Question: A linear permutation i (i + m) modn is used as shown in Figure 16.13. Does the encryption depend on the value of m ?
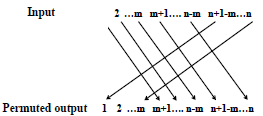
Input 2.m m+l.. n-m n+l-m...n 1 2 ..m m+1.. n-m n+l-m...n Permuted output
Step by Step Solution
3.54 Rating (161 Votes )
There are 3 Steps involved in it
The encryption depends on the value of m since it decides ... View full answer

Get step-by-step solutions from verified subject matter experts


