Question: Given the protection state shown in Figure and the rules shown in Figure, do the following. a. Explain how S3 can cause the protection state
Given the protection state shown in Figure and the rules shown in Figure, do the following.
a. Explain how S3 can cause the protection state to be changed so that it has write access to F2.
b. Specify two different ways by which S3 can obtain read permission to F1.
c. Explain whether S3 can obtain seek permission to D1 from S1. Why or why not?
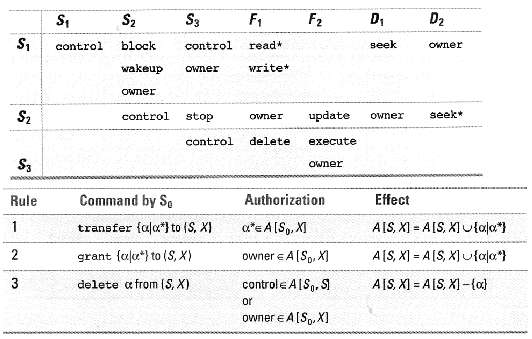
S, S, S2 S3 D2 F1 F2 D, block seek control control read* Owner write* wakeup Owner OWner S2 seek* update control stop owner Owner control delete execute S3 Owner Command by So Authorization Effect Rule AIS, XI = A[S, XI Uala*) 1 transfer {ala*) to (S, X) a*e A[Sp, XI A[S, X] = A[S, X) ufala*} owner e A[Sp, X] grant {alu*} to (S, X) controle AIS,, SI AIS, XI = A[S, XI -{a} delete a from (S, X) or owner e A[S,. X]
Step by Step Solution
3.39 Rating (155 Votes )
There are 3 Steps involved in it
Here is a solution a S 3 has owner to F 2 so S 3 can grant write to itself be... View full answer

Get step-by-step solutions from verified subject matter experts
Document Format (1 attachment)
34-E-CE-OS (544).docx
120 KBs Word File


