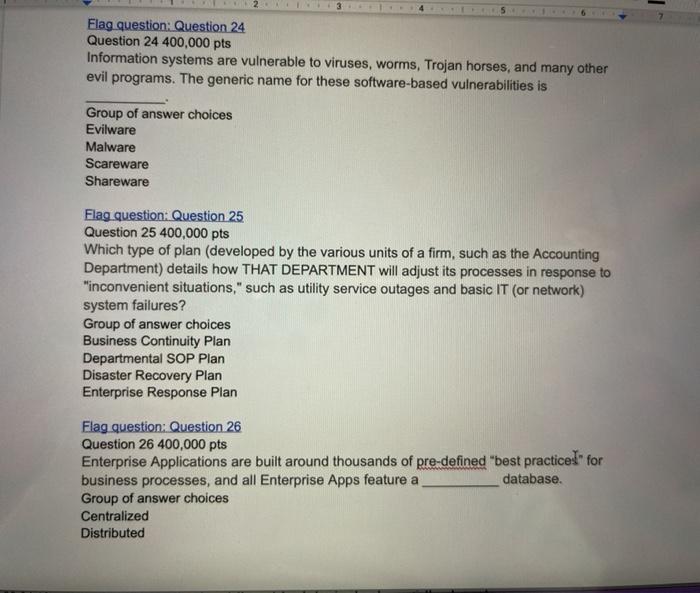
Question: 2 5 Flag question: Question 24 Question 24 400,000 pts Information systems are vulnerable to viruses, worms, Trojan horses, and many other evil programs. The
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


