Question: b) The figure 1 shows communication between Ani and Baba. Both Ani and Baba require an authenticated and secret communications from the eavesdropper. Demonstrate

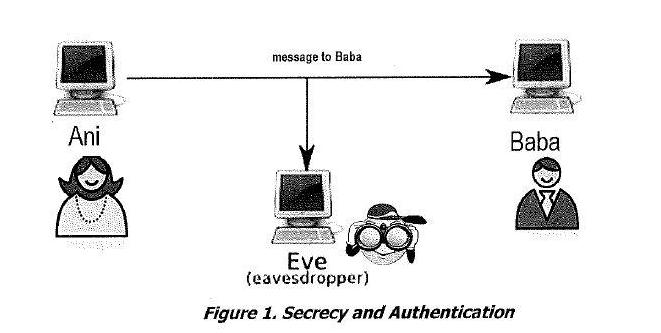
b) The figure 1 shows communication between Ani and Baba. Both Ani and Baba require an authenticated and secret communications from the eavesdropper. Demonstrate how the authentication and secrecy can be achieved using the encryption method. Ani message to Baba Eve (eavesdropper) Figure 1. Secrecy and Authentication Baba
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


