Question: 1 2 3 4, All are true about policy development except a. Policies must be balanced with performance b. Policy must be developed when new
 1
1
2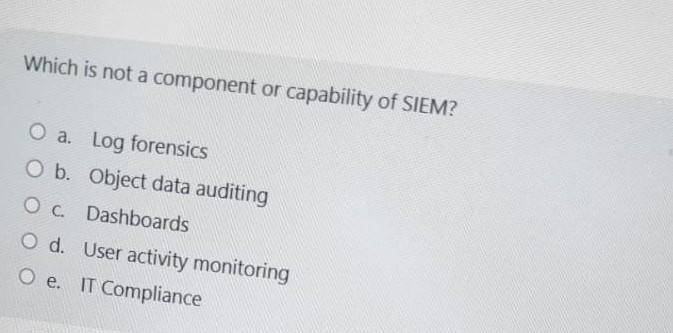
3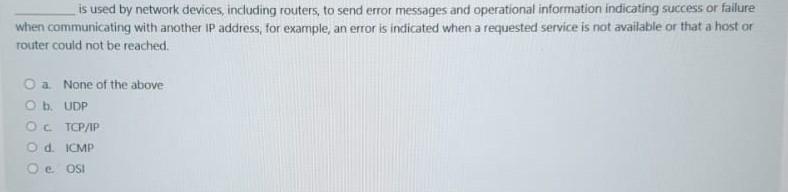
4,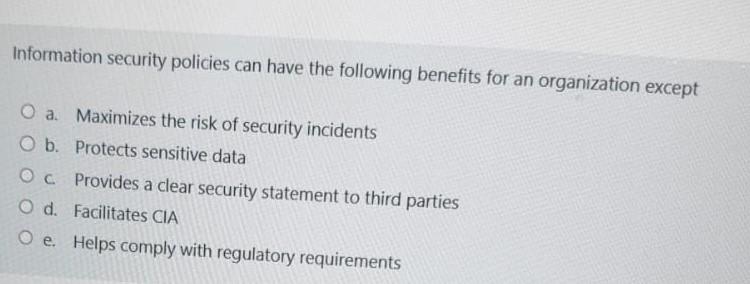
All are true about policy development except a. Policies must be balanced with performance b. Policy must be developed when new data, asset, or services are available c. Before policies are developed, a set of procedures must be defined d. All of the above e. None of the above Which is not a component or capability of SIEM? a. log forensics b. Object data auditing c. Dashboards d. User activity monitoring e. IT Compliance is used by network devices, including routers, to send error messages and operational information indicating success or failure when communicating with another IP address, for example, an error is indicated when a requested service is not available or that a host or touter could not be reached. a. None of the above b. UDP c. TCP/P d. ICMP e. OSi Information security policies can have the following benefits for an organization except a. Maximizes the risk of security incidents b. Protects sensitive data c. Provides a clear security statement to third parties d. Facilitates CIA e. Helps comply with regulatory requirements
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


