Question: 2. We conduct a known-plaintext attack on an LFSR-based stream cipher. We know that the plaintext sent was: 1001 0010 0110 1101 1001 0010
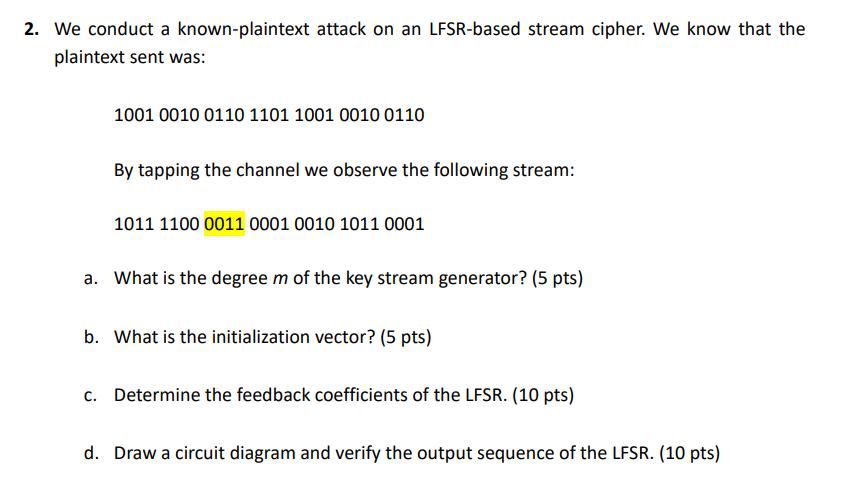
2. We conduct a known-plaintext attack on an LFSR-based stream cipher. We know that the plaintext sent was: 1001 0010 0110 1101 1001 0010 0110 By tapping the channel we observe the following stream: 1011 1100 0011 0001 0010 1011 0001 a. What is the degree m of the key stream generator? (5 pts) b. What is the initialization vector? (5 pts) c. Determine the feedback coefficients of the LFSR. (10 pts) d. Draw a circuit diagram and verify the output sequence of the LFSR. (10 pts)
Step by Step Solution
3.53 Rating (153 Votes )
There are 3 Steps involved in it
a We can find the key stream by doing XOR of the plain text and the ciphered text which gives ... View full answer

Get step-by-step solutions from verified subject matter experts


