On June 27, 2017, a malware infectionNotPetyabegan spreading from Ukraine. It affected firms in many countries, although
Question:
On June 27, 2017, a malware infection—NotPetya—began spreading from Ukraine. It affected firms in many countries, although the greatest impact was in Ukraine. As a result of this malware infection, FedEx acknowledged that this software infection might have a material impact on its operations and financial results.
On June 28, FedEx halted trading of its stock while it assessed the impact of an outbreak of the malware on the network of TNT Express, the recently acquired FedEx subsidiary based in Amsterdam, the Netherlands. The disruption caused by the malware significantly affected communications and operations at TNT Express due to the infiltration of an information system virus. Investors commented that such trading halts were not common among large companies such as FedEx, “unless the news is pretty material to investors/the company.”2 While trading of FedEx stock resumed soon after the temporary halt, the decision to halt trading was significant, with some commenters noting that FedEx might be concerned that the infection could spread and cause more significant disruptions to its global package-delivery operation.3 On July 17, FedEx warned that the impact of NotPetya on its TNT subsidiary would “materially impact” its profits.
FedEx indicated in its form 10-K annual report filing with the US Securities and Exchange Commission (SEC), “Our 2018 results will be negatively affected by our TNT Express integration and restructuring activities, as well as the impact of the TNT Express cyberattack.”4 It continued with other telling statements, indicating that it had:
experienced [a] loss of revenue due to decreased volumes at TNT and incremental costs associated with the implementation of contingency plans and the remediation of affected systems. . . . We cannot yet estimate how long it will take to restore the systems that were impacted, and it is reasonably possible that TNT will be unable to fully restore all of the affected systems and recover all of the critical business data that was encrypted by the virus.
How would these material financial impacts affect FedEx? How could the operational impacts, including the loss of data, impair FedEx’s ability to operate? FedEx has long believed that “the information about a package is as important as the package itself.”5 What more could FedEx have done to prevent this occurrence? Did it do the right things in preparing to ensure that this information was available, uncorrupted, and usable in directing its worldwide operations? What will be the ongoing impact on FedEx’s share price as a result of this cybersecurity incident?
Fedex’s 2016 Acquisition of TNT Express Founded in 1973, FedEx had grown to more than 400,000 employees providing services in more than 220 countries and earning revenue in excess of $60 billion by 2017.6 In May 2016, FedEx acquired TNT Express, B.V. (hereafter “TNT Express”) for $4.9 billion.7 TNT Express’s revenue in 2015 was €6.9 billion. It had operations in 61 countries and delivered parcels to more than 200 countries. It provided both road- and airdelivery services in Europe, the Middle East and Africa, Asia Pacific, and the Americas. A key value proposition of this acquisition was the potential coupling of TNT’s European road network with FedEx’s air network.
FedEx announced that the integration process would begin immediately after the acquisition. The intent was “to leverage investments in technology, infrastructure, facilities and operational capabilities to position the combined companies for long-term growth and success.”8 While customers could continue to interact with each company as they had previously, FedEx announced its intentions to offer customers an integrated global offering, building on the combined expertise of both FedEx and TNT Express.
However, this intent was not without challenges. In its fiscal year 2017 (FY17) earnings guidance, FedEx warned that there was uncertainty about how the integration activities would impact TNT Express’s ongoing business, and how the integration activities would impact TNT Express’s previously announced turnaround strategy.9 By September following the acquisition, FedEx chairman, president, and CEO Frederick Smith reported that the “integration of TNT Express is proceeding smoothly, and the level of team members’ engagement is outstanding.”10 During FY17, 64 countries had fully integrated operations and integration activities had begun across additional countries, including many of the largest operations in TNT’s global network.11 Among the FY17 accomplishments was the implementation of the first phase of cross-scan technology that would enable handling TNT Express packages in the FedEx network and FedEx packages in the TNT Express network, as well as the ability to manage and coordinate inquiries from both FedEx and TNT customers. As part of this integration, FedEx had integrated air operations with TNT Express by connecting the FedEx Express and TNT worldwide networks with a new Boeing 777 flight from the TNT air hub in Liège, Belgium, to the FedEx hub in Memphis. This around-the-world flight would continue onward to Shanghai, China, before returning to Liège.12 Preparing for Cybersecurity Incidents How had FedEx prepared for the kind of cybersecurity incident that it saw unfolding in its business? FedEx made available to its officers, directors, managers, and employees of FedEx and its subsidiaries throughout the world a FedEx Code of Business Conduct and Ethics.13 This code was first adopted in 2003 and updated in September 2016. It is explained that managers were to “anticipate, prevent, and detect compliance risks.” It also went on to require that FedEx resources, including computers, software, and other office equipment, be protected and their efficient and proper use ensured by all.
