Question: 1 . Identify and explain 3 network security problems and 3 infrastructure design problems with company B 2 . Discuss the risks, likelihood and impact
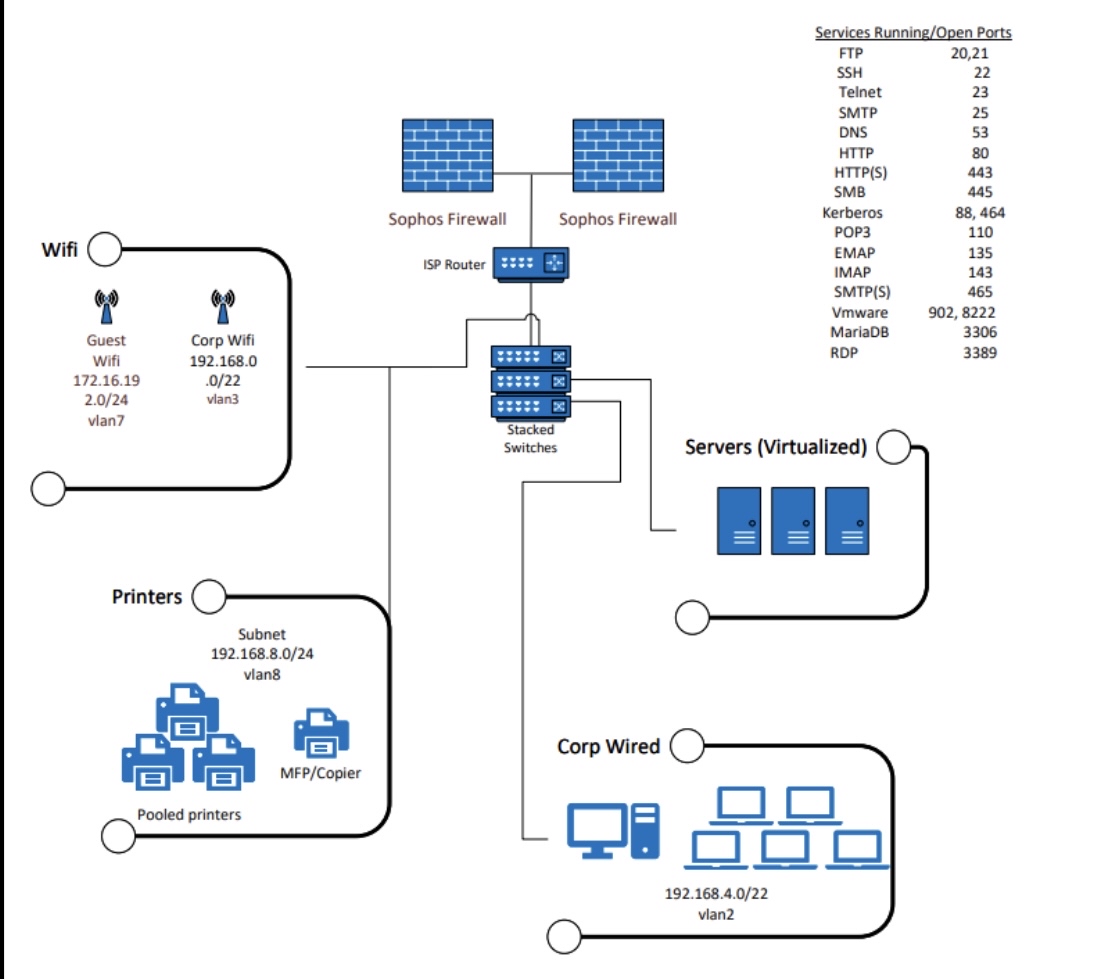
Identify and explain network security problems and infrastructure design problems with company B Discuss the risks, likelihood and impact associated with of the network security and infrastructure design problems identified in company BCompany B performed this vulnerability assessment in anticipation of system integration with Company AThis assessment was performed by a qualified thirdparty assessor, and this report has been generated with the results. This assessment was performed in accordance with a methodology described in NIST Rev to identify the following: Vulnerabilities using the CVSS model Severity Likelihood of occurrenceTable A Risk ClassificationsRisk LevelDescriptionHighThe loss of confidentiality, integrity, or availability may be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.ModerateThe loss of confidentiality, integrity, or availability may be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.LowThe loss of confidentiality, integrity, or availability may be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.Table B SeveritySeverity LevelCVSS ModelDescriptionCritical Exploitation of the vulnerability likely results in rootlevel compromise of servers or infrastructure devices. Exploitation is usually straightforward in the sense that the attacker does not need any special authentication credentials or knowledge about individual victims and does not need to persuade a target user, for example, via social engineering, to perform any special functions.High The vulnerability is difficult to exploit. Exploitation could result in elevated privileges. Exploitation could result in significant data loss or downtime.Medium Vulnerabilities that require the attacker to manipulate individual victims via social engineering tactics. Denial of service vulnerabilities that are difficult to set up Exploits that require an attacker to reside on the same local network as the victim. Vulnerabilities where exploitation provides only very limited access. Vulnerabilities that require user privileges for successful exploitation.LowExploitation of such vulnerabilities usually requires local or physical system access and would have little impact on the organization.Table C Level of EffortLevel of EffortDescriptionHighThis requires a high level of dedicated effort from one or more teams on critical systems, including patching, multiple configuration changes, or highly technical changes that risk bringing services down.ModerateThis is a mediumlevel effort that requires substantial dedication from a partial or entire team. This could impact services or cause a partial outage.LowThese are individual or small team efforts generally requiring a minimal time commitment and require running an update or remedial command or series of commands that