Question: 2:29 Riving Servestar Proctoring Session Active THEeasier Show Support Chat forng Susan is part of a multi-disciplinary team working on a health-care application. One of
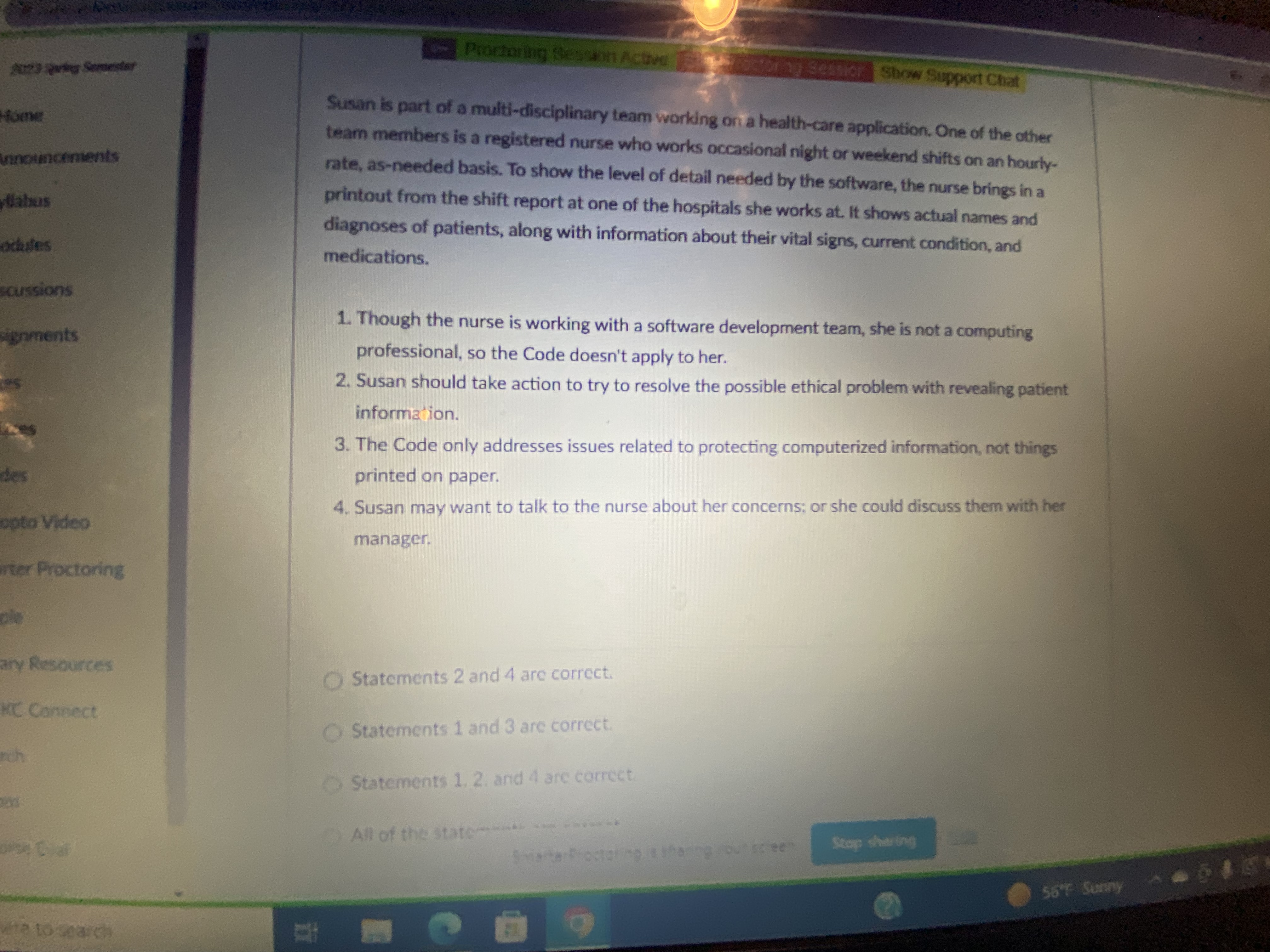
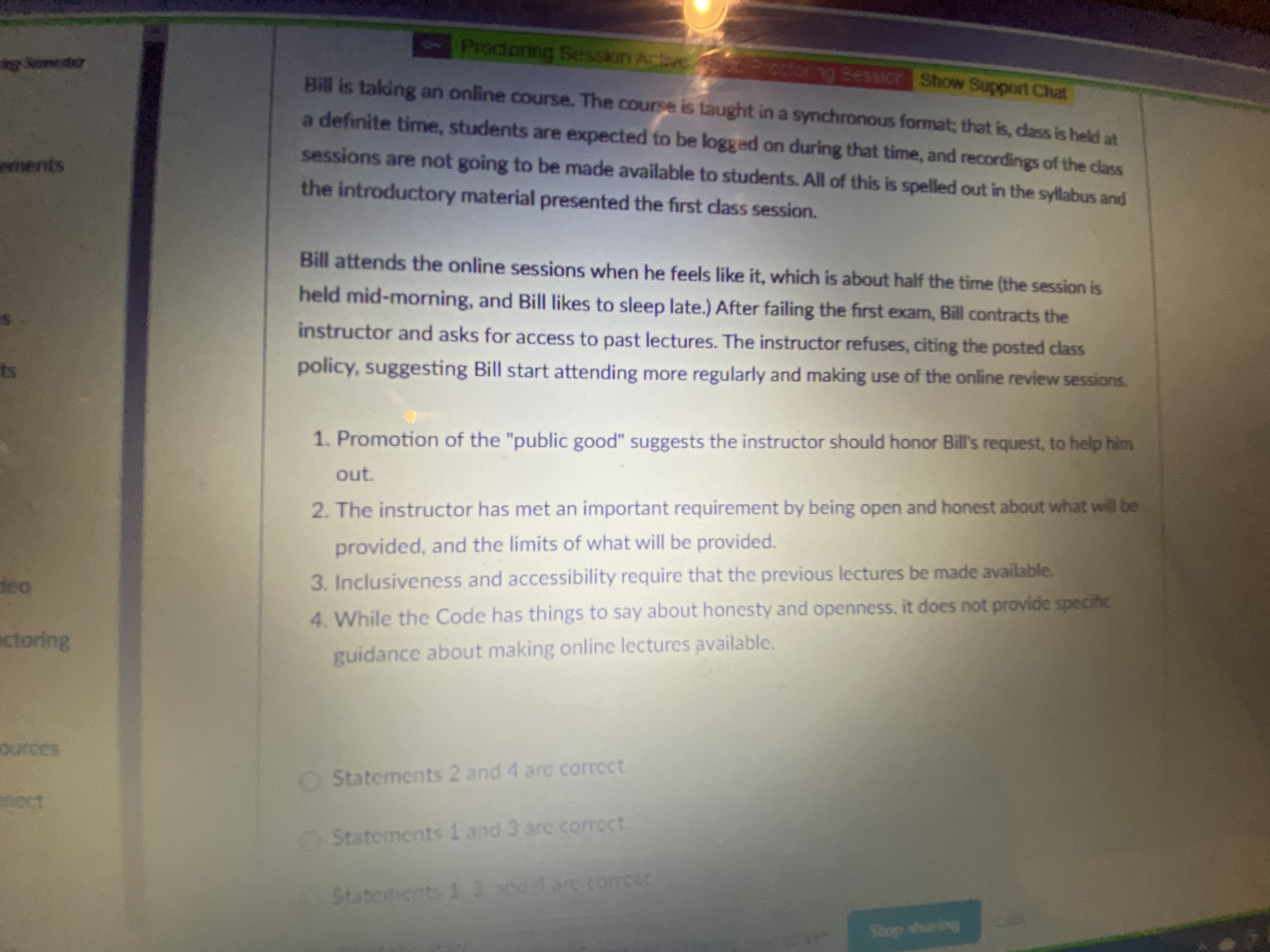
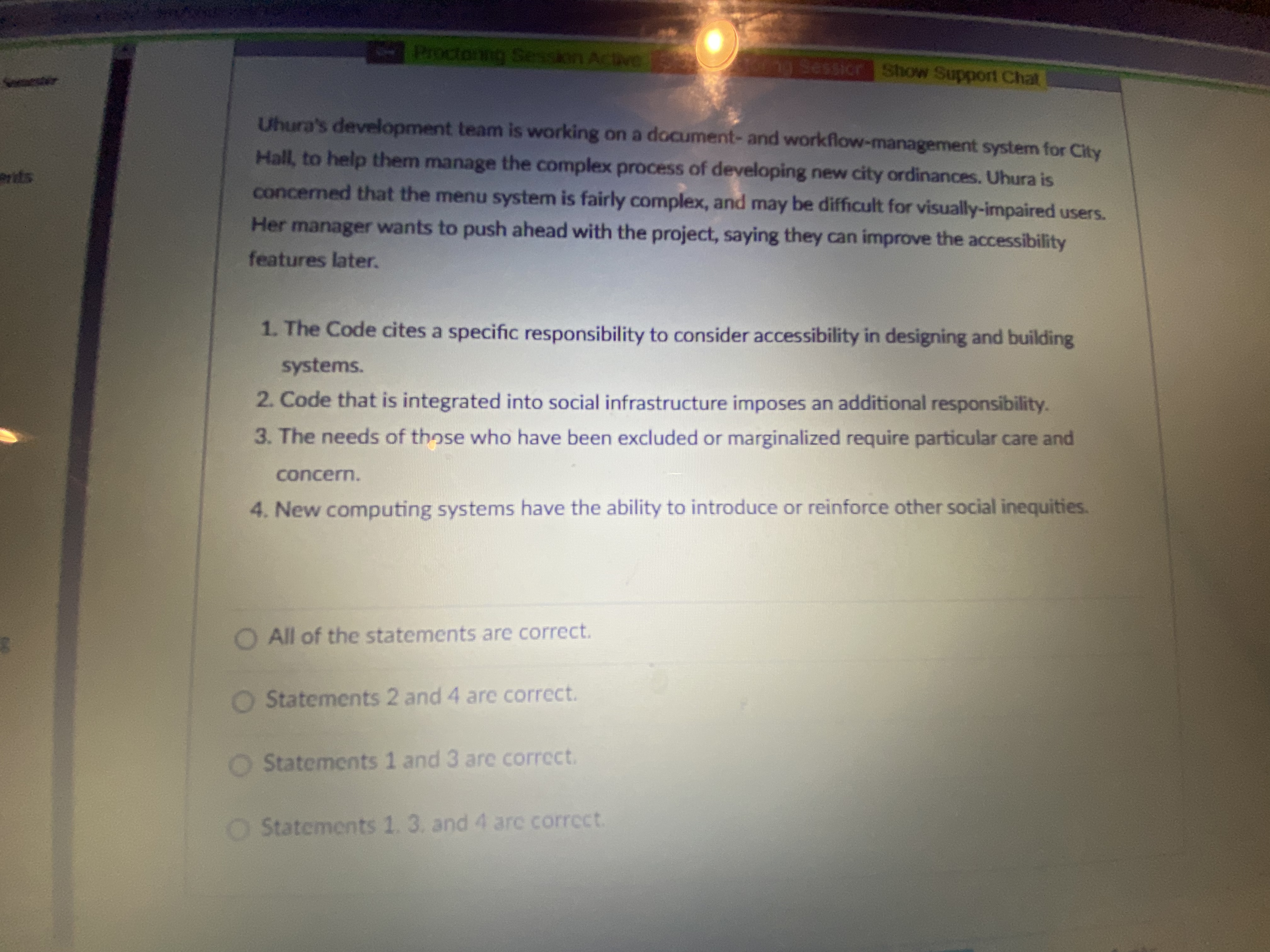
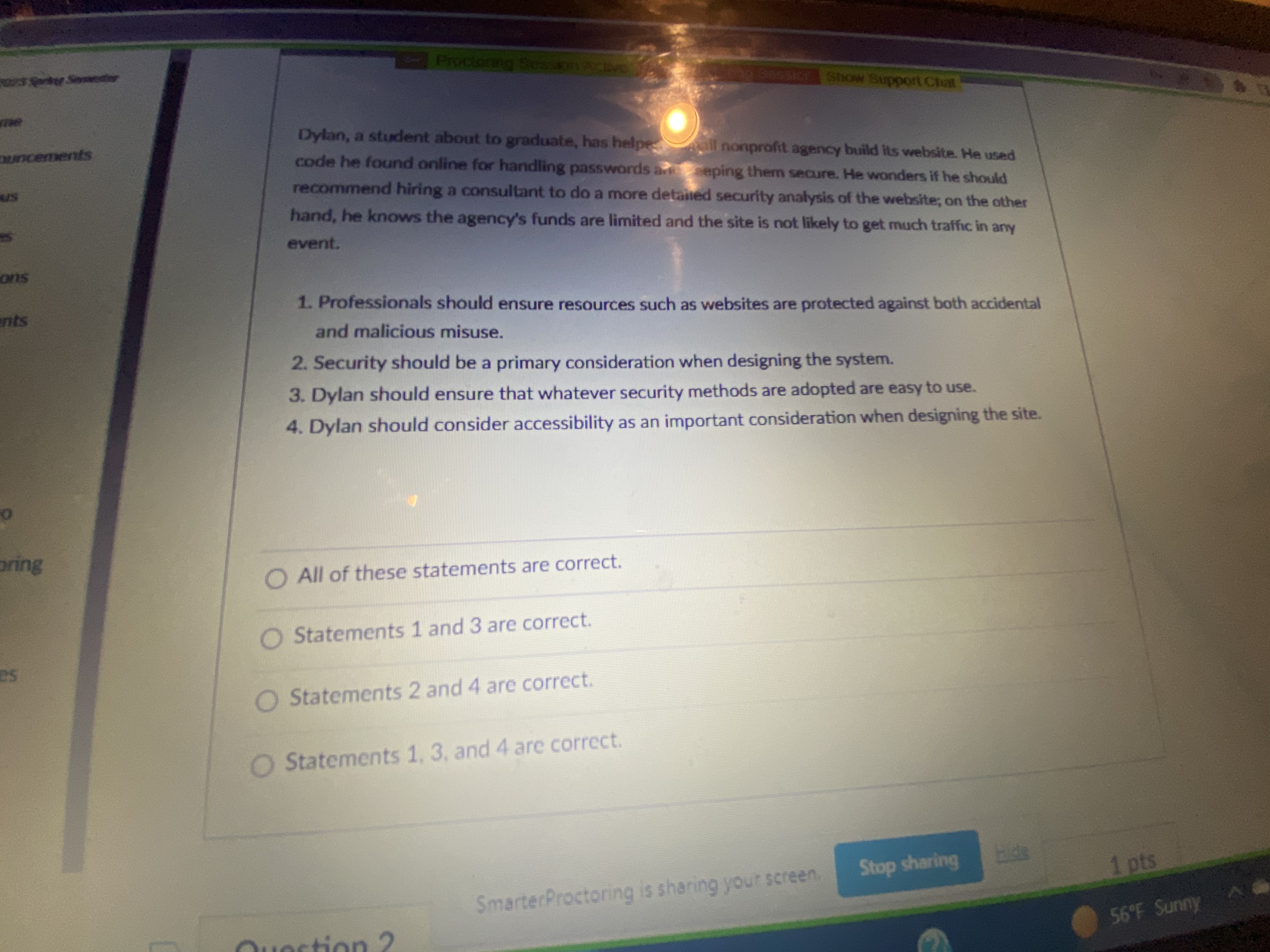
2:29 Riving Servestar Proctoring Session Active THEeasier Show Support Chat forng Susan is part of a multi-disciplinary team working on a health-care application. One of the other nnoucements team members is a registered nurse who works occasional night or weekend shifts on an hourly- rate, as-needed basis. To show the level of detail needed by the software, the nurse brings in a llabus printout from the shift report at one of the hospitals she works at. It shows actual names and ocktes diagnoses of patients, along with information about their vital signs, current condition, and medications. cussions goments 1. Though the nurse is working with a software development team, she is not a computing professional, so the Code doesn't apply to her. 2. Susan should take action to try to resolve the possible ethical problem with revealing patient information. 