To implement its corporate governance guidelines,14 FedEx had a Board of Directors consisting of 12 members.
In November 2015, a new member was added to the board—John Inglis, a professor of cybersecurity at the United States Naval Academy and former chief operating officer of the National Security Agency (NSA), who had served as the highest ranking civilian in the NSA.15 The Information Technology Oversight Committee was one of four standing committees within the Board of Directors. During 2016, the charter for this six-member committee was updated with the following charge.
The purpose of the Information Technology Oversight Committee is to:
● Review major information technology (“IT”)-related projects and technology architecture decisions;
● Assess whether the Company’s IT programs effectively support the Company’s business objectives and strategies;
● Assist Board oversight of cybersecurity risks and management efforts to monitor and mitigate those risks;
● Advise the Company’s senior IT management team;
● Advise the Board of Directors on IT-related matters.16 WannaCry and Petya Ransomware WannaCry was the fastest and largest ransomware attack to date.17
This ransomware outbreak affected more than 300,000 computers across 200,000 organizations in more than 150 countries.18 The Petya ransomware was first detected in 2016 and attacked Microsoft Windows-based operating systems.
Like the WannaCry ransomware attack in May 2017, Petya used the EternalBlue exploit that had previously been discovered in older versions of Windows. The EternalBlue exploit had been previously identified, and Microsoft issued patches in March 2017 to shut down the exploit for the latest versions of Windows Vista, Windows 7, Windows 8.1, Windows 10, Windows Server 2008, Windows Server 2012, and Windows Server 2016.
When Petya was unleashed, it infected the master boot record to execute a component of the ransomware that initiated a malicious activity known as a payload that encrypted the master file table of a computer’s hard drive and forced the computer to restart. It then displayed a message to the users that their files were now encrypted and that they needed to send $300 (in Bitcoin) to one of three wallets to receive instructions to decrypt their computer. At the same time, the software exploited the server message block protocol in Windows to infect local computers on the same network and any remote computers it could find. Therefore, it not only infected one machine, but also actively sought out other machines to infect.
WannaCry Cyberattacks in May 2017 WannaCry extortion attacks spread around the globe in May 2017.19 FedEx was one of the organizations affected.
On May 12, FedEx issued a statement indicating that malware was interfering with some of its computers and that remediation steps were being taken. At this point in time, FedEx was unsure if this was related to the global outbreak of the WannaCry malware and whether this was going to cause the company to issue service alerts about potential delays in shipments being delivered.20 NotPetya Cyberattacks in June 2017 On June 27, firms across the globe found themselves again confronted with a new wave of cyberattacks.21 These attacks appeared to target or stem from locations in Ukraine.
Various estimates suggested that between 60% and 80% of the infections were in Ukraine.22 Security experts dubbed the malware used in the Ukraine cyberattacks NotPetya or Nyetna to distinguish it from the original Petya malware. NotPetya encrypted all files on infected computers, not just the master file table. In some cases the computer’s files were completely wiped or rewritten in a manner that could not be undone through decryption.
Security experts believed the attack originated from an update of a Ukrainian tax-accounting package called MeDoc (M.E.Doc) developed by Intellect Service. MeDoc provided periodic updates to its program through an update server. On the day of the attack, June 27, 2017, an update for MeDoc was pushed out by the update server, and the ransomware attacks soon began. It was believed that the software’s automatic update system was compromised and used to download and run malware rather than legitimate updates for the software.
Security company ESET discovered that a back door had been installed on MeDoc’s updater service as early as May 2017, whereas Cisco Systems found evidence of the back door as early as April 2017. Such findings pointed to the cyberattack as a “thoroughly well-planned and well-executed operation.”
While numerous Ukrainian government agencies, companies, and organizations were attacked, non-Ukrainian companies reporting incidents related to the attack—in addition to TNT Express—include food processor Mondelez International, the APM Terminals subsidiary of international shipping company A.P. Moller-Maersk, consumer goods giant Reckitt Benckiser, British advertising agency WPP, pharmaceutical company Merck, Russian oil and gas giant Rosneft, and French construction firm Saint-Gobain.
TNT Struggles to Operate Following the Cyberattack FedEx confirmed that its operations at the TNT subsidiary were impacted by this malware attack, indicating that the attack “involved the spread of an information technology virus through a Ukrainian tax software product.”23 On June 28, a senior vice president at FedEx announced, “Like many other companies worldwide, TNT Express operations have been significantly affected by an information system virus.
