Question: Consider our authentication protocol in Figure 8.18 in which Alice authenticates herself to Bob, which we saw works well (i.e., we found no flaws in
Figure 8.18
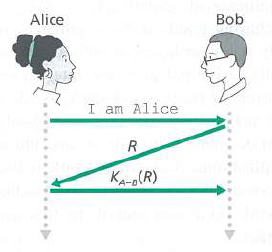
Alice Bob I am Alice KA-e(R)
Step by Step Solution
3.33 Rating (165 Votes )
There are 3 Steps involved in it
Bob does not know if he is talking to Trudy or Alice initially Bob and Alice share a secret key K AB ... View full answer

Get step-by-step solutions from verified subject matter experts


