Question: Exhibit 12.1 lists common techniques used to commit cybercrimes. For each of these techniques, research the Internet and provide the names of one or two
Exhibit 12.1 lists common techniques used to commit cybercrimes. For each of these techniques, research the Internet and provide the names of one or two entities that have been impacted by such technique in the last 5–7 years. Briefly describe how the technique was used in the attack.
Exhibit 12.1
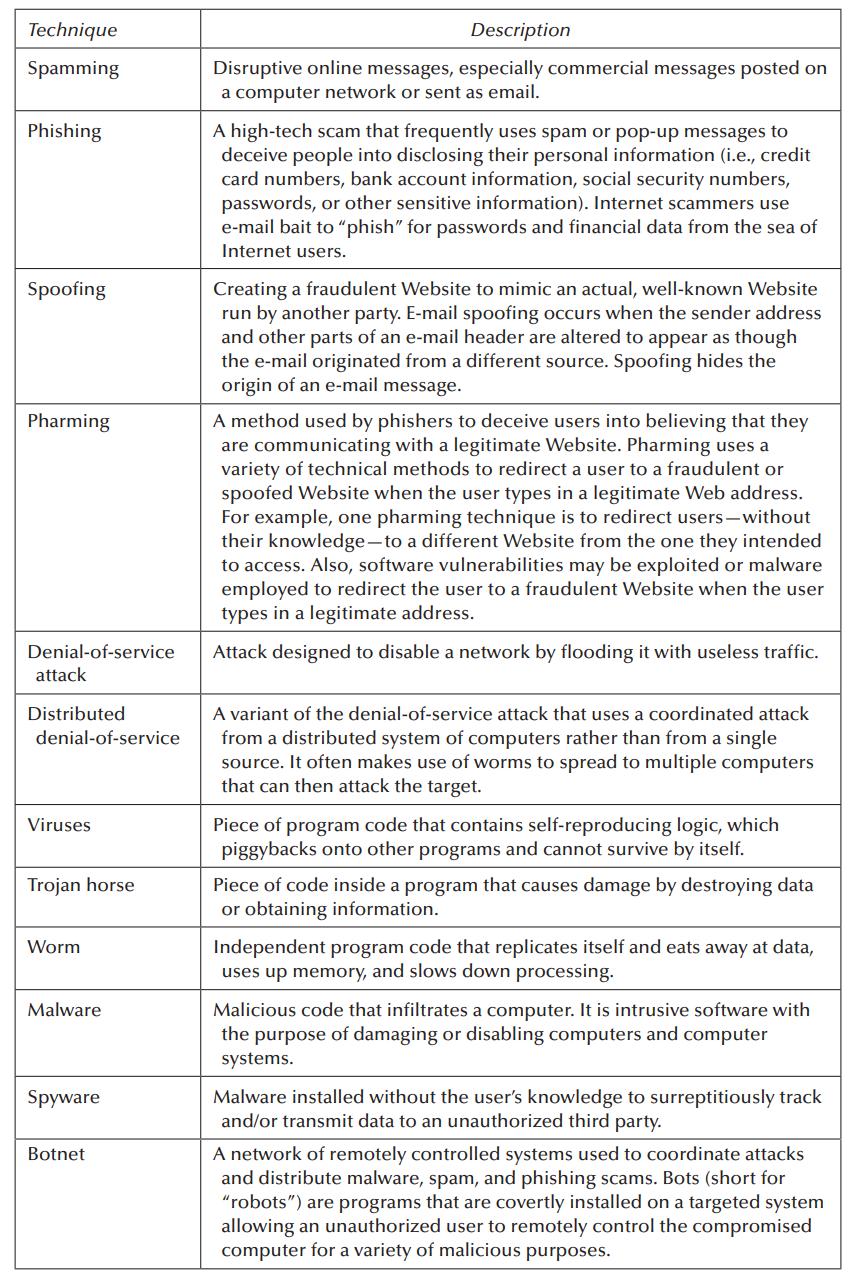
Technique Spamming Phishing Spoofing Pharming Denial-of-service attack Distributed denial-of-service Viruses Trojan horse Worm Malware Spyware Botnet Description Disruptive online messages, especially commercial messages posted on a computer network or sent as email. A high-tech scam that frequently uses spam or pop-up messages to deceive people into disclosing their personal information (i.e., credit card numbers, bank account information, social security numbers, passwords, or other sensitive information). Internet scammers use e-mail bait to "phish" for passwords and financial data from the sea of Internet users. Creating a fraudulent Website to mimic an actual, well-known Website run by another party. E-mail spoofing occurs when the sender address and other parts of an e-mail header are altered to appear as though the e-mail originated from a different source. Spoofing hides the origin of an e-mail message. A method used by phishers to deceive users into believing that they are communicating with a legitimate Website. Pharming uses a variety of technical methods to redirect a user to a fraudulent or spoofed Website when the user types in a legitimate Web address. For example, one pharming technique is to redirect users - without their knowledge-to a different Website from the one they intended to access. Also, software vulnerabilities may be exploited or malware employed to redirect the user to a fraudulent Website when the user types in a legitimate address. Attack designed to disable a network by flooding it with useless traffic. A variant of the denial-of-service attack that uses a coordinated attack from a distributed system of computers rather than from a single source. It often makes use of worms to spread to multiple computers that can then attack the target. Piece of program code that contains self-reproducing logic, which piggybacks onto other programs and cannot survive by itself. Piece of code inside a program that causes damage by destroying data or obtaining information. Independent program code that replicates itself and eats away at data, uses up memory, and slows down processing. Malicious code that infiltrates a computer. It is intrusive software with the purpose of damaging or disabling computers and computer systems. Malware installed without the user's knowledge to surreptitiously track and/or transmit data to an unauthorized third party. A network of remotely controlled systems used to coordinate attacks and distribute malware, spam, and phishing scams. Bots (short for "robots") are programs that are covertly installed on a targeted system allowing an unauthorized user to remotely control the compromised computer for a variety of malicious purposes.
Step by Step Solution
3.32 Rating (158 Votes )
There are 3 Steps involved in it
Certainly here are examples of entities impacted by the listed cybercrime techniques in the last 57 years 1 Spamming In 2016 the University of Calgary in Canada fell victim to a spam attack where the ... View full answer

Get step-by-step solutions from verified subject matter experts


