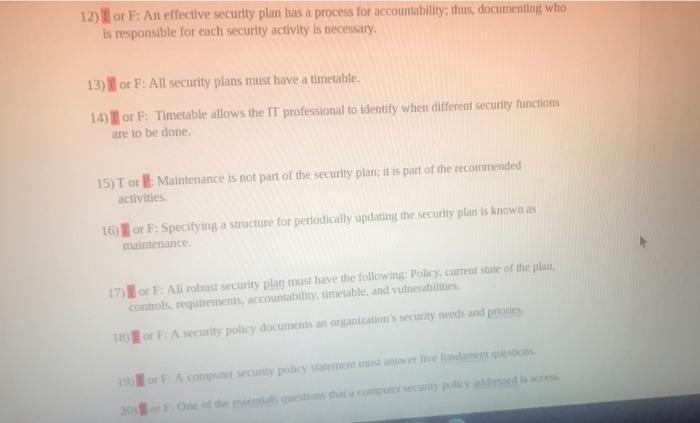
Question: 12) or F: An effective security plan has a process for accountability; thus, documenting who is responsible for each security activity is necessary, 13) or
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