will not impact production services.Table D System InventorySystem ComponentsServersVirtualized farm running on HyperV hosts Windows Server and Ubuntu Linux. Approximately virtualized servers across the hosts including the following roles: Ubuntu Linux FTP server for EDI Incoming Operations x Domain Controllers used for M identity syncx File StorageServer x Ruby On Rails server x ElasticSearch servers clusterx web application servers Ubuntu Linux cluster, x PostGRESQL, x MariaDB SQLx running nginX Plus wreverse caching proxy, x running Apache Tomcat, PHP hosting SSLTLS certificatesx Remote Desktop Servers for internal sharedapplications x legacy Exchange servers postmigration WorkstationsWindows XP Pro, Ubuntu Linux, MacOSSwitchesHPE JLA Aruba F G PoEFirewallx Sophos XG firewallsBorder routerVerizon FIOS router CRALaptopsWindows Ubuntu LTS MacOS Ventura Monterey, Big SurWireless Access Pointsx HPE JZA Aruba APCable plantCataTable E Risk IdentificationRisk #VulnerabilityNVT NameNVT OIDSeverityRiskLevel of EffortDistributed Ruby dRubyDRb Multiple Remote Code Execution VulnerabilitiesCriticalHighHighMFA not enforced across all usersHighHighHighRexec service is runningHighHighLowAll users have local administrative privilegesMediumModerateHighJava RMI Server Insecure Default Configuration Remote Code Execution Vulnerability on publiclyfacing serverCriticalHighModerateOperating System OS End of Life EOL DetectionCriticalHighLowrlogin Passwordless LoginHighModerateLowApache Tomcat AJP RCE Vulnerability GhostcatCriticalHighModeratePostgreSQL weak passwordHighHighLowPostgreSQL admin is reachable from internetCriticalHighLowVNC Brute Force LoginHighHighLowFTP Brute Force Logins ReportingHighHighLowphpinfo output ReportingHighModerateLowvsftpd Compromised Source Packages Backdoor VulnerabilityHighHighModeratersh Unencrypted Cleartext LoginHighModerateModerateSSLTLS: OpenSSL CCS Man in the Middle Security Bypass VulnerabilityHighModerateModerateAnonymous FTP Login ReportingModerateLowSamba MSRPC Remote Shell Command Execution Vulnerability Active CheckHighModerateHighSSLTLS: Deprecated SSLv and SSLv Protocol DetectionModerateModerateModerateWeak Host Key AlgorithmsSSHModerateModerateModerateCompany B Cyber Security ToolsCompany B has provided this list of cyber security tools in anticipation of being acquired by Company AThis list is assumed to be complete.Table A Cyber Security ToolsTool NamePurposeSophosIntercept XEndpoint Detection and ResponseOneTrustData privacyData lifecycle managementCodeDatacentric securitySophos XGNextGen FirewallsNo tool availableMobile Device & Application ManagementDUOIdentity and Access ManagementAkamaiApplication SecurityMimecastMessaging SecurityArctic WolfManaged Security Services ProviderCisco UmbrellaDNS SecurityIn progressCyber security policyIn progressWritten Information Security Policy WISPIn progressWritten proceduresMinimalDocumentation of environment
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


