Question: 05B - Summarize Cryptographic Modes of Operation Performance-based Question Instructions Carefully review the sentences within the message verification process, then use the dropdown selectors
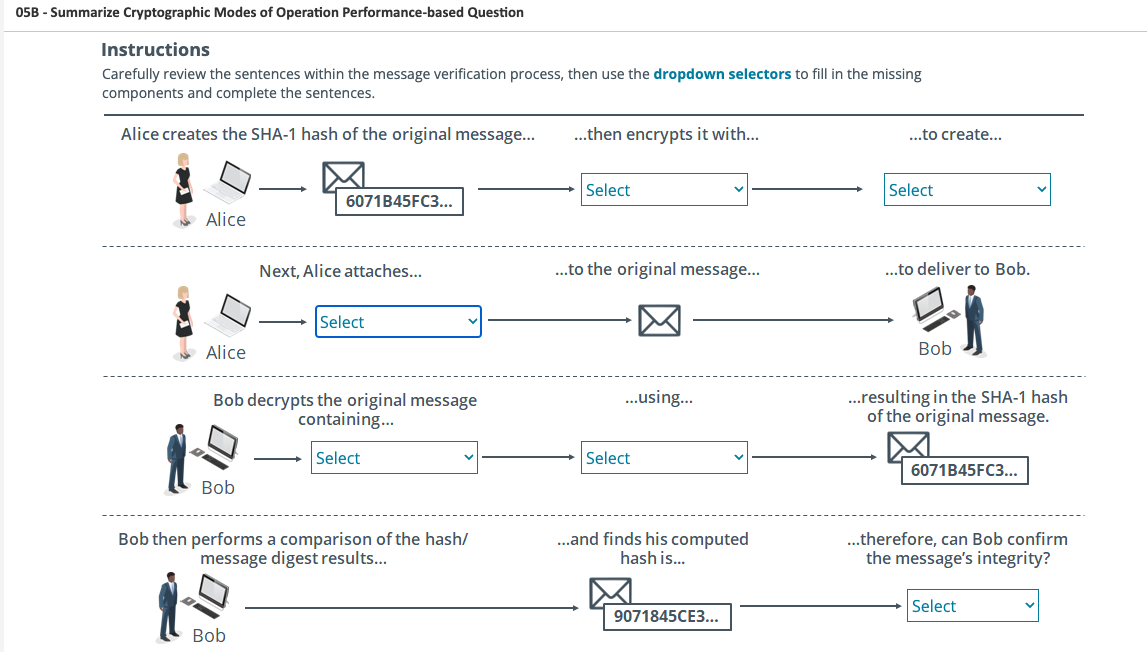
05B - Summarize Cryptographic Modes of Operation Performance-based Question Instructions Carefully review the sentences within the message verification process, then use the dropdown selectors to fill in the missing components and complete the sentences. Alice creates the SHA-1 hash of the original message... Alice Alice Bob 6071B45FC3... Next, Alice attaches... Bob decrypts the original message containing... Select Bob Select Bob then performs a comparison of the hash/ message digest results... ..then encrypts it with... Select ...to the original message... ...using... Select ...and finds his computed hash is... 9071845CE3... ...to create... Select ...to deliver to Bob. Bob ...resulting in the SHA-1 hash of the original message. 6071B45FC3... ...therefore, can Bob confirm the message's integrity? Select
Step by Step Solution
There are 3 Steps involved in it
To correctly complete this question on summarizing cryptographic modes of operation follow the process of encrypting hashing and verifying the message... View full answer

Get step-by-step solutions from verified subject matter experts


