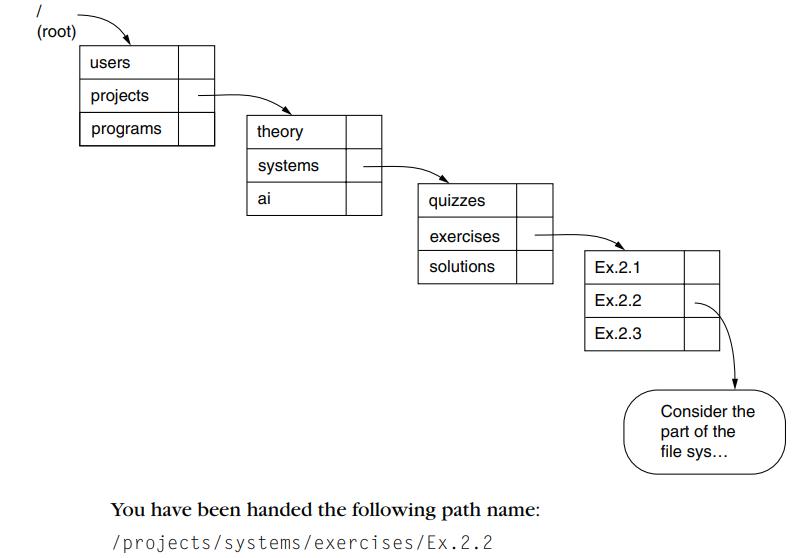
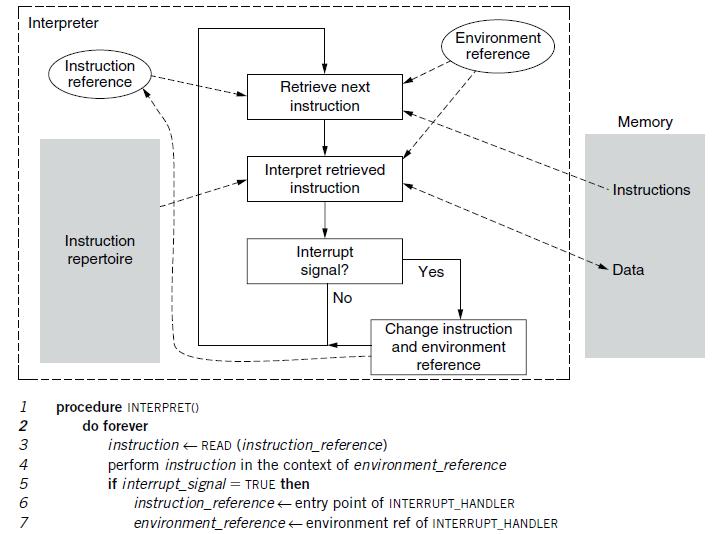
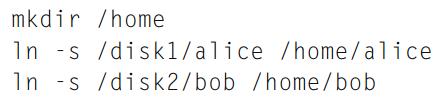
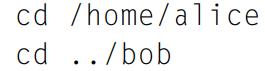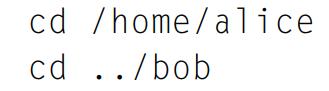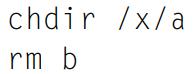Principles Of Computer System Design An Introduction 1st Edition Jerome H. Saltzer, M. Frans Kaashoek - Solutions
Explore comprehensive solutions and in-depth answers to the questions from "Principles Of Computer System Design: An Introduction" by Jerome H. Saltzer and M. Frans Kaashoek. Our online resource offers a detailed answers key and solution manual, featuring step-by-step answers for every chapter. Access solved problems and test bank materials to enhance your understanding of the textbook. Whether you're seeking chapter solutions or an instructor manual, our solutions PDF covers it all. Enjoy the convenience of free download options to ensure you have the essential answers and guidance needed for your studies and academic success.
![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()