Question: 2 . The least - privilege principle can be used to effectively defend against the race condition attacks discussed in this chapter. Can we use
The leastprivilege principle can be used to effectively defend against the race condition attacks discussed in this chapter. Can we use the same principle to defeat
bufferoverflow
attacks? Why or why not? Namely, before executing the vulnerable function, we
disable
the root privilege; after the vulnerable function returns, we enable the privilege
back.
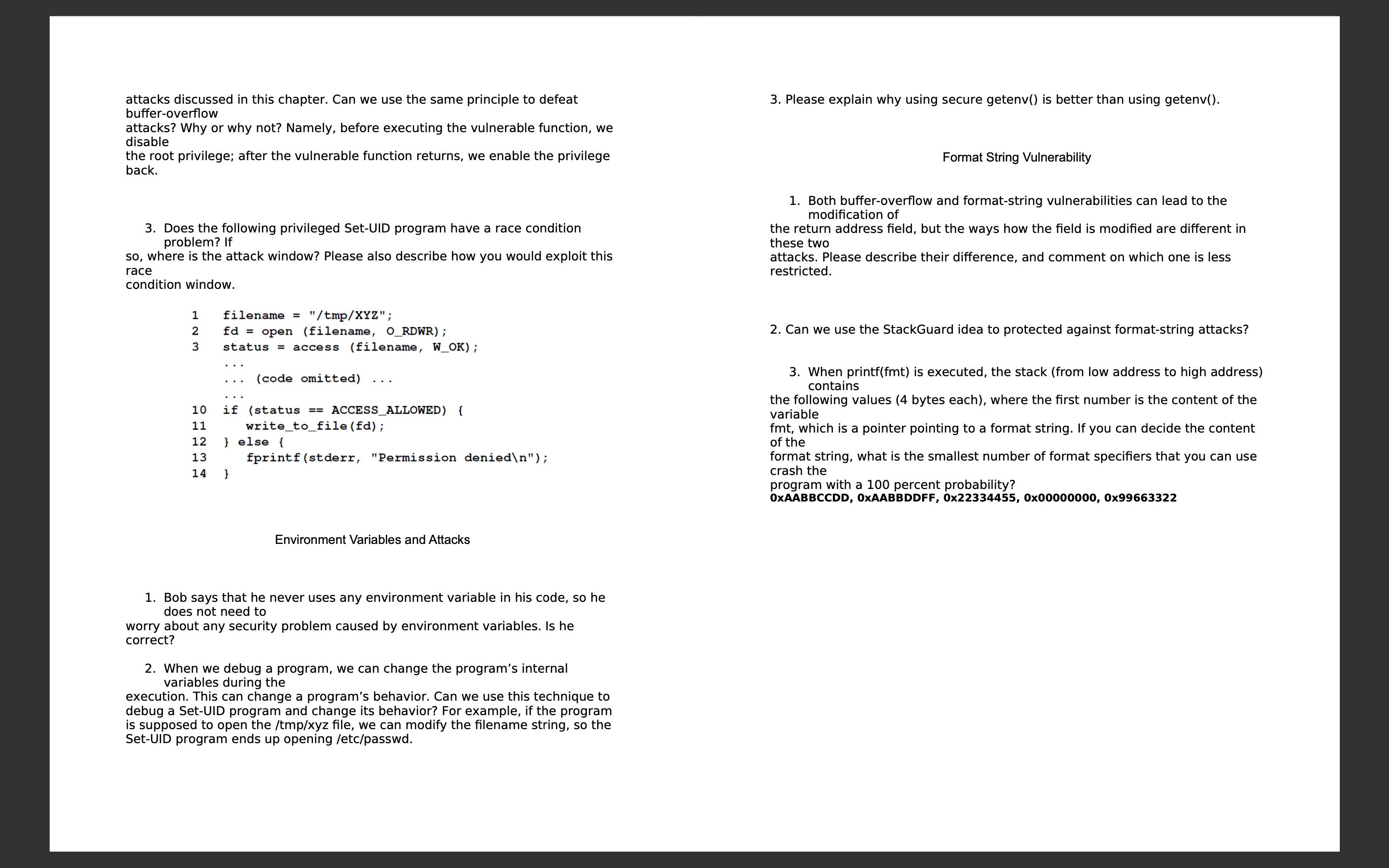
Does the following privileged SetUID program have a race condition
problem? If
so where is the attack window? Please also describe how you would exploit this
race
condition window.
Please explain why using secure getenv is better than using getenv
Format String Vulnerability
Both bufferoverflow and formatstring vulnerabilities can lead to the
modification of
the return address field, but the ways how the field is modified are different in
these two
attacks. Please describe their difference, and comment on which one is less
restricted.
Can we use the StackGuard idea to protected against formatstring attacks?
When is executed, the stack from low address to high address
contains
the following values bytes each where the first number is the content of the
variable
fmt which is a pointer pointing to a format string. If you can decide the content
of the
format string, what is the smallest number of format specifiers that you can use
crash the
program with a percent probability?
OXAABBCCDD, OXAABBDDFF, xxx
Bob says that he never uses any environment variable in his code, so he
does not need to
worry about any security problem caused by environment variables. Is he
correct?
When we debug a program, we can change the program's internal
variables during the
execution. This can change a program's behavior. Can we use this technique to
debug a SetUID program and change its behavior? For example, if the program
is supposed to open the tmpxyz file, we can modify the filename string, so the
SetUID program ends up opening etcpasswd
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


