Use Table 2.6 to conduct a security self-assessment. Identify specific follow-up actions you need to take. Data
Question:
Use Table 2.6 to conduct a security self-assessment. Identify specific follow-up actions you need to take.
Data in Table 2.6
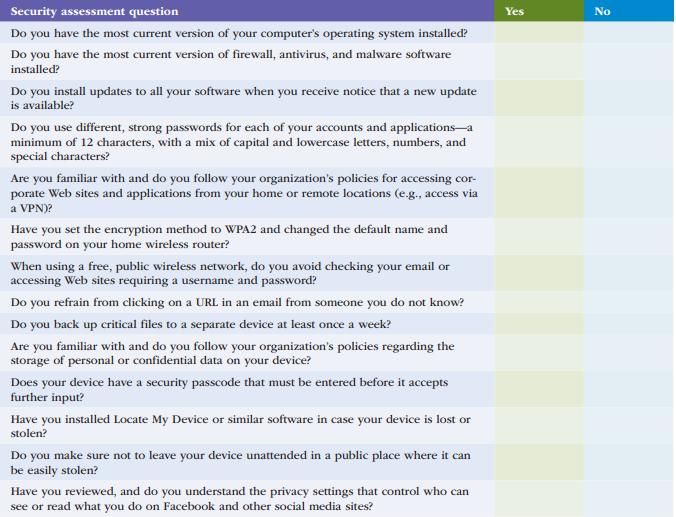
Transcribed Image Text:
Security assessment question Do you have the most current version of your computer's operating system installed? Do you have the most current version of firewall, antivirus, and malware software installed? Do you install updates to all your software when you receive notice that a new update is available? Do you use different, strong passwords for each of your accounts and applications-a minimum of 12 characters, with a mix of capital and lowercase letters, numbers, and special characters? Are you familiar with and do you follow your organization's policies for accessing cor- porate Web sites and applications from your home or remote locations (e.g., access via a VPN)? Have you set the encryption method to WPA2 and changed the default name and password on your home wireless router? When using a free, public wireless network, do you avoid checking your email or accessing Web sites requiring a username and password? Do you refrain from clicking on a URL in an email from someone you do not know? Do you back up critical files to a separate device at least once a week? Are you familiar with and do you follow your organization's policies regarding the storage of personal or confidential data on your device? Does your device have a security passcode that must be entered before it accepts further input? Have you installed Locate My Device or similar software in case your device is lost or stolen? Do you make sure not to leave your device unattended in a public place where it can be easily stolen? Have you reviewed, and do you understand the privacy settings that control who can see or read what you do on Facebook and other social media sites? Yes No
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 54% (11 reviews)
Table 26 Security SelfAssessment Security Domain Assessment FollowUp Actions Access Control Limited access to authorized ...View the full answer

Answered By

Monette Taban
I am currently studying Computer Science Engineering, Due to my interest in programming languages and coding, I am interesetd on Technology so I search about it read about different types of technologies, I think my this habbis will help me to solve problems of students and that is why I am signing as a question answer expert.
0.00
0 Reviews
10+ Question Solved
Related Book For 

Principles Of Information Systems
ISBN: 9780357112410
14th Edition
Authors: Ralph Stair, George Reynolds
Question Posted:
Students also viewed these Computer science questions
-
List three specific parts of the Case Guide, Objectives and Strategy Section (See below) that you had the most difficulty understanding. Describe your current understanding of these parts. Provide...
-
Planning is one of the most important management functions in any business. A front office managers first step in planning should involve determine the departments goals. Planning also includes...
-
Case Study: Quick Fix Dental Practice Technology requirements Application must be built using Visual Studio 2019 or Visual Studio 2017, professional or enterprise. The community edition is not...
-
Ski Aus is a company that makes fashionable, high performance and expensive ski clothing (ski wear). Ski Aus has traditionally segmented the market by clothing type (e.g., ski pants, ski jackets,...
-
A real estate agent wants to know how many owners of homes worth over $1,000,000 might be considering putting their home on the market in the next 12 months. He surveys 40 of them and finds that 10...
-
Analyze the Trivago s search engine marketing strategy ( search engine optimization and paid search marketing ).
-
With reference to the preceding exercise, for which temperature is the probability 0.05 that it will be exceeded during one day? Data From Preceding Exercise Determining a joint cumulative...
-
Juras Inc. and Hinson Inc. have the following operating data: a. Compute the operating leverage for Juras Inc. and Hinson Inc. b. How much would income from operations increase for each company if...
-
Question 1. From the research for this terms Crisis Management Team Assignment - Taylor swift and Ticket Master Crisis a. Explaining, with some detail, three (3) specific things that the leader(s) in...
-
You are going to perform a security risk assessment for your small company. What steps must be taken?
-
Discuss how the CIS security triad can be implemented at the organizational level to safeguard against cyberattacks.
-
In general it appears that environmental groups favor standards over market-based solutions to pollution. Do you think this preference is based on pragmatic considerations or the belief that, in...
-
Why is Haumea an oblate spheroid? a. Because it is not big enough to be a regular sphere. b. Because it has a very large crater c. Because it spins rapidly. d. Because of tidal forces from one of its...
-
When you throw an object into the air, is its return speed just before hitting your hand the same as its initial speed? (Neglect air resistance.) Explain by applying the conservation of mechanical...
-
As an object approaches a converging lens from beyond the focal point, its image O a decreases in size. Ob. increases in size. O c. stays the same size. O d. decreases in size to a point and then...
-
state whether the statements below are true or false and explain why. even in the case that the explanation is a formula, please explain what the formula is saying (what the symbols mean etc...) A....
-
In a collision, the total _________ is always the same before and after. kinetic energy internal energy linear momentum elastic potential energy
-
How do elevation (on mountains) and depth (in water) affect environmental conditions and life-forms?
-
List four items of financial information you consider to be important to a manager of a business that has been operating for a year.
-
What is a knowledge repository?
-
Identify the basic components of an expert sys- tem and describe the role of each.
-
Describe the roles of the domain expert, the knowledge engineer, and the knowledge user in expert systems.
-
The correlation between equity and bonds is 0.2. If the standard deviation of equity returns is 15% and the standard deviation of bond returns is 5%, what is the covariance between equity and bonds?
-
Consider the specific-factors model, where the economy produces an agricultural good with land and labour and a manufactured good with capital and labour. The production process features diminishing...
-
Show graphically why the problem of outsourcing production to China, Mexico, and elsewhere is a good move economically for many companies. (consider isoquant and isocosts maps for the USA and for...

Study smarter with the SolutionInn App


