Question: 5. Consider the following protocol for Authentication/Key Distribution: (X and Y are two principals, A is a Certificate Authority or a Key Distribution Center, RX
5. Consider the following protocol for Authentication/Key Distribution: (X and Y are two principals, A is a Certificate Authority or a Key Distribution Center, RX is a randon number, and EX means encrypted with the secret key of X.)
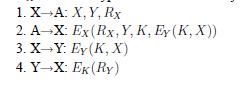
![]()
(a) What does the presence of RX in message 2 assure?
(b) What problem will be created if an attacker were to break an old K (and the attacker has also copied messages for that session)? Explain your answer.
(c) Suggest a method to solve this problem?
1.XA: X.Y, Ry 2. A-X: Ex(Rx, Y, K, Ey (K, X)) 3. XY: Ey (K, X) 4. YX: E(RY)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


