Question: 2. Reverse compile the program in question2.asm by following the steps A, B, and c, below The original program does not do any meaningful computation.
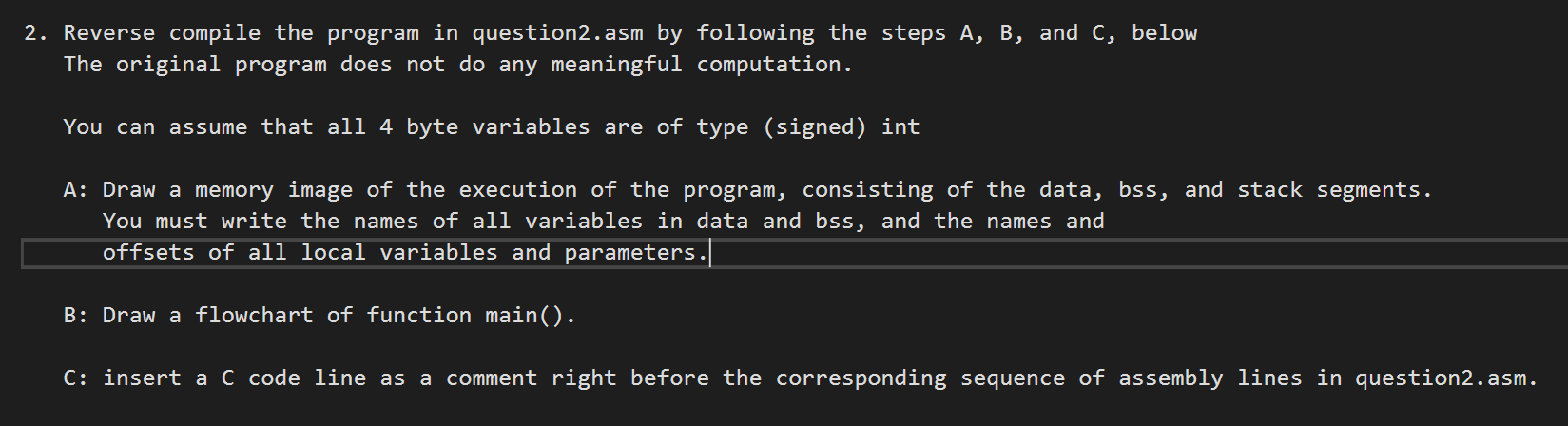
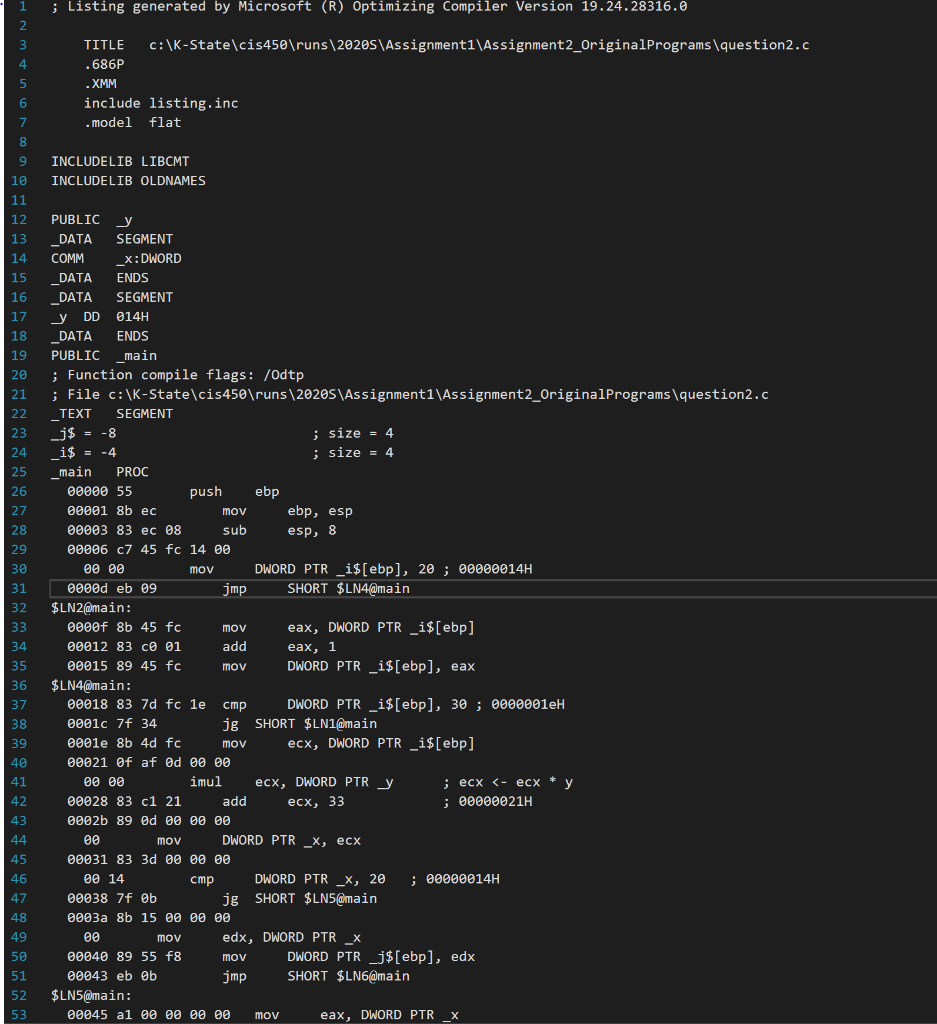
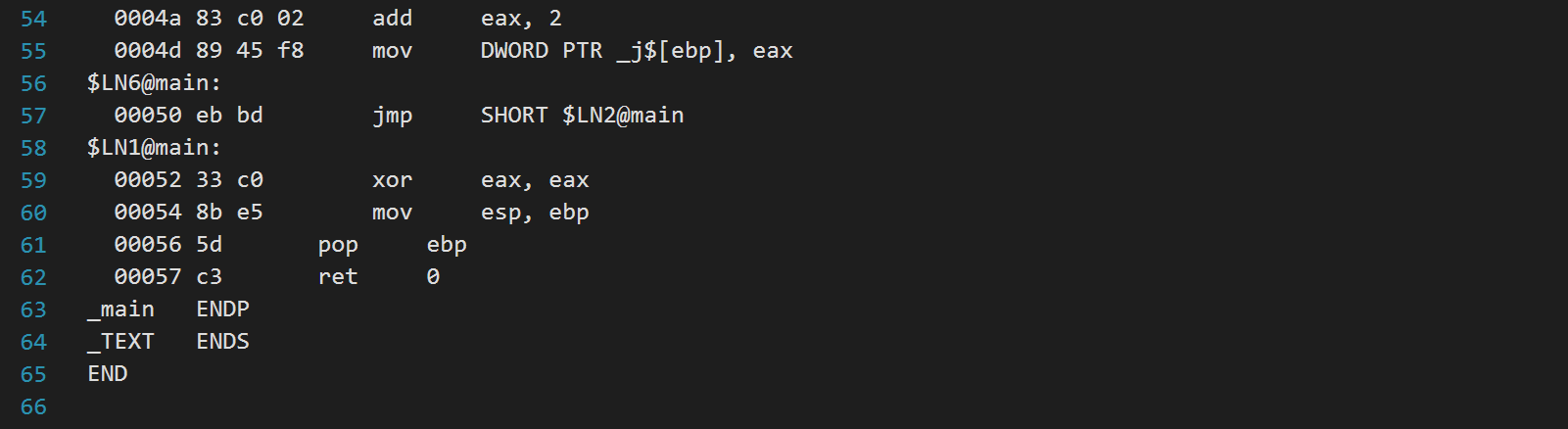
2. Reverse compile the program in question2.asm by following the steps A, B, and c, below The original program does not do any meaningful computation. You can assume that all 4 byte variables are of type (signed) int A: Draw a memory image of the execution of the program, consisting of the data, bss, and stack segments. You must write the names of all variables in data and bss, and the names and offsets of all local variables and parameters. habies in data and oss, and the names and bss, a B: Draw a flowchart of function main(). C: insert a C code line as a comment right before the corresponding sequence of assembly lines in question2.asm. ; Listing generated by Microsoft (R) Optimizing Compiler Version 19.24.28316.0 