Question: 1) Using any programming language of your choice implement the Frequency analysis attack to break a vigenere cipher that is using a key of length
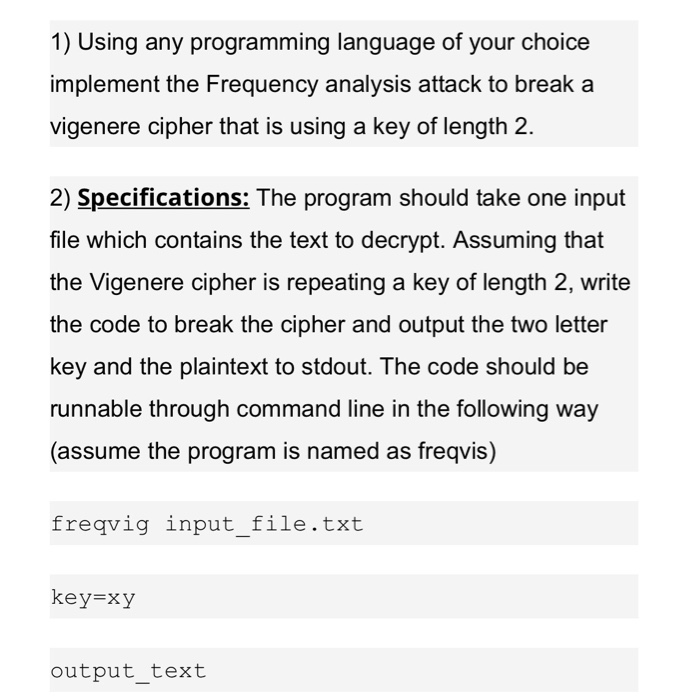


1) Using any programming language of your choice implement the Frequency analysis attack to break a vigenere cipher that is using a key of length 2. 2) Specifications: The program should take one input file which contains the text to decrypt. Assuming that the Vigenere cipher is repeating a key of length 2, write the code to break the cipher and output the two letter key and the plaintext to stdout. The code should be runnable through command line in the following way (assume the program is named as freqvis) freqvig input_file.txt key=xy output text Input text: ybiokq rfzqrb nlz jgak 11 oapzfi muikp gkj pnb nxj kksko hbkk nbxb hbllxb yek okxrffbj fz tgp zek nafkq vigzk tnbxb zek dxlcftd vekxyxtay tkok okxxbj qnb qbkmko ok nfy pnfxq yikbbby tgp qkkbrftd nxsjkookm qnb jlm qxlzqka llxtgoj toqn x euoz pnxxm hxxh gkj qnb qbkmko rflqka yqgozika rluh ok nfy beb ek pzogfmezbtbj eojybrc gkj pgiaqka cxzznftd nbx ft poikkib gp yek zgjk cuocxxa cfze cbghkkokm iojhp nb xbybtqka zek ftqxryfuk nb iekoopnbj eop ylrfzrjb gp nfy ltie xta rxyq lokbjls ft iock" Output: Key xg "She saw a secret little clearing and a secret little hot made of rustic poles And she had never been here before She realized it was the quiet place where the growing pheasants were reared the keeper in his shirt sleeves was kneeling hammering The dog trotted forward with a short sharp bark and the keeper lifted his face suddenly and saw her He had a startled look in his eyes He straightened himself and saluted watching her in silence as she came forward with weakening 1imbs He resented the intrusion he cherished his solitude as his only and last freedom in life
Step by Step Solution
There are 3 Steps involved in it
Implementation of Frequency Analysis Attack on Vigenere Cipher Key length 2 Detected Key gx Decrypted Plaintext secret uzckuv hot djun 11 idjczl poles ... View full answer

Get step-by-step solutions from verified subject matter experts


