Question: 1. Identify the functional dependencies in the table above. 2. Using the functional dependencies identified in #1, use the attribute closure method to identify

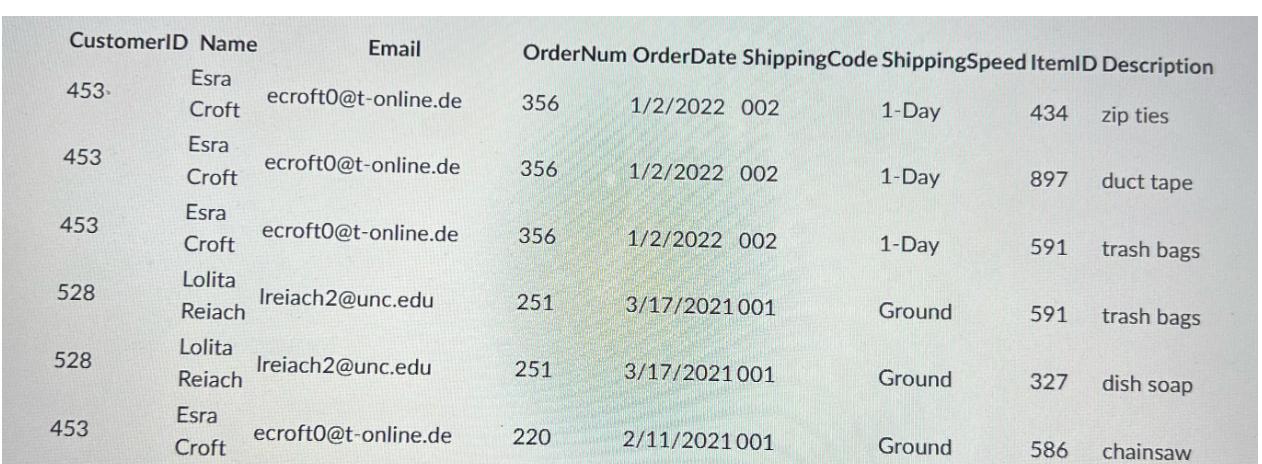
1. Identify the functional dependencies in the table above. 2. Using the functional dependencies identified in #1, use the attribute closure method to identify the candidate keys of the table above. 3. From the candidate keys identified in #2, what is the primary key of the table? 4. Show the following normal forms for the table above: a. First Normal Form. Show all data. b. Second Normal Form. Just the names of the columns for each reorganized table, with the primary key underlined is sufficient. c. Third Normal Form. Just the names of the columns for each reorganized table, with the primary key underlined is sufficient. CustomerID Name Esra Croft 453- 453 453 528 528 453 Esra Croft Esra Croft Lolita Reiach Lolita Reiach Esra Croft Email ecroft0@t-online.de ecroft0@t-online.de ecroft0@t-online.de Ireiach2@unc.edu Ireiach2@unc.edu ecrofto@t-online.de OrderNum OrderDate ShippingCode ShippingSpeed ItemID Description 1/2/2022 002 zip ties 356 356 356 251 251 220 1/2/2022 002 1/2/2022 002 3/17/2021001 3/17/2021001 2/11/2021001 1-Day 1-Day 1-Day Ground Ground Ground 434 897 591 591 327 586 duct tape trash bags trash bags dish soap chainsaw
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