ovou AWNE TITLE C:\K-State\cis450 uns 2020 Assignment1 Assignment2_originalPrograms question2.c .686P .XMM include listing.inc .model flat INCLUDELIB LIBCMT INCLUDELIB OLDNAMES 13 17 18 19 21 22 32 PUBLIC DATA SEGMENT COMMx:DWORD _DATA ENDS _DATA SEGMENT y DD 014H _DATA ENDS PUBLIC _main ; Function compile flags: /Odtp ; File c:\K-State\cis450 runs 2020s\Assignment1 Assignment2_OriginalPrograms question2. _TEXT SEGMENT j$ = -8 ; size = 4 _i$ = -4 ; size = 4 main PROC 00000 55 push ebp 00001 8b ec mov e bp, esp 00003 83 ec 08 sub esp, 8 00006 c7 45 fc 14 00 00 00 mov DWORD PTR _i$[ebp), 20 ; 00000014H 0000d eb 09 jmp SHORT $LN4@main $LN2@main: 0000f 8b 45 fc mov eax, DWORD PTR _i$[ebp] 00012 83 co 01 add eax, 1 00015 89 45 fc mov DWORD PTR _i$[ebp), eax $LN4@main: 00018 83 7d fc le cmp DWORD PTR _i$[ebp), 30 ; 00000011H 0001c 7f 34 jg SHORT $LN1@main 0001e 8b 4d fcmovecx, DWORD PTR _i$[ebp) 00021 Of af Od 00 00 00 eO i mul ecx, DWORD PTR Y ; ecx
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


