Question: 13.10. We consider a system in which a key kAB is established using the Diffie- Hellman key exchange protocol, and the encryption keyskare then derived
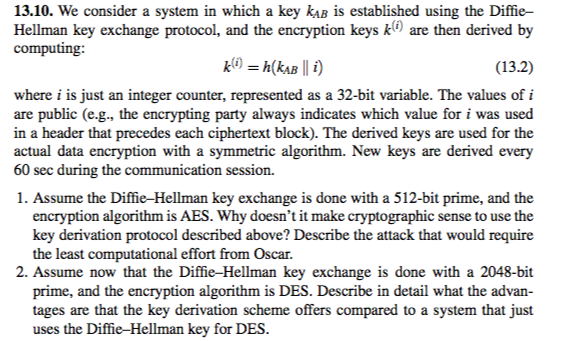
13.10. We consider a system in which a key kAB is established using the Diffie- Hellman key exchange protocol, and the encryption keyskare then derived by computing: (13.2) where i is just an integer counter, represented as a 32-bit variable. The values of i are public (e.g., the encrypting party always indicates which value for i was used in a header that precedes each ciphertext block). The derived keys are used for the actual data encryption with a symmetric algorithm. New keys are derived every 60 sec during the communication session 1. Assume the Diffie-Hellman key exchange is done with a 512-bit prime, and the encryption algorithm is AES. Why doesn't it make cryptographic sense to use the key derivation protocol described above? Describe the attack that would require the least computational effort from Oscar. 2. Assume now that the Diffie-Hellman key exchange is done with a 2048-bit prime, and the encryption algorithm is DES. Describe in detail what the advan tages are that the key derivation scheme offers compared to a system that just uses the Diffie-Hellman key for DES
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


