Question: Alice is using the public-key authentication protocol of Fig. 8-43 to authenticate communication with Bob. However, when sending message 7, Alice forgot to encrypt R
Figure 8-43
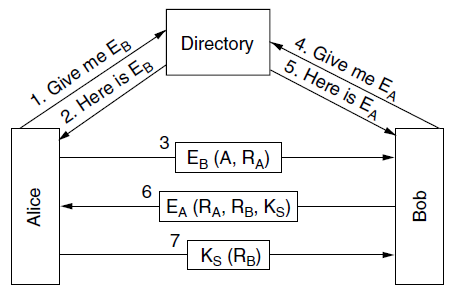
4. Give me EA 1. Give me EB 2. Here is ER Directory 5. Here is EA (, RA) 6 Ea (R, R, Ks) Ks (RB) Alice Bob
Step by Step Solution
3.47 Rating (157 Votes )
There are 3 Steps involved in it
Even if Trudy intercepted the message including R B she ... View full answer

Get step-by-step solutions from verified subject matter experts


