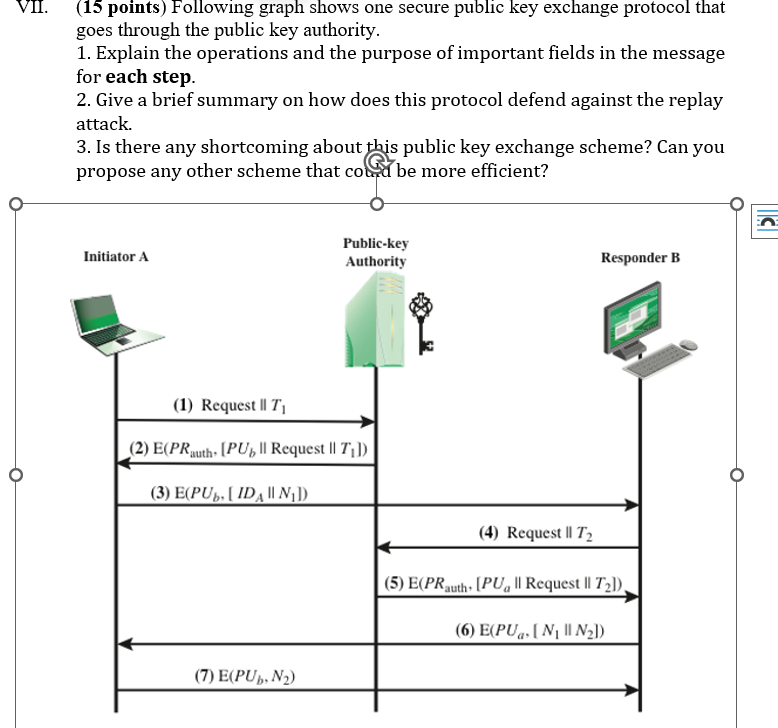
Question: VII. ( 1 5 points ) Following graph shows one secure public key exchange protocol that goes through the public key authority. Explain the operations
VII. points Following graph shows one secure public key exchange protocol that
goes through the public key authority.
Explain the operations and the purpose of important fields in the message
for each step.
Give a brief summary on how does this protocol defend against the replay
attack.
Is there any shortcoming about this public key exchange scheme? Can you
propose any other scheme that co Ge more efficient?
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


