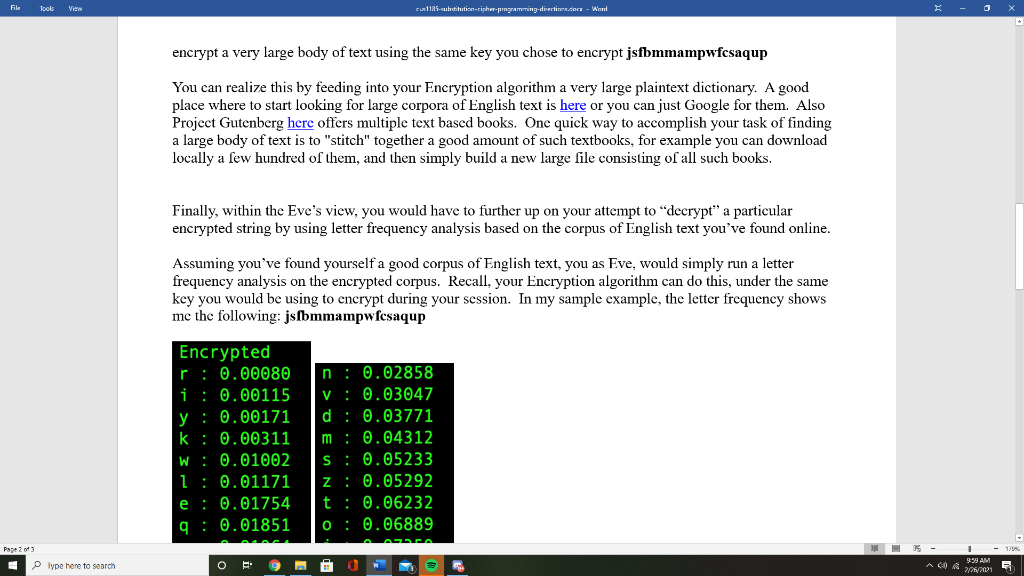
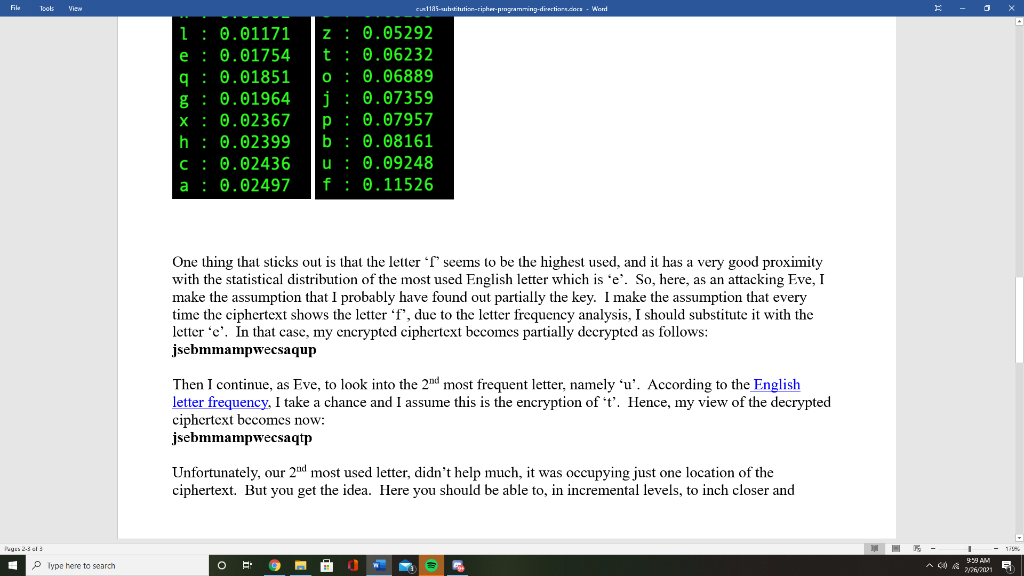
File Tools View cu 1185-substitutin-ripher-programming direction.com - Word - 0 Programming Java Description of activity: In this exercise I would like you to attempt an implementation of the substitution cipher, just as we will see in class. Your scheme should implement all the 3 algorithms namely key-genera- tion, encryption, decryption. Ultimately you will use this programming exercise to play a mental game with yourself, where you play part of the sender (Alice), recipient (Bob) and malicious attacker (Eve). Key-generation step: Your interface can vary. For example, you do NOT have to manually pick the letter pairing, you can opt to have it randomly assigned. The most important thing is to realize that the key-generation algorithm selects randomly an element from the keyspace K. In my example, I've chosen the following element: plaintext ta' Thus the key here is the paring a->b, b->e, c->.....2->i as shown above. Recall from lecture, that once a key is generated, in the symmetric key setting (substitution cipher is one such type), the key k, must be securely shared between the two parties. So, the mental game would be to think that this key k must be distributed between the sender/receiver in a secure manner. Generally, the sender generates it, so we assume here you are under the Alice's setting. Encryption step: Once the key is generated (pairs of plaintext lettersciphertext letters are assigned), allow the user to "encrypt" plaintext words using this particular key. In other words, your interface should allow you or someone to enter into standard input and "encrypt" the plaintext. You can define what legal plaintext is, but I suggest something easy such as just lower-case English characters. Ultimately your interface should allow someone to encrypt at will similar to the following. Enter a string to encrypt (-1 to quit): Here you are simulating Alice's setting of encryption. You simply utilize your key k to encrypt any messages of vour choice. For example, vou might have encrypted some text whose ciphertext is shown Type here to search 398AM O 2/7/2011 File Tools View cus:1185-auhtihution-tipher-programming direction.com Word - 0 Here you are simulating Alice's setting of encryption. You simply utilize your key k to encrypt any messages of your choice. For example, you might have encrypted some text whose ciphertext is shown below: jsfbmmampwfcsaqup Decryption step: Here you will be simulating Bob's view i.e.: you are the recipient. As a recipient in the symmetric key setting you have securely shared the key k with your sender, namely with Alice. In other words, you have possession of the previously generated key shown in the key-generation step. Recall the 2 inputs to an encryption algorithm, namely (1) plaintext and (ii). Assuming that you are simulating Alice's view, you are now ready to decrypt, by feeding to your decryption algorithm the key k and the text jsfbmmampwfesaqup. This is trivial to decrypt; all you have to do have the key k represented as a lookup table Ciphertext-only attack (passive attacker): Another part of the exercise is to allow you to think from a perspective of a passive attacker (Eve). As we explained in class, Eve is given, due to Kerckhofl's principle, our key-generation, encryption, decryption algorithm. Eve is also able to observe ciphertexts as they go through the "Wire". For example, Eve has access to the encrypted ciphertext jsfbmmampwfesaqup and many more. Here you will simulate Eve's letter frequency cryptoanalysis by allowing your Encryption algorithm to encrypt very large body of text using the same key you chose to encrypt jsfbmmampwfesaqup You can realize this by feeding into your Encryption algorithm a very large plaintext dictionary. A good place where to start looking for large corpora of English text is here or you can just Google for them. Also Type here to search 38 AM O 2/7/2011 File Tools View cu 1185-suhdiutin-ripher-programming direction.com - Word - 0 encrypt a very large body of text