No data breach is known to have occurred.” On the same day, FedEx filed a Form 8-K with the SEC indicating that same message but ending with this ominous disclosure: “We cannot measure the financial impact of this service disruption at this time, but it could be material.”24 On July 17, FedEx indicated that customers of its TNT Express subsidiary were still experiencing “widespread”
service and invoicing delays.25 Employees were using manual processes and workarounds due to their systems not being available.26 By August 2017, TNT Express’s deliveries were still disrupted due to the attack.
The Impact Customers were defecting from TNT Express.27 They were being contacted about parcels days after these parcels were due to be delivered. Some customers were waiting 25 days or more for “next day” delivery. They were wondering why they could retrieve FedEx tracking information but not TNT tracking information, and why TNT had not switched over to using the FedEx systems, which seemed to be running.
The Guardian reported that a major TNT hub in the United Kingdom was packed with undelivered parcels, each awaiting manual processing. TNT had to resort to manual processes because its package-tracking data, as well as billing data, were locked in malware-infected encrypted hard drives and not accessible to the firm.
In addition to not being able to estimate (in mid-July) when FedEx would be able to fully restore operations at TNT, the company also acknowledged that the lack of cyberinsurance meant that FedEx might have to bear the full cost of recovery and the financial losses due to the attack.
It stated: We do not have cyber or other insurance in place that covers this attack. Although we cannot currently quantify the amounts, we have experienced loss of revenue due to decreased volumes at TNT and incremental costs associated with the implementation of contingency plans and the remediation of affected systems.
This situation caused FedEx to acknowledge that the NotPetya ransomware attack in late June directly led to both financial and material consequences in its TNT Express subsidiary, which would impact the ability of FedEx to both meet its projections and know whether its financial reporting was accurate.
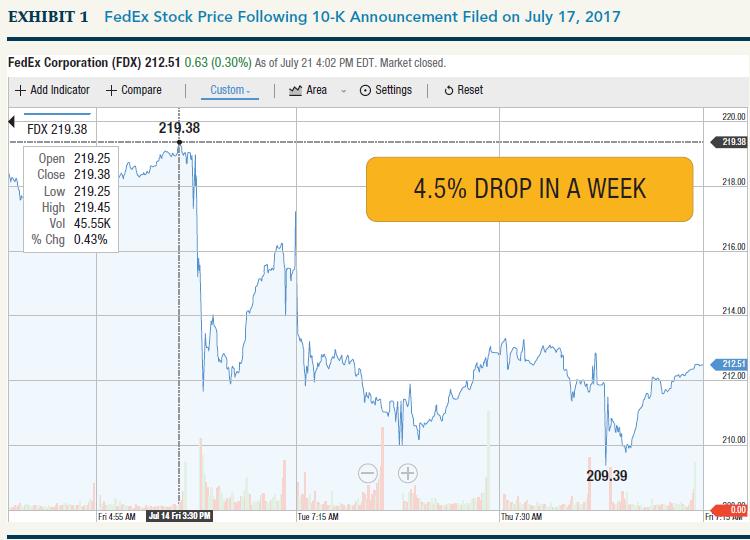
According to a study by Comparitech, stocks generally see a 0.43% drop immediately following a data breach.28 Within a day of the attack, according to Yahoo Finance data, Maersk’s stock had dropped 0.69%, Mondelez International’s 0.93%, and FedEx’s 0.53%. Shown in Exhibit 1, FedEx stock declined 4.5% over the week following the announcement of the NotPetya ransomware.
On September 19, 2017, FedEx reported earnings of $2.19 per diluted share for the quarter ending August 31, 2017.29 These earnings reflected the estimated negative impact of the June 27 cyberattack affecting TNT Express
($0.79 per diluted share) and Hurricane Harvey (only $0.02 per diluted share). In this quarterly filing, FedEx disclosed the following:
The worldwide operations of TNT Express were significantly affected during the first quarter by the June 27 NotPetya cyberattack. Most TNT Express services resumed during the quarter and substantially all TNT Express critical operational systems have been restored.
However, TNT Express volume, revenue, and profit still remain below previous levels. How far below the previous levels was also disclosed by FedEx in its regulatory reporting. First-quarter financial results following the attack showed that operating results for FedEx Express (including TNT Express) declined due to an estimated $300 million impact from the NotPetya cyberattack.
Case Discussion Questions
1. From a resource-based view, an acquisition is supposed to add value. Why did the acquisition of TNT Express reduce so much value for FedEx?
2. Is this cyberattack a black swan event? Or should this have been anticipated?
3. From a postmerger integration standpoint, what are the lessons from this case?
Step by Step Answer:






