Question: 2. Write a program that takes an input string from the user and encrypts the message, or decrypts it, using a multi-shift cipher: Multi-Shift Cypher:
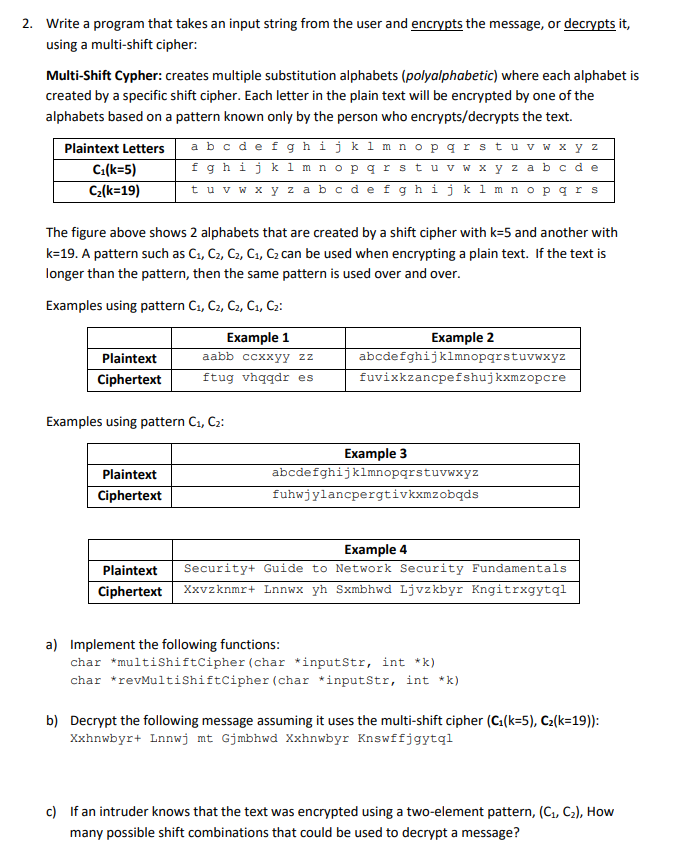
2. Write a program that takes an input string from the user and encrypts the message, or decrypts it, using a multi-shift cipher: Multi-Shift Cypher: creates multiple substitution alphabets (polyalphabetic) where each alphabet is created by a specific shift cipher. Each letter in the plain text will be encrypted by one of the alphabets based on a pattern known only by the person who encrypts/decrypts the text. Plaintext Letters C1(k-5) C2(k-19) a b cdefgh ijkl m n opqrstu v wx y z fghjk1mnopqrstuvwxyzabcde tuvw x y z abcdefg hijkl m nopqrs The figure above shows 2 alphabets that are created by a shift cipher with k-5 and another with k-19. A pattern such as Ci, C2, C2, Ci, C2 can be used when encrypting a plain text. If the text is longer than the pattern, then the same pattern is used over and over Examples using pattern Ci, C2, C2, C1, C2: Example 1 aabb ccxxyy zz ftug vhqqdr es Example abcdefghijklmnopqrstuvwxyz fuvixkzancpefshujkxmzopcre Plaintext Ciphertext Examples using pattern Ci, C2: Example3 abcdefghijklmnopqrstuvwxyz fuhwjylancpergtivkxmzobqds Plaintext Ciphertext Example 4 Plaintext Security+ Guide to Network Security Fundamentals a) Implement the following functions char *multiShiftCipher (char inputStr, int *k) char *revMultiShiftcipher (char *inputStr, int *k) b) Decrypt the following message assuming it uses the multi-shift cipher (C1(k-5), C2(k-19)) Xxhnwbyr+ Lnnwj mt Gjmbhwd Xxhnwbyr Knswffjgytql c) If an intruder knows that the text was encrypted using a two-element pattern, (C, C2), How many possible shift combinations that could be used to decrypt a message
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