using the same key you chose to encrypt jsfbmmampwfesaqup You can realize this by feeding into your Encryption algorithm a very large plaintext dictionary. A good place where to start looking for large corpora of English text is here or you can just Google for them. Also Project Gutenberg here offers multiple text based books. One quick way to accomplish your task of finding a large body of text is to "stitch" together a good amount of such textbooks, for example you can download locally a few hundred of them, and then simply build a new large file consisting of all such books. Finally, within the Eve's view, you would have to further up on your attempt to "decrypt" a particular encrypted string by using letter frequency analysis based on the corpus of English text you've found online. Assuming you've found yourself a good corpus of English text, you as Eve, would simply run a letter frequency analysis on the encrypted corpus. Recall, your Encryption algorithm can do this, under the same key you would be using to encrypt during your session. In my sample example, the letter frequency shows me the following: jsfbmmampwfesaqup Encrypted r : 0.00080 i: 0.00115 y : 0.00171 k: 0.00311 W: 0.01002 1 : 0.01171 e: 0.01754 9: 0.01851 n: 0.02858 V: 0.03047 d: 0.03771 m : 0.04312 S: 0.05233 Z: 0.05292 t : 0.06232 0 : 0.06889 Pape23 398AM Type here to search O 2/7/2011 File Tools View culis. dibution-ripher programming-direction.does. Word - 0 1: 0.01171 e: 0.01754 9: 0.01851 g: 0.01964 X: 0.02367 h: 0.02399 C: 0.02436 a: 0.02497 Z: 0.05292 t : 0.06232 O: 0.06889 j: 0.07359 P: 0.07957 b: 0.08161 u : 0.09248 f : 0.11526 One thing that sticks out is that the letter T seems to be the highest used, and it has a very good proximity with the statistical distribution of the most used English letter which is 'e. So, here, as an attacking Eve, I make the assumption that I probably have found out partially the key. I make the assumption that every time the ciphertext shows the letter 'f', due to the letter frequency analysis, I should substitute it with the letter 'e'. In that case, my encrypted ciphertext becomes partially decrypted as follows: jsebmmampwecsaqup Then I continue, as Eve, to look into the 2nd most frequent letter, namely 'u'. According to the English letter frequency, I take a chance and I assume this is the encryption of 't'. Hence, my view of the decrypted ciphertext becomes now: jsebmmampwecsaqtp Unfortunately, our 20 most used letter, didn't help much, it was occupying just one location of the ciphertext. But you get the idea. Here you should be able to, in incremental levels, to inch closer and Pyss 2013 398AM Type here to search 2/21/2001 File Tools View cuR 1185-tic-tipher-pigramming direction.cons. Word - 0 closer to a decryption based on the English language letter frequency, Programming Assignment Deliverables: What do I expect out of you in this exercise? 1. Source code of the full implementation of the substitution cipher (Java or Python only). 2. Source code of the full implementation of the letter analysis based on a good corpus of English language. Note on 1 and 2: Your code should compile/interpret without any errors and run with little effort from my side i.e., no fancy IDE's are necessary to compile/interpret and run. 3. Citation of the particular corpus you've found and its effectiveness. Ideally you should be able to match the first 7-8 letters precisely. I do not need you to upload the corpus, after all it might be into the GB size. I simply would like to know how I can duplicate your work in the event that I would like to take your script for a test-drive. 4. A simple HOWTO (text or Word or PDF) file which helps me understand how to test-drive your program. 