Recall Exercise 2.24, that phishing is the term used to describe an attempt to extract personal/financial information
Question:
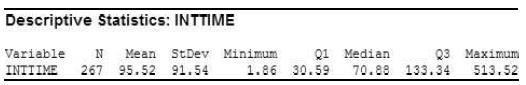
Recall Exercise 2.24, that phishing is the term used to describe an attempt to extract personal/financial information from unsuspecting people through fraudulent email. Data from an actual phishing attack against an organization are provided in the PHISHING file. The company set up a publicized email account—called a “fraud box”—which enabled employees to notify them if they suspected an email phishing attack. The data represent interarrival times, i.e., the difference (in seconds) between the time of the actual phishing attack and the time when an employee notified the company of the attack, for 267 fraud box email notifications. The greater the “typical” interarrival time, the more likely the phishing attack was an “inside job” that originated within the company. Suppose the Technical Support Group at the company, investigating the phishing attack, will classify the attack as an inside job if the typical interarrival time is 80 or more seconds. Descriptive statistics for the interarrival times are shown in the MINITAB printout below. Based on the high mean value of 95.52 seconds, a technical support manager claims the phishing attack is an inside job. Do you agree?
Data from Exercise 2.24
Phishing is the term used to describe an attempt to extract personal/financial information (e.g., PIN numbers, credit card information, bank account numbers) from unsuspecting people through fraudulent email. An article in Chance (Summer, 2007), demonstrates how statistics can help identify phishing attempts and make e-commerce safer. Data from an actual phishing attack against an organization were used to determine whether the attack may have been an “inside job” that originated within the company. The company set up a publicized email account — called a “fraud box” — which enabled employees to notify them if they suspected an email phishing attack. The interarrival times, i.e., the time differences (in seconds), for 267 fraud box email notifications were recorded. Chance showed that if there is minimal or no collaboration or collusion from within the company, the interarrival times would have a frequency distribution similar to the one shown in the accompanying figure. The 267 interarrival times are saved in the PHISHING file.
Step by Step Answer:

Statistics For Engineering And The Sciences
ISBN: 9781498728850
6th Edition
Authors: William M. Mendenhall, Terry L. Sincich





