Question: 13) In class we discussed the following PHP script for a login page : (1 mark) $username - $_GET[user); $password - $_GET[pwd); $sql - SELECT
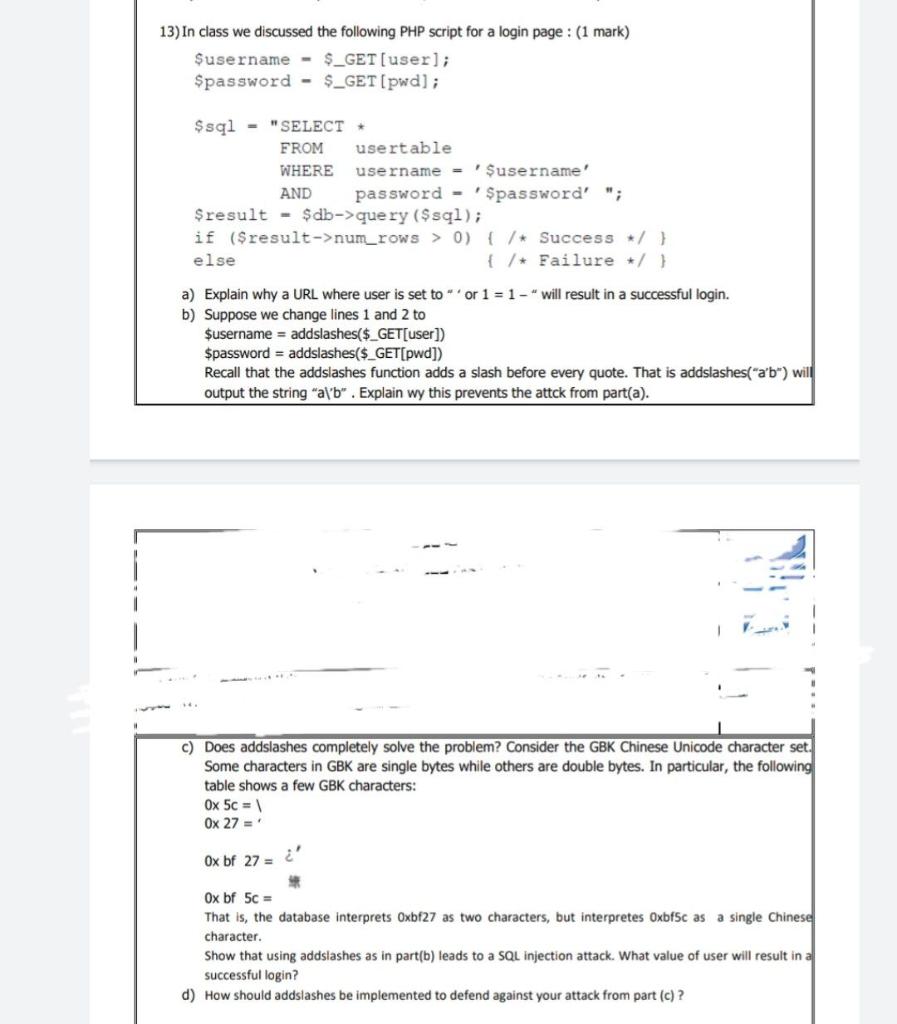
13) In class we discussed the following PHP script for a login page : (1 mark) $username - $_GET[user); $password - $_GET[pwd); $sql - "SELECT * FROM usertable WHERE username = '$username' AND password - "Spassword' "; $result - $db->query($sql); if ($result->num_rows > 0) { /* Success */ } else { /* Failure */ } a) Explain why a URL where user is set to or 1 = 1 -" will result in a successful login. b) Suppose we change lines 1 and 2 to $username = addslashes($_GET[user]) $password = addslashes($_GET[pwd]) Recall that the addslashes function adds a slash before every quote. That is addslashes("a'b") will output the string "alb". Explain wy this prevents the attck from part(a). c) Does addslashes completely solve the problem? Consider the GBK Chinese Unicode character set. Some characters in GBK are single bytes while others are double bytes. In particular, the following table shows a few GBK characters: Ox 5c = Ox 27 = Ox bf 27 = Ox bf 5C = That is, the database interprets Oxbf27 as two characters, but interpretes Oxbf5c as a single Chinese character. Show that using addslashes as in part(b) leads to a SQL injection attack. What value of user will result in a successful login? d) How should addslashes be implemented to defend against your attack from part (c)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


