Question: 2. Was there enough personal information returned that could potentially be used for identity theft? Explain why or why not. 3. How can identity thieves
2. Was there enough personal information returned that could potentially be used for identity theft? Explain why or why not.
3. How can identity thieves take advantage of social networking users to steal personal information?
4. According to Facebook.com, who owns the information posted by a user? Include specific text from Facebook.com in your answer.
5. What is a security feature you should always look for in any website that will ask for personal information to share with others?
6. What implications can the social networking sites have for job applicants?
7. What is the risk of combining your family and personal friends with your business
contacts and associates?
8. What type of personal information could an attacker obtain from a user profile on
LinkedIn.com that he or she could use for identity theft?
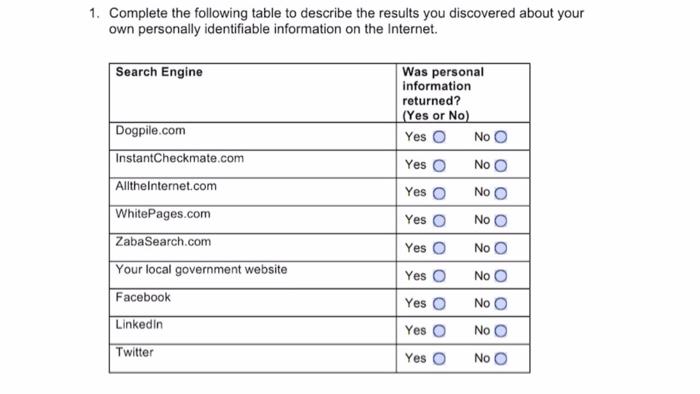
1. Complete the following table to describe the results you discovered about your own personally identifiable information on the Internet
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