3. The Code only addresses issues related to protecting computerized information, not things printed on paper. 4. Susan may want to talk to the nurse about her concerns; or she could discuss them with her opto Video manager. inter Proctoring ple ary Resources Statements 2 and 4 are correct. KC Connect Statements 1 and 3 are correct. ech Statements 1. 2. and 4 are correct. All of the statemass Stop sharing 56'7 SunnyProctoring Session Active Procion ing Session Show Support Chat Bill is taking an online course. The course is taught in a synchronous format; that is, class is held at a definite time, students are expected to be logged on during that time, and recordings of the class ements sessions are not going to be made available to students. All of this is spelled out in the syllabus and the introductory material presented the first class session. Bill attends the online sessions when he feels like it, which is about half the time (the session is held mid-morning, and Bill likes to sleep late.) After failing the first exam, Bill contracts the instructor and asks for access to past lectures. The instructor refuses, citing the posted class policy, suggesting Bill start attending more regularly and making use of the online review sessions. 1. Promotion of the "public good" suggests the instructor should honor Bill's request, to help him out. 2. The instructor has met an important requirement by being open and honest about what will be provided, and the limits of what will be provided. 3. Inclusiveness and accessibility require that the previous lectures be made available. 4. While the Code has things to say about honesty and openness, it does not provide specific ctoring guidance about making online lectures available. ources Statements 2 and 4 are correct Statements 1 and 3 are correct Statements 1 3 and lars correct Stop cheringProctoring Session Active Sessicra Show Support Chat Uhura's development team is working on a document- and workflow-management system for City Hall, to help them manage the complex process of developing new city ordinances. Uhura is wrists concerned that the menu system is fairly complex, and may be difficult for visually-impaired users. Her manager wants to push ahead with the project, saying they can improve the accessibility features later. 1. The Code cites a specific responsibility to consider accessibility in designing and building systems. 