Question: 3. a. b. C. Discuss any TWO (2) techniques used to distribute keys in symmetric encryption. Describe THREE (3) applications of Public-Key cryptography. Refer
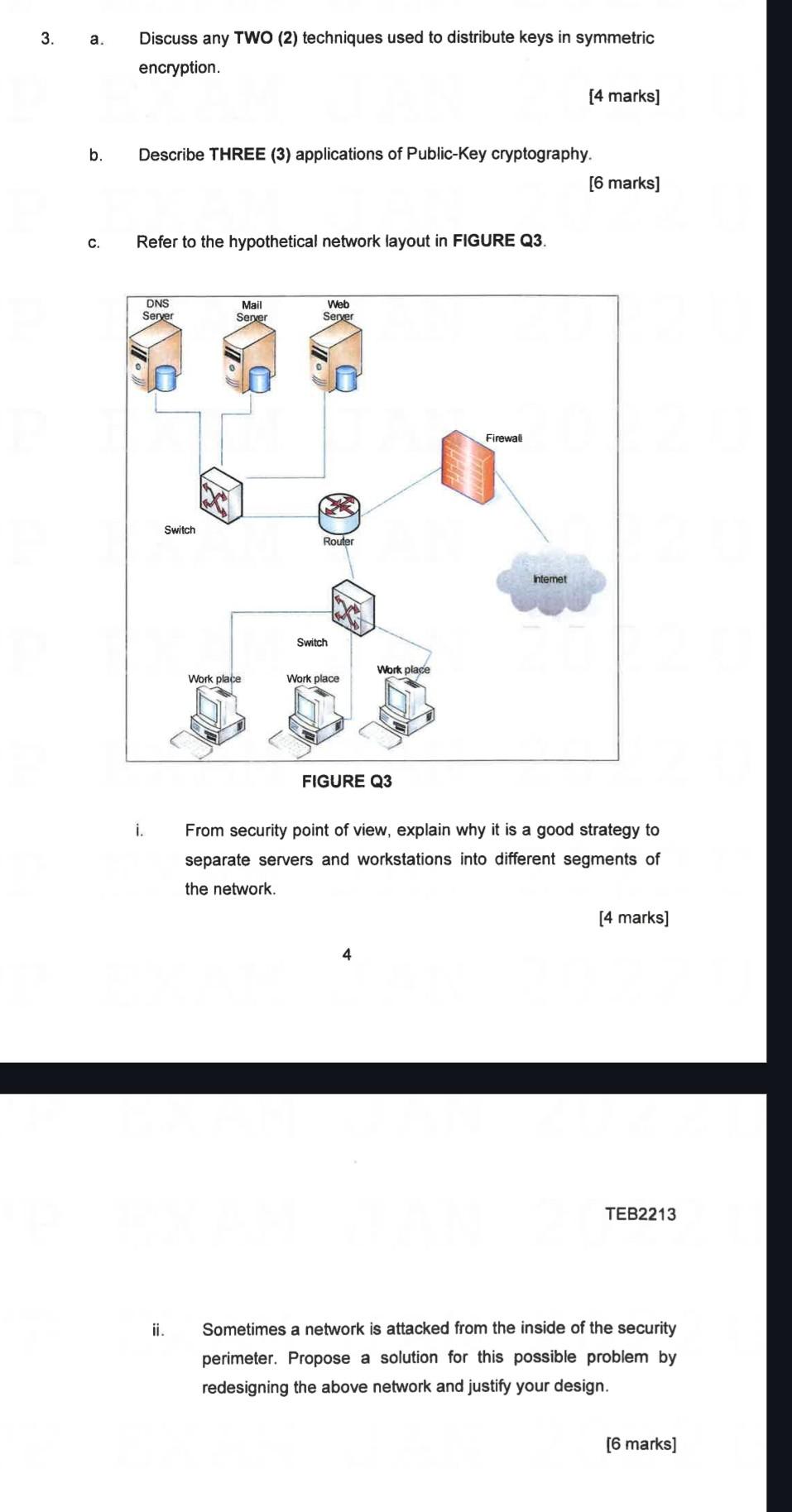
3. a. b. C. Discuss any TWO (2) techniques used to distribute keys in symmetric encryption. Describe THREE (3) applications of Public-Key cryptography. Refer to the hypothetical network layout in FIGURE Q3. DNS Server i. Switch ii. Mail Server Work place Web Server Router Switch Work place Work place FIGURE Q3 4 Firewall [4 marks] Internet [6 marks] From security point of view, explain why it is a good strategy to separate servers and workstations into different segments of the network. [4 marks] TEB2213 Sometimes a network is attacked from the inside of the security perimeter. Propose a solution for this possible problem by redesigning the above network and justify your design. [6 marks]
Step by Step Solution
There are 3 Steps involved in it
3 a Two techniques to distribute keys in symmetric encryption are 1 Key Distribution Centers KDCs A KDC manages the generation storage and distribution of keys When a user or node on the network needs ... View full answer

Get step-by-step solutions from verified subject matter experts


