Given the following C code file, perform a stack smash on the vuln.c code file using...
Fantastic news! We've Found the answer you've been seeking!
Question:
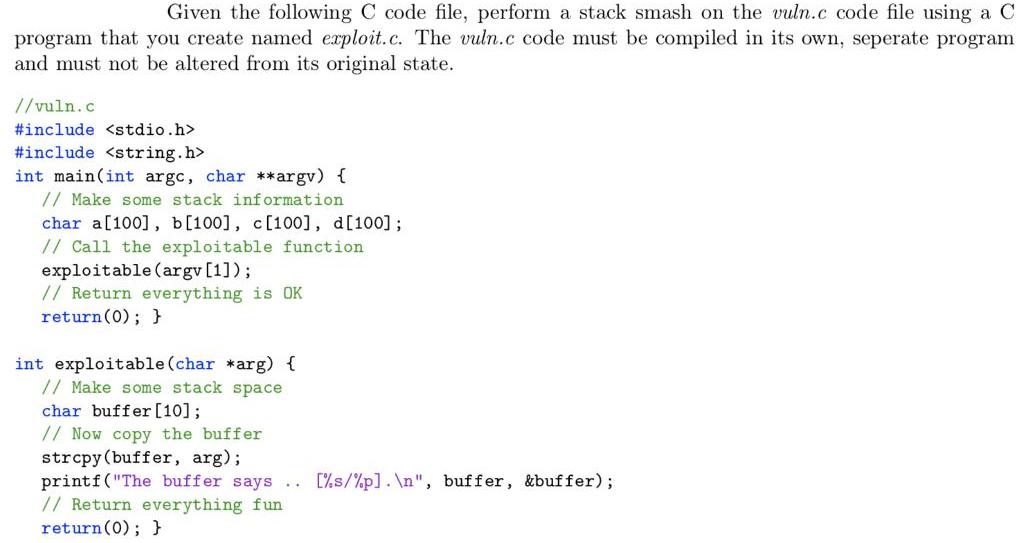
Transcribed Image Text:
Given the following C code file, perform a stack smash on the vuln.c code file using a C program that you create named exploit.c. The vuln.c code must be compiled in its own, seperate program and must not be altered from its original state. //vuln.c #include <stdio.h> #include <string.h> int main(int argc, char **argv) { // Make some stack inf ormation char a[100], b[100], c[100], d[100]; // Call the exploitable function exploitable (argv [1]); // Return everything is OK return(0); } int exploitable(char *arg) { // Make some stack space char buffer[10]; // Now copy the buffer strcpy(buffer, arg); printf("The buffer says .. // Return everything fun return(0); } [%s/%p]. \n", buffer, &buffer); Given the following C code file, perform a stack smash on the vuln.c code file using a C program that you create named exploit.c. The vuln.c code must be compiled in its own, seperate program and must not be altered from its original state. //vuln.c #include <stdio.h> #include <string.h> int main(int argc, char **argv) { // Make some stack inf ormation char a[100], b[100], c[100], d[100]; // Call the exploitable function exploitable (argv [1]); // Return everything is OK return(0); } int exploitable(char *arg) { // Make some stack space char buffer[10]; // Now copy the buffer strcpy(buffer, arg); printf("The buffer says .. // Return everything fun return(0); } [%s/%p]. \n", buffer, &buffer);
Expert Answer:
Answer rating: 100% (QA)
include include int exploitablechar arg int mainint argc char argv ch... View the full answer

Related Book For 

Discrete Mathematics and Its Applications
ISBN: 978-0073383095
7th edition
Authors: Kenneth H. Rosen
Posted Date:
Students also viewed these mathematics questions
-
Lab Exercise -- C++ Structures Objective: The purpose of the program is to: 1. Write functions to read in and print an Employee struct 2. Write an additional function that passes in an array of...
-
A string is pulled aside a distance h at a point 3L/7 from one end. At a point 3L/7 from the other end, the string is pulled aside a distance h in the opposite direction. Discuss the vibrations in...
-
A coil C of N turns is placed around a long solenoid S of radius R and n turns per unit length, as in Figure. (a) Show that the mutual inductance for the coil-solenoid combination is given by M =...
-
Calculate UTX's market value-added (MVA) for each year 2010-2012.
-
Compute a 75% Chebyshev interval centered on the mean.
-
Winner says, It is clear that in decades to come a great many things like telephone answer machines and automatic bank tellers will become, in effect, members of our society. More recent technologies...
-
I spent time with you. It seems that this deed is out of character for you. You were not awarded your normal annual bonus. I would probably feel the same. Is that what happened? You normally wouldnt...
-
Aubrey Inc. issued $4,000,000 of 10%, 10-year convertible bonds on June 1, 2014, at 98 plus accrued interest. The bonds were dated April 1, 2014, with interest payable April 1 and October 1. Bond...
-
Activity 1 Response: Measure the temperature of the environment (ambient temperature), the human body (both forehead and under the tongue), and two other objects in the room. Record this information...
-
Consider the following string of page references 7, 0, 1, 2, 0, 3, 0, 4, 2, 3, 0, 3, 2. Complete a figure similar to Figure 8.14, showing the frame allocation for: a. FIFO (first-in-first-out) b. LRU...
-
Lord Suirdale (Richard Michael John Hely-Hutchinson) sued Brayhead Ltd for losses incurred after a failed takeover deal. The CEO, chairman and de facto managing director of Brayhead Ltd, Mr....
-
Pure A enters an ideal CSTR of volume 10 L at a volumetric flow rate of 10 L/s. Species A undergoes a first-order, liquid-phase reaction inside the reactor. Its conversion under these conditions is...
-
If any individual does not have emotional intelligence, do you believe one can be taught emotional intelligence or practice techniques that will improve their emotional intelligence? Why or why not?...
-
To deal with the rising cost of Medicare, Congressman Lancaster has proposed increasing premiums for higher-income beneficiaries further. What other Medicare reform options have been discussed?...
-
To retire in style takes careful, early planning with an understanding of budgets, taxes, and investments. Identify the first three steps of retirement planning. 1.Define retirement goals....
-
While agencies possess considerable discretion in the rulemaking process, if Congress has not delegated authority to an agency, any action taken by an agency, including rulemaking, will be found...
-
The United States has a dual court system, meaning there are: civil courts and criminal courts. misdemeanor and felony courts. state and federal courts. state and local courts. district courts and...
-
The MIT Sloan School of Management is one of the leading business schools in the U.S. The following table contains the tuition data for the masters program in the Sloan School of Management. a. Use...
-
Suppose that when a long string of text is encrypted using a Vigenre cipher, the same string is found in the ciphertext starting at several different positions. Explain how this information can be...
-
Show that the worst-case complexity in terms of comparisons of an algorithm that finds the maximum and minimum of n elements is at least [3n/2] 2.
-
How many ways are there to arrange the letters a, b, c, and d such that a is not followed immediately by b?
-
Draw Bode plots for a sixth-order Pade approximation to a pure delay of 1 second.
-
A rejection network that can be utilised instead of the twin-T network is the bridged-T network shown below. The transfer function of this network is given by \[...
-
Sketch the polar plot of the frequency response for the following transfer functions: 1 (a) KG(s): = (1+0.5s) (1+2s) (1+0.5s) (b) KG(s) = $2 s+10 (c) KG(s) = s2+6s+10 30(s+8) (d) KG(s) = s(s+2)(s+4)

Study smarter with the SolutionInn App