2. Code that is integrated into social infrastructure imposes an additional responsibility. 3. The needs of those who have been excluded or marginalized require particular care and concern. 4. New computing systems have the ability to introduce or reinforce other social inequities. All of the statements are correct. O Statements 2 and 4 are correct. Statements 1 and 3 are correct. Statements 1. 3, and 4 are correct.Show Support Chat Dylan, a student about to graduate, has helper uncements all nonprofit agency build its website. He used code he found online for handling passwords and seping them secure. He wonders if he should US recommend hiring a consultant to do a more detailed security analysis of the website; on the other hand, he knows the agency's funds are limited and the site is not likely to get much traffic in any event. ons nts 1. Professionals should ensure resources such as websites are protected against both accidental and malicious misuse. 2. Security should be a primary consideration when designing the system. 3. Dylan should ensure that whatever security methods are adopted are easy to use. 4. Dylan should consider accessibility as an important consideration when designing the site. bring All of these statements are correct. Statements 1 and 3 are correct. Statements 2 and 4 are correct. Statements 1, 3, and 4 are correct. Stop sharing 1 pts SmarterProctoring is sharing your screen 56 F Sunny-Proctoring Session Action Factoring session Show Support Chat Ivan is a consultant providing advice regarding data mining. His latest client has two different data sources, one from a public source (a taxpayer database) and another from a private source (a vents medical clinic the company provides IT services for). Out of concern for privacy, they have replaced all names with random strings of characters, but have left all other information intact, so as not to hide relationships between the data. 1. Combining data sources can make previously-anonymous data become personally identifiable. 2. Protecting privacy requires careful analysis and consideration when merging data sources. 3. Ivan should ensure that the data collection was properly authorized. 4. Any data that is not needed for the project should be removed or disposed of. O All of the statements are correct. Satements 1 and 3 are correct. ing Statements 2 and 4 are correct. Statements 1. 3. and 4 are correct. 1 pts
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


