Question: 12.5.15 *Consider Protocol 12-8. How would Alice compute K? How would Bob compute K. Why is it insecure? (Hint: someone impersonating Bob can do a
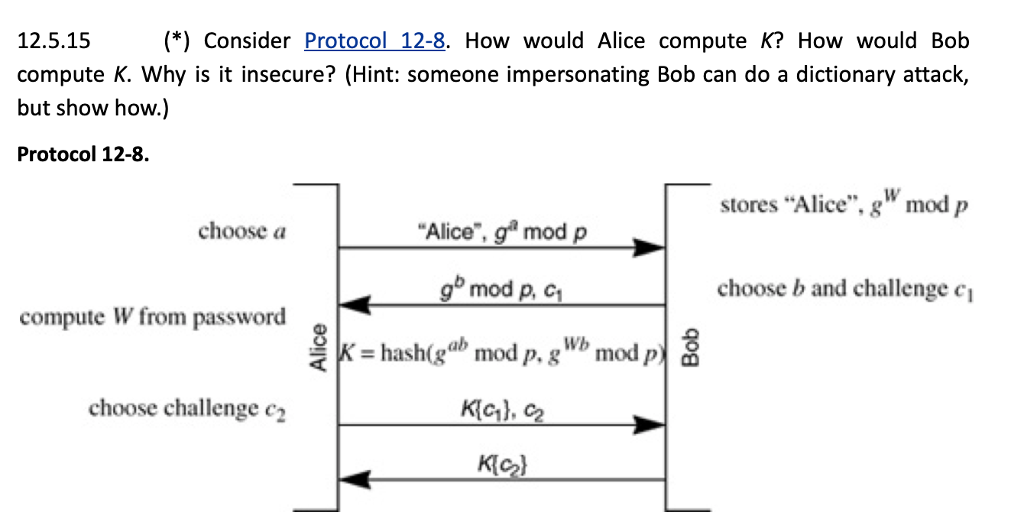
12.5.15 *Consider Protocol 12-8. How would Alice compute K? How would Bob compute K. Why is it insecure? (Hint: someone impersonating Bob can do a dictionary attack, but show how.) Protocol 12-8. stores "Alice". g" mod p Alice", g mod p g mod p. c, K- hashigal mod p.gW mod p3 choose a choose b and challenge ci compute W from password hoose challenge KG
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