5. A report which shows screenshots of your program in execution during the: key-generation (Alice's view) encryption (Alice's view) decryption phase (Bob's view) Eve's view of cryptanalyzing your scheme based on the letter frequency analysis, she runs on the captured large body of ciphertext. The report will give me a more complete view of your understanding of the scheme and what exactly you have done to cryptanalyze it. Please elaborate in full and be as thorough as possible as if you were to show it to a third party observer. Pysso 398AM Type here to search O E. 2/7/2011 File Tools View cu 1185-substitutin-ripher-programming direction.com - Word - 0 3. Citation of the particular corpus you've found and its effectiveness. Ideally you should be able to match the first 7-8 letters precisely. I do not need you to upload the corpus, after all it might be into the GB size. I simply would like to know how I can duplicate your work in the event that I would like to take your script for a test-drive. 4. A simple HOWTO (text or Word or PDF) file which helps me understand how to test-drive your program. 5. A report which shows screenshots of your program in execution during the: key-generation (Alice's view) encryption (Alice's view) decryption phase (Bob's view) Eve's view of cryptanalyzing your scheme based on the letter frequency analysis, she runs on the captured large body of ciphertext. The report will give me a more complete view of your understanding of the scheme and what exactly you have done to cryptanalyze it. Please elaborate in full and be as thorough as possible as if you were to show it to a third party observer . 6. You should upload items 1, 2, 4 and 5 on LMS and provide full description of the dataset I need to download if I want to take your script for a test-drive if I so choose. Note: Do not bundle the items into a zip file. Upload all required items individually. This allows me to see them within LMS. I do not want to download a zip file, extract it locally and view, all viewing should occur within the LMS. Special notes: You may utilize a Word document to write up your report and any appropriate screen shots along your steps. This is an individual assignment. Please upload the document as Lastname-Firstname- CUS-1185-substitution-cipher either in Word or PDF format in the proper LMS section along with items 1,2,4,5. Pysso Type here to search 3:38 AM 2/7/2011 File Tools View cu 1185-substitutin-ripher-programming direction.com - Word - 0 Programming Java Description of activity: In this exercise I would like you to attempt an implementation of the substitution cipher, just as we will see in class. Your scheme should implement all the 3 algorithms namely key-genera- tion, encryption, decryption. Ultimately you will use this programming exercise to play a mental game with yourself, where you play part of the sender (Alice), recipient (Bob) and malicious attacker (Eve). Key-generation step: Your interface can vary. For example, you do NOT have to manually pick the letter pairing, you can opt to have it randomly assigned. The most important thing is to realize that the key-generation algorithm selects randomly an element from the keyspace K. In my example, I've chosen the following element: plaintext ta' Thus the key here is the paring a->b, b->e, c->.....2->i as shown above. Recall from lecture, that once a key is generated, in the symmetric key setting (substitution cipher is one such type), the key k, must be securely shared between the two parties. So, the mental game would be to think that this key k must be distributed between the sender/receiver in a secure manner. Generally, the sender generates it, so we assume here you are under the Alice's setting. Encryption step: Once the key is generated (pairs of plaintext lettersciphertext letters are assigned), allow the user to "encrypt" plaintext words using this particular key. In other words, your interface should allow you or someone to enter into standard input and "encrypt" the plaintext. You can define what legal plaintext is, but I suggest something easy such as just lower-case English characters. Ultimately your interface should allow someone to encrypt at will similar to the following. Enter a string to encrypt (-1 to quit): Here you are simulating Alice's setting of encryption. You simply utilize your key k to encrypt any messages of vour choice. For example, vou might have encrypted some text whose