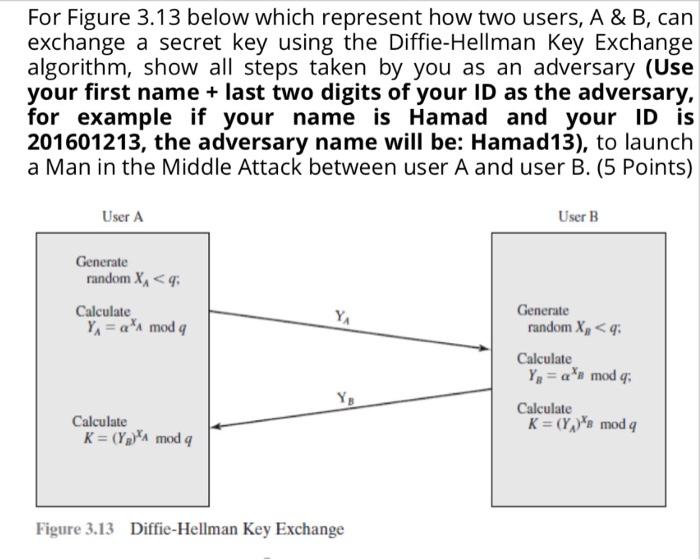
For Figure 3.13 below which represent how two users, A & B, can exchange a secret...
Fantastic news! We've Found the answer you've been seeking!
Question:
Transcribed Image Text:
For Figure 3.13 below which represent how two users, A & B, can exchange a secret key using the Diffie-Hellman Key Exchange algorithm, show all steps taken by you as an adversary (Use your first name + last two digits of your ID as the adversary, for example if your name is Hamad and your ID is 201601213, the adversary name will be: Hamad13), to launch a Man in the Middle Attack between user A and user B. (5 Points) User A Generate random X₁ < q: Calculate Y₁ = a A mod q Calculate K= (Y₂)A mod q YA Figure 3.13 Diffie-Hellman Key Exchange User B Generate random X₂ < q: Calculate Y₁ = an mod q; Calculate K = (Y₂)s mod q For Figure 3.13 below which represent how two users, A & B, can exchange a secret key using the Diffie-Hellman Key Exchange algorithm, show all steps taken by you as an adversary (Use your first name + last two digits of your ID as the adversary, for example if your name is Hamad and your ID is 201601213, the adversary name will be: Hamad13), to launch a Man in the Middle Attack between user A and user B. (5 Points) User A Generate random X₁ < q: Calculate Y₁ = a A mod q Calculate K= (Y₂)A mod q YA Figure 3.13 Diffie-Hellman Key Exchange User B Generate random X₂ < q: Calculate Y₁ = an mod q; Calculate K = (Y₂)s mod q
Expert Answer:
Related Book For 

Posted Date:
Students also viewed these programming questions
-
The Crazy Eddie fraud may appear smaller and gentler than the massive billion-dollar frauds exposed in recent times, such as Bernie Madoffs Ponzi scheme, frauds in the subprime mortgage market, the...
-
Planning is one of the most important management functions in any business. A front office managers first step in planning should involve determine the departments goals. Planning also includes...
-
Given that y = x 2 , find the image of the curve y = x 2 after each of the following combinations of transformations. a. A stretch in the y-direction with factor 3 followed by a translation by the...
-
Gatske A.S .s chart of accounts includes the following selected accounts. 101 .......................Cash 201 Accounts Payable 120 .......................Inventory 332 Cash Dividends 130...
-
This selected information is from recent annual reports of the two largest r etail pharmaceutical companies in the United States. (Dollar amounts are stated in billions.) a. Fill in the missing...
-
If a computer passed the Turing Test, what would that prove? What conditions would you want to be sure had been observed in setting up the test?
-
Stalberg Company's beginning inventory and purchases during the fiscal year ended December 31, 20--, were as follows: There are 10 units of inventory on hand on December 31. 1. Calculate the total...
-
Gallatin County Motors Inc. assembles and sells snowmobile engines. The company began operations on July 1 and operated at 1 0 0 % of capacity during the first month. The following data summarize the...
-
1. Given the facts of the case, what communications do you believe Forrester & Loomis should have made with the audit committee with regard to the transactions with the vendor to comply with PCAOB AS...
-
Table#1: Market Share in U.S. Chocolate Bar Market of Major Chocolate Bar Companies (2020) Company Market Share (% of US Market) Hershey 43.3% Mars 29.8% Lindt/Ghirardilli /R. Stove 9.1% Ferrero*...
-
net; Layer L-1 JE Yj ,(L-1) j,i and neti Yi Layer L (last hidden layer) (1) =-y.8k where &k= f'(netk) (tk - Yk) (L) awl,k Using the gradient descent method, assuming that E = k(yk - tk), then prove...
-
Design a database to automate the intake process for an estate planning attorney. The current process is based on capturing information in the attached form which every client completes....
-
8. Flash memory has some of the properties of ROM (it retains its contents with the power off), and some of the properties of RAM (you can read or write to it). However most types of FLASH memory are...
-
Step 12 Create the following three scenarios using Scenario Manager. The scenarios should change the cells B7, B8, and E6. Good B7 = .0325 B8 = 5 E6 = 275000 Most Likely B7 = .057 B8 = 5 E6312227.32...
-
K The table below contains the total cost (in $) for four average-priced tickets, two beers, four soft drinks, four hot dogs, two game programs, two adult-sized caps, and one parking space for 30...
-
Ten Rings Ltd is a small wholesale business selling premium jewellery boxes. The balance sheet at the end of December 2021 is shown below. (11) (111) (iv) (v) (vi) (vii) (viii) (ix) (xii) Assets...
-
In the operation of an automated production line with storage buffers, what does it mean if a buffer is nearly always empty or nearly always full?
-
The gaseous reaction A B has a unimolecular reaction rate constant of 0.0015 min1 at 80F. This reaction is to be carried out in parallel tubes 10 ft long and 1 in. inside diameter, under a pressure...
-
It is desired to carry out the gaseous reaction A B in an existing tubular reactor consisting of 50 parallel tubes 40 ft long with a 0.75-in. inside diameter. Bench-scale experiments have given the...
-
View the CSB video to list two things in which dust explosions are different from those involving flammable liquids.
-
Using Program16.m(Houbolt method), solve Problem 11.20. Data From Problem 11.20:- The equations of motion of a two-degree-of-freedom system are given by \(2 \ddot{x}_{1}+6 x_{1}-2 x_{2}=5\) and...
-
Using Program16.m(Houbolt method), solve Problem 11.19. Data From Problem 11.19:- Using the central difference method, find the response of the system shown in Fig. 11.2 when \(F_{1}(t)=10 \sin 5 t\)...
-
Using the Wilson method with \(\theta=1.4\), solve Problem 11.18. Data From Problem 11.18:- Using the central difference method, find the response of the two-degree-of-freedom system shown in Fig....

Study smarter with the SolutionInn App



