Question: 1)You now have a firewall between the internet (represented by a cloud) and your network router. Click the play button and watch what happens. Do
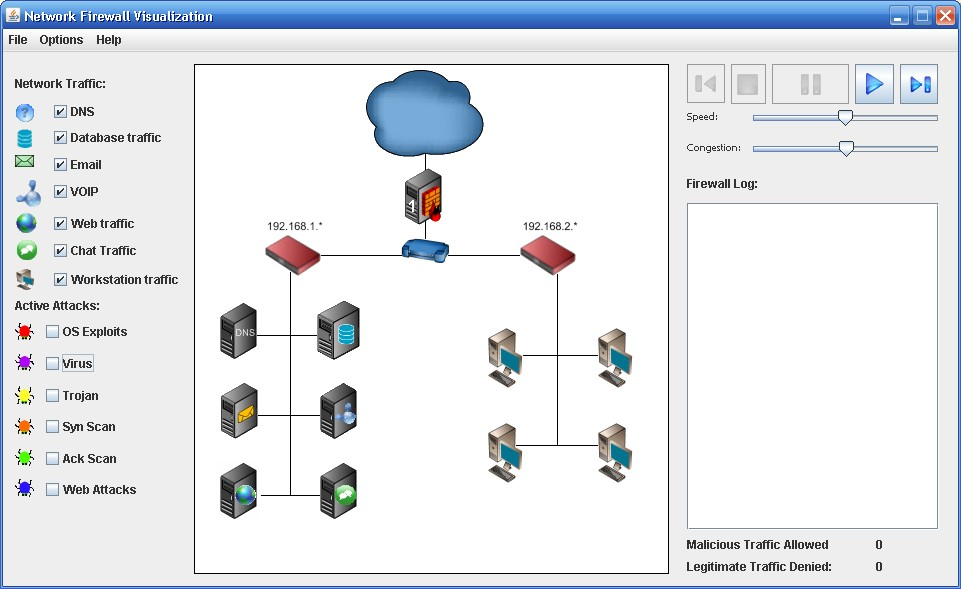
1)You now have a firewall between the internet (represented by a cloud) and your network router. Click the play button and watch what happens. Do you see traffic flowing from the internet into your system or from your network to the internet? Explain why or why not:
2)Add some active attacks by clicking on several different options. Are these attacks able to get to your network? Do you feel your system is secure? Whats wrong with this scenario?
3)Configure your firewall to allow traffic to flow in and out of your network . What traffic now flows through the firewall? Add some active attacks and watch if they flow through the firewall. Would you claim your rule is now sufficient to allow traffic to flow for a typical network? Why or why not? Do any of the active attacks now work against machines behind the firewall?
4)Come up with a series of rules which seems to protect the network from all attacks. Be sure to watch the legitimate traffic denied and malicious traffic permitted in the lower right hand portion of the screen. That should tell you how well your rules are working.
How many rules did you have to write to secure your network? Were you able to completely secure the network? What types of rules did you create?
Network Firewall Visualization File Options Help Network Traffic: VDNS Database traffic Email Speed: Congestion: Firewall Log: VWeb traffic 192.168.1. 192.168.2. Chat Traffic Y Workstation traffic Active Attacks: Los Exploits Virus Trojan Sym Scan Ack Scan Web Attacks Malicious Traffic Allowed 0 Legitimate Traffic Denied: 0
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