ciphertext is shown Type here to search 398AM O 2/7/2011 File Tools View cus:1185-auhtihution-tipher-programming direction.com Word - 0 Here you are simulating Alice's setting of encryption. You simply utilize your key k to encrypt any messages of your choice. For example, you might have encrypted some text whose ciphertext is shown below: jsfbmmampwfcsaqup Decryption step: Here you will be simulating Bob's view i.e.: you are the recipient. As a recipient in the symmetric key setting you have securely shared the key k with your sender, namely with Alice. In other words, you have possession of the previously generated key shown in the key-generation step. Recall the 2 inputs to an encryption algorithm, namely (1) plaintext and (ii). Assuming that you are simulating Alice's view, you are now ready to decrypt, by feeding to your decryption algorithm the key k and the text jsfbmmampwfesaqup. This is trivial to decrypt; all you have to do have the key k represented as a lookup table Ciphertext-only attack (passive attacker): Another part of the exercise is to allow you to think from a perspective of a passive attacker (Eve). As we explained in class, Eve is given, due to Kerckhofl's principle, our key-generation, encryption, decryption algorithm. Eve is also able to observe ciphertexts as they go through the "Wire". For example, Eve has access to the encrypted ciphertext jsfbmmampwfesaqup and many more. Here you will simulate Eve's letter frequency cryptoanalysis by allowing your Encryption algorithm to encrypt very large body of text using the same key you chose to encrypt jsfbmmampwfesaqup You can realize this by feeding into your Encryption algorithm a very large plaintext dictionary. A good place where to start looking for large corpora of English text is here or you can just Google for them. Also Type here to search 38 AM O 2/7/2011 File Tools View cu 1185-suhdiutin-ripher-programming direction.com - Word - 0 encrypt a very large body of text using the same key you chose to encrypt jsfbmmampwfesaqup You can realize this by feeding into your Encryption algorithm a very large plaintext dictionary. A good place where to start looking for large corpora of English text is here or you can just Google for them. Also Project Gutenberg here offers multiple text based books. One quick way to accomplish your task of finding a large body of text is to "stitch" together a good amount of such textbooks, for example you can download locally a few hundred of them, and then simply build a new large file consisting of all such books. Finally, within the Eve's view, you would have to further up on your attempt to "decrypt" a particular encrypted string by using letter frequency analysis based on the corpus of English text you've found online. Assuming you've found yourself a good corpus of English text, you as Eve, would simply run a letter frequency analysis on the encrypted corpus. Recall, your Encryption algorithm can do this, under the same key you would be using to encrypt during your session. In my sample example, the letter frequency shows me the following: jsfbmmampwfesaqup Encrypted r : 0.00080 i: 0.00115 y : 0.00171 k: 0.00311 W: 0.01002 1 : 0.01171 e: 0.01754 9: 0.01851 n: 0.02858 V: 0.03047 d: 0.03771 m : 0.04312 S: 0.05233 Z: 0.05292 t : 0.06232 0 : 0.06889 Pape23 398AM Type here to search O 2/7/2011 File Tools View culis. dibution-ripher programming-direction.does. Word - 0 1: 0.01171 e: 0.01754 9: 0.01851 g: 0.01964 X: 0.02367 h: 0.02399 C: 0.02436 a: 0.02497 Z: 0.05292 t : 0.06232 O: 0.06889 j: 0.07359 P: 0.07957 b: 0.08161 u : 0.09248 f : 0.11526 One thing that sticks out is that the letter T seems to be the highest used, and it has a very good proximity with the statistical distribution of the most used English letter which is 'e. So, here, as an attacking Eve, I make the assumption that I probably have found out partially the key. I make the assumption that every time the ciphertext shows the letter 'f', due to the letter frequency analysis, I should substitute it with the letter 'e'. In that case, my encrypted ciphertext