Question: 1. Consider a raw CBC MAC construction such as the one beloww raw CBC m[0] m(3] F(k, ) F(k,) F(k,) F(k,) SL L Let F:
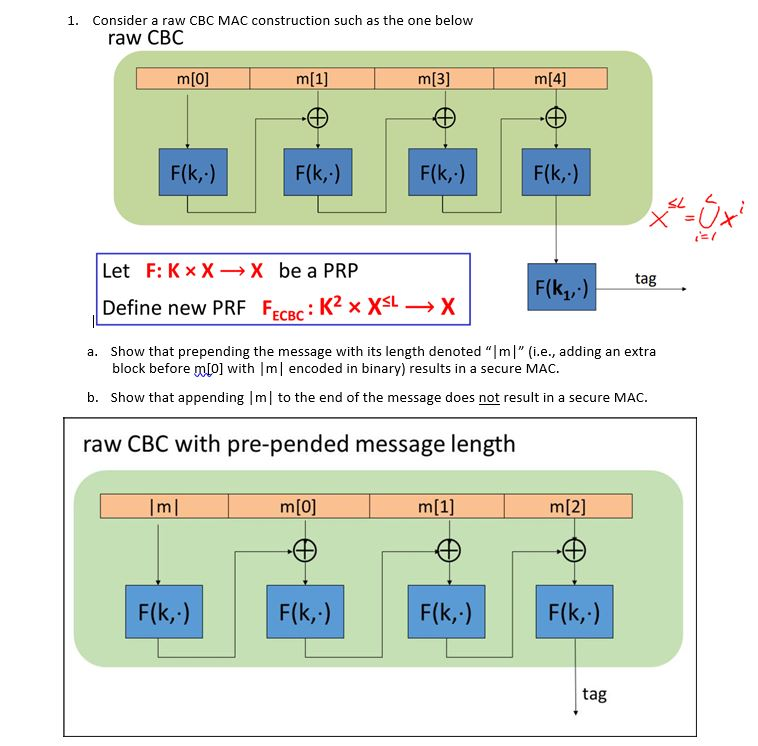
1. Consider a raw CBC MAC construction such as the one beloww raw CBC m[0] m(3] F(k, ) F(k,) F(k,) F(k,) SL L Let F: Kx XX be a PRP tag Define new PRF FECBc: K2 x 1/ a. Show that prepending the message with its length denoted "Im" (i.e., adding an extra b. Show that appending |ml to the end of the message does not result in a secure MAC. raw CBC with pre-pended message length block before mlO] with ml encoded in binary) results in a secure MAC. mo m[2) F(k,) F(k,) F(k,) tag 1. Consider a raw CBC MAC construction such as the one beloww raw CBC m[0] m(3] F(k, ) F(k,) F(k,) F(k,) SL L Let F: Kx XX be a PRP tag Define new PRF FECBc: K2 x 1/ a. Show that prepending the message with its length denoted "Im" (i.e., adding an extra b. Show that appending |ml to the end of the message does not result in a secure MAC. raw CBC with pre-pended message length block before mlO] with ml encoded in binary) results in a secure MAC. mo m[2) F(k,) F(k,) F(k,) tag
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


