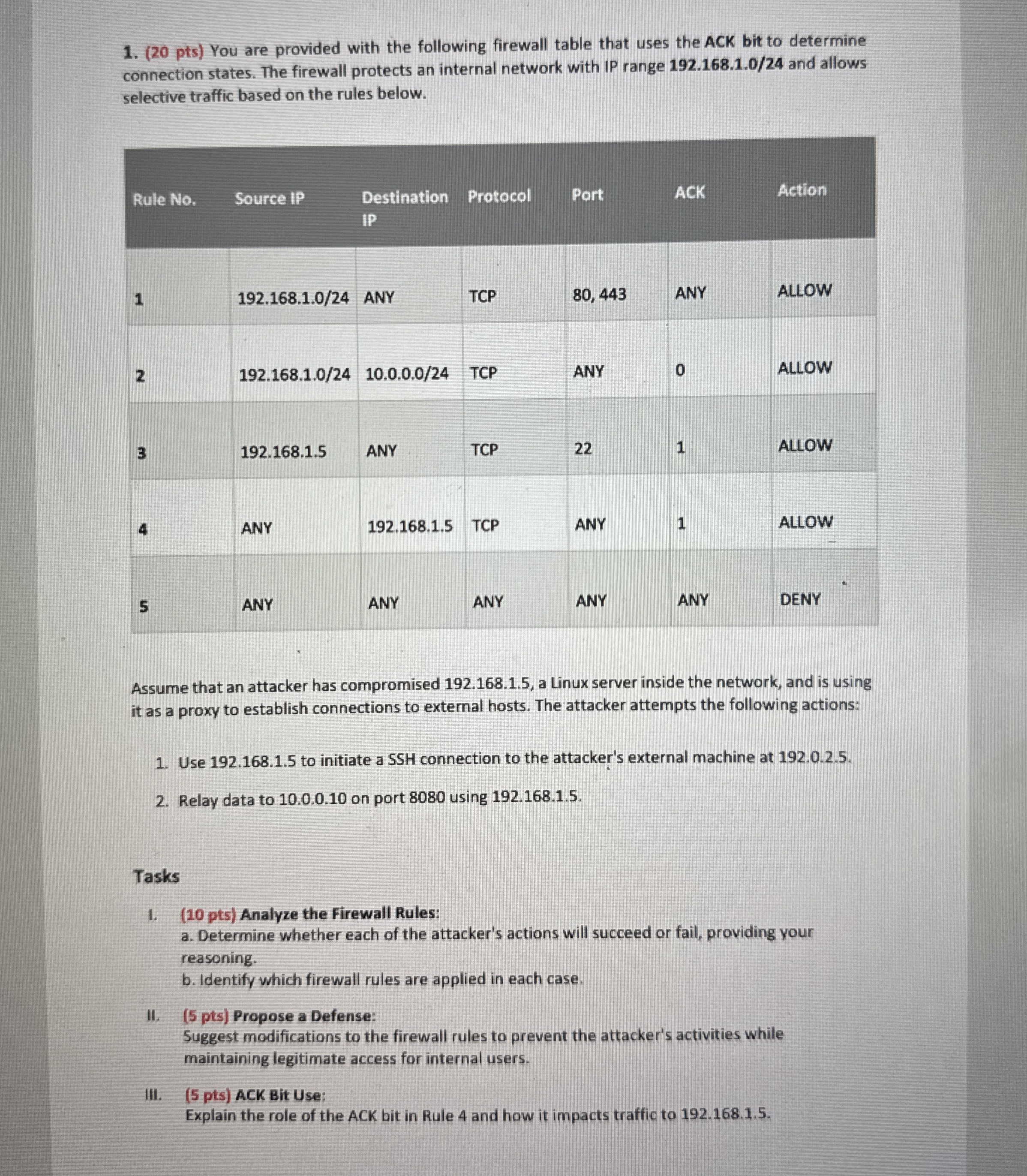
Question: ( 2 0 pts ) You are provided with the following firewall table that uses the ACK bit to determine connection states. The firewall protects
pts You are provided with the following firewall table that uses the ACK bit to determine connection states. The firewall protects an internal network with IP range and allows selective traffic based on the rules below.
tableRule NoSource IPtableDestinationIPProtocol,Port,ACK,ActionANY,TCPANY,AllowTCPANY,ALLOWANY,TCPAllowANY,TCPANY,AlLOWANY,ANY,ANY,ANY,ANY,DENY
Assume that an attacker has compromised a Linux server inside the network, and is using it as a proxy to establish connections to external hosts. The attacker attempts the following actions:
Use to initiate a SSH connection to the attacker's external machine at
Relay data to on port using
Tasks
I. pts Analyze the Firewall Rules:
a Determine whether each of the attacker's actions will succeed or fail, providing your reasoning.
b Identify which firewall rules are applied in each case.
II pts Propose a Defense:
Suggest modifications to the firewall rules to prevent the attacker's activities while maintaining legitimate access for internal users.
III. pts ACK Bit Use:
Explain the role of the ACK bit in Rule and how it impacts traffic to
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