becomes partially decrypted as follows: jsebmmampwecsaqup Then I continue, as Eve, to look into the 2nd most frequent letter, namely 'u'. According to the English letter frequency, I take a chance and I assume this is the encryption of 't'. Hence, my view of the decrypted ciphertext becomes now: jsebmmampwecsaqtp Unfortunately, our 20 most used letter, didn't help much, it was occupying just one location of the ciphertext. But you get the idea. Here you should be able to, in incremental levels, to inch closer and Pyss 2013 398AM Type here to search 2/21/2001 File Tools View cuR 1185-tic-tipher-pigramming direction.cons. Word - 0 closer to a decryption based on the English language letter frequency, Programming Assignment Deliverables: What do I expect out of you in this exercise? 1. Source code of the full implementation of the substitution cipher (Java or Python only). 2. Source code of the full implementation of the letter analysis based on a good corpus of English language. Note on 1 and 2: Your code should compile/interpret without any errors and run with little effort from my side i.e., no fancy IDE's are necessary to compile/interpret and run. 3. Citation of the particular corpus you've found and its effectiveness. Ideally you should be able to match the first 7-8 letters precisely. I do not need you to upload the corpus, after all it might be into the GB size. I simply would like to know how I can duplicate your work in the event that I would like to take your script for a test-drive. 4. A simple HOWTO (text or Word or PDF) file which helps me understand how to test-drive your program. 5. A report which shows screenshots of your program in execution during the: key-generation (Alice's view) encryption (Alice's view) decryption phase (Bob's view) Eve's view of cryptanalyzing your scheme based on the letter frequency analysis, she runs on the captured large body of ciphertext. The report will give me a more complete view of your understanding of the scheme and what exactly you have done to cryptanalyze it. Please elaborate in full and be as thorough as possible as if you were to show it to a third party observer. Pysso 398AM Type here to search O E. 2/7/2011 File Tools View cu 1185-substitutin-ripher-programming direction.com - Word - 0 3. Citation of the particular corpus you've found and its effectiveness. Ideally you should be able to match the first 7-8 letters precisely. I do not need you to upload the corpus, after all it might be into the GB size. I simply would like to know how I can duplicate your work in the event that I would like to take your script for a test-drive. 4. A simple HOWTO (text or Word or PDF) file which helps me understand how to test-drive your program. 5. A report which shows screenshots of your program in execution during the: key-generation (Alice's view) encryption (Alice's view) decryption phase (Bob's view) Eve's view of cryptanalyzing your scheme based on the letter frequency analysis, she runs on the captured large body of ciphertext. The report will give me a more complete view of your understanding of the scheme and what exactly you have done to cryptanalyze it. Please elaborate in full and be as thorough as possible as if you were to show it to a third party observer . 6. You should upload items 1, 2, 4 and 5 on LMS and provide full description of the dataset I need to download if I want to take your script for a test-drive if I so choose. Note: Do not bundle the items into a zip file. Upload all required items individually. This allows me to see them within LMS. I do not want to download a zip file, extract it locally and view, all viewing should occur within the LMS. Special notes: You may utilize a Word document to write up your report and any appropriate screen shots along your steps. This is an individual assignment. Please upload the document as Lastname-Firstname- CUS-1185-substitution-cipher either in Word or PDF format in the proper LMS section along with items 1,2,4,5. Pysso Type here to search 3:38 AM 2/7/2011
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


