Question: When using the DES algorithm for decryption, the 16 keys (left(K_{1}, K_{2}, ldots, K_{16}ight)) are used in reverse order. Therefore, the right-hand side of Figure
When using the DES algorithm for decryption, the 16 keys \(\left(K_{1}, K_{2}, \ldots, K_{16}ight)\) are used in reverse order. Therefore, the right-hand side of Figure 3.5 is not valid for decryption. Design a key-generation scheme with the appropriate shift schedule (analogous to Table 3.4d) for the decryption process.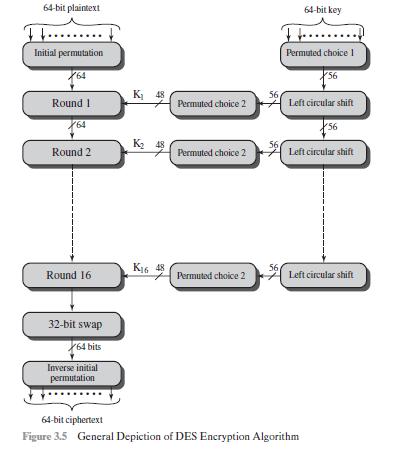
64-bit plaintext Initial permutation 764 Round 1 64 Round 2 Round 16 32-bit swap 64 bits Inverse initial permutation K 48 K 48 K16 48 Permuted choice 2 Permuted choice 2 Permuted choice 2 56 56 56 64-bit key Permuted choice 1 56 Left circular shift 64-bit ciphertext Figure 3.5 General Depiction of DES Encryption Algorithm X56 Left circular shift Left circular shift
Step by Step Solution
3.31 Rating (154 Votes )
There are 3 Steps involved in it
Round number 1 2 Bi... View full answer

Get step-by-step solutions from verified subject matter experts


