Question: 1 : In the Access Control lecture, we covered the Bell - LaPadula ( BLP ) access control model ( for confidentiality ) . For
: In the Access Control lecture, we covered the BellLaPadula BLP access control model for confidentiality For this homework, the goal is to analyze the applicability of the simple and star properties of the BLP model under the scenario given below:
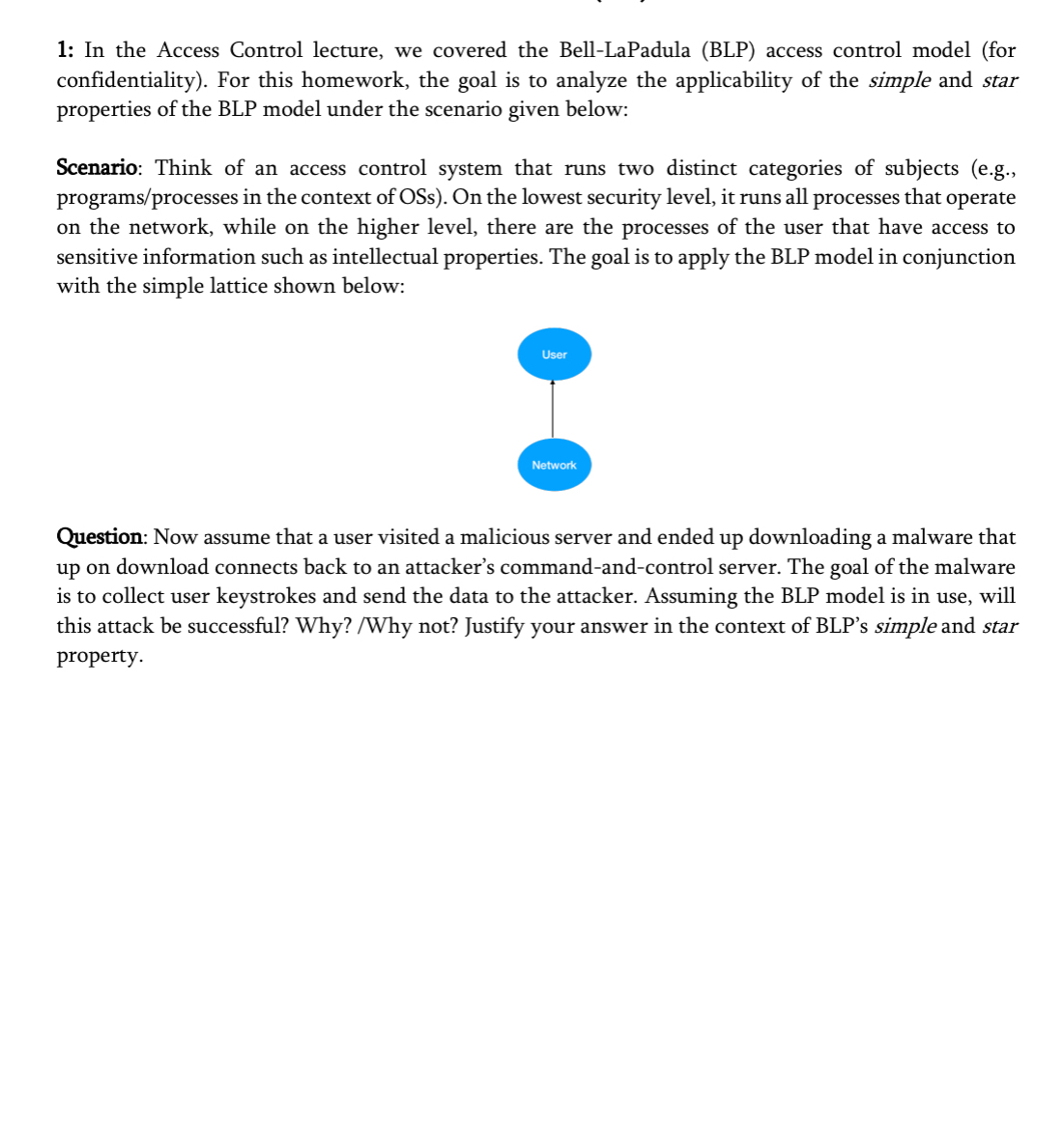
Scenario: Think of an access control system that runs two distinct categories of subjects eg programsprocesses in the context of OSs On the lowest security level, it runs all processes that operate on the network, while on the higher level, there are the processes of the user that have access to sensitive information such as intellectual properties. The goal is to apply the BLP model in conjunction with the simple lattice shown below:
Question: Now assume that a user visited a malicious server and ended up downloading a malware that up on download connects back to an attacker's commandandcontrol server. The goal of the malware is to collect user keystrokes and send the data to the attacker. Assuming the BLP model is in use, will this attack be successful? Why? Why not? Justify your answer in the context of BLPs simple and star property.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


