In addition to providing a standard for public-key certificate formats, X.509 specifies an authentication protocol.The original version
Question:
In addition to providing a standard for public-key certificate formats, X.509 specifies an authentication protocol.The original version of X.509 contains a security flaw.The essence of the protocol is as follows.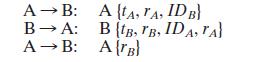
where tA and are timestamps, rA and rB are nonces and the notation indicates that the message Y is transmitted, encrypted, and signed by X.
The text of X.509 states that checking timestamps tA and tB is optional for three-way authentication. But consider the following example: Suppose A and B have used the preceding protocol on some previous occasion, and that opponent C has intercepted the preceding three messages. In addition, suppose that timestamps are not used and are all set to 0. Finally, suppose C wishes to impersonate A to B. C initially sends the first captured message to B:![]()
B responds, thinking it is talking to A but is actually talking to C:![]()
C meanwhile causes A to initiate authentication with C by some means. As a result,A sends C the following:![]()
C responds to A using the same nonce provided to C by B:![]()
A responds with![]()
This is exactly what C needs to convince B that it is talking to A, so C now repeats the incoming message back out to B.![]()
So B will believe it is talking to A whereas it is actually talking to C. Suggest a simple solution to this problem that does not involve the use of timestamps.
Step by Step Answer:






