Question: 10(a) Consider Case 1 from the replay attacks in the slides. Which of the following best describes what is happening? Select one: a. Eve can
10(a)
Consider Case 1 from the replay attacks in the slides. Which of the following best describes what is happening?
Select one:
a. Eve can perform a replay attack without knowing what any of the messages in the conversation are.
b. Eve can perform a replay attack, and in doing so she sees the plaintext of the rest of the conversation.
c. Eve cannot perform a replay attack, even if she learns ks
d. Eve can perform a replay attack, but only if she learns ks
(b)
Consider Case 2 from the replay attacks in the slides. Which of the following best describes what is happening?
Select one:
a. Eve can perform a replay attack, but only if she can predict r2
b. Eve can perform a replay attack, but only if she learns ks
c. Eve cannot perform a replay attack, even if she learns ks or can predict r2
(c)
Consider Case 3 from the replay attacks in the slides. It is not vulnerable to replay attacks as long as the clocks are synchronized and the authentication exchanges are cached for a certain amount of time.
Select one:
True
False
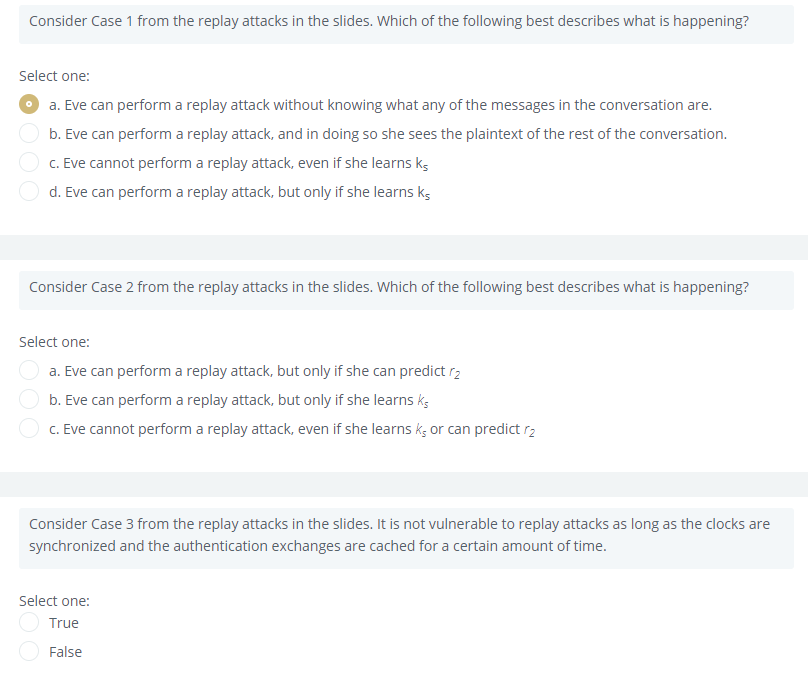
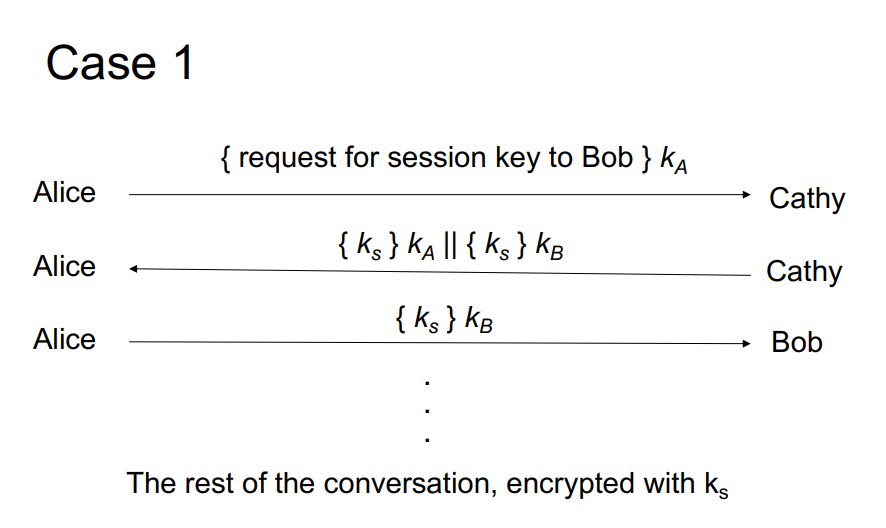
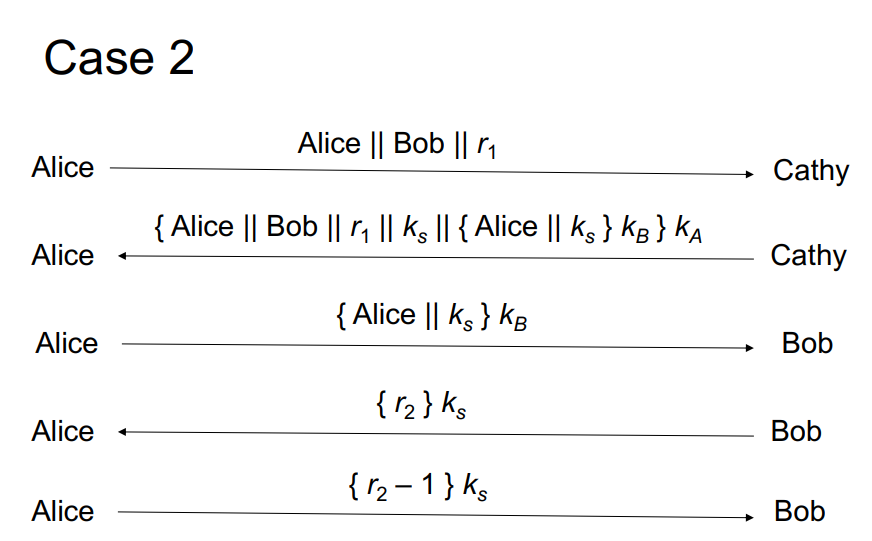
Consider Case 1 from the replay attacks in the slides. Which of the following best describes what is happening? Select one: a. Eve can perform a replay attack without knowing what any of the messages in the conversation are. b. Eve can perform a replay attack, and in doing so she sees the plaintext of the rest of the conversation. c. Eve cannot perform a replay attack, even if she learns ks d. Eve can perform a replay attack, but only if she learns ks Consider Case 2 from the replay attacks in the slides. Which of the following best describes what is happening? Select one: a. Eve can perform a replay attack, but only if she can predict ra b. Eve can perform a replay attack, but only if she learns ks C. Eve cannot perform a replay attack, even if she learns ks or can predict rz Consider Case 3 from the replay attacks in the slides. It is not vulnerable to replay attacks as long as the clocks are synchronized and the authentication exchanges are cached for a certain amount of time. Select one: True False Case 1 { request for session key to Bob } ka Alice Cathy {ks } kall { ks } KB Alice Cathy Alice - {Ks} kB Bob The rest of the conversation, encrypted with ks Case 2 Alice || Bob || r1 Alice Cathy {Alice || Bob || 61 || ks Il {Alice || ks } ke} ka Alice + Cathy { Alice || ks } KB Alice Bob {r2} ks Alice Bob {r2-1}ks Alice Bob Case 3 Alice Alice || Bob || r1 Cathy {Alice || Bob || 61 || ks || {Alice || T || ks } k}ka Alice Cathy {Alice || T || ks } kg Alice Bob { r2}k Alice + Bob {12-1} ks Alice Bob Consider Case 1 from the replay attacks in the slides. Which of the following best describes what is happening? Select one: a. Eve can perform a replay attack without knowing what any of the messages in the conversation are. b. Eve can perform a replay attack, and in doing so she sees the plaintext of the rest of the conversation. c. Eve cannot perform a replay attack, even if she learns ks d. Eve can perform a replay attack, but only if she learns ks Consider Case 2 from the replay attacks in the slides. Which of the following best describes what is happening? Select one: a. Eve can perform a replay attack, but only if she can predict ra b. Eve can perform a replay attack, but only if she learns ks C. Eve cannot perform a replay attack, even if she learns ks or can predict rz Consider Case 3 from the replay attacks in the slides. It is not vulnerable to replay attacks as long as the clocks are synchronized and the authentication exchanges are cached for a certain amount of time. Select one: True False Case 1 { request for session key to Bob } ka Alice Cathy {ks } kall { ks } KB Alice Cathy Alice - {Ks} kB Bob The rest of the conversation, encrypted with ks Case 2 Alice || Bob || r1 Alice Cathy {Alice || Bob || 61 || ks Il {Alice || ks } ke} ka Alice + Cathy { Alice || ks } KB Alice Bob {r2} ks Alice Bob {r2-1}ks Alice Bob Case 3 Alice Alice || Bob || r1 Cathy {Alice || Bob || 61 || ks || {Alice || T || ks } k}ka Alice Cathy {Alice || T || ks } kg Alice Bob { r2}k Alice + Bob {12-1} ks Alice Bob
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


