Question: 3. (Texbook Q 3.60) Consider the following source code, where R, S, and T are constants declared with int ACR] [S] [T]; int store_ele(int i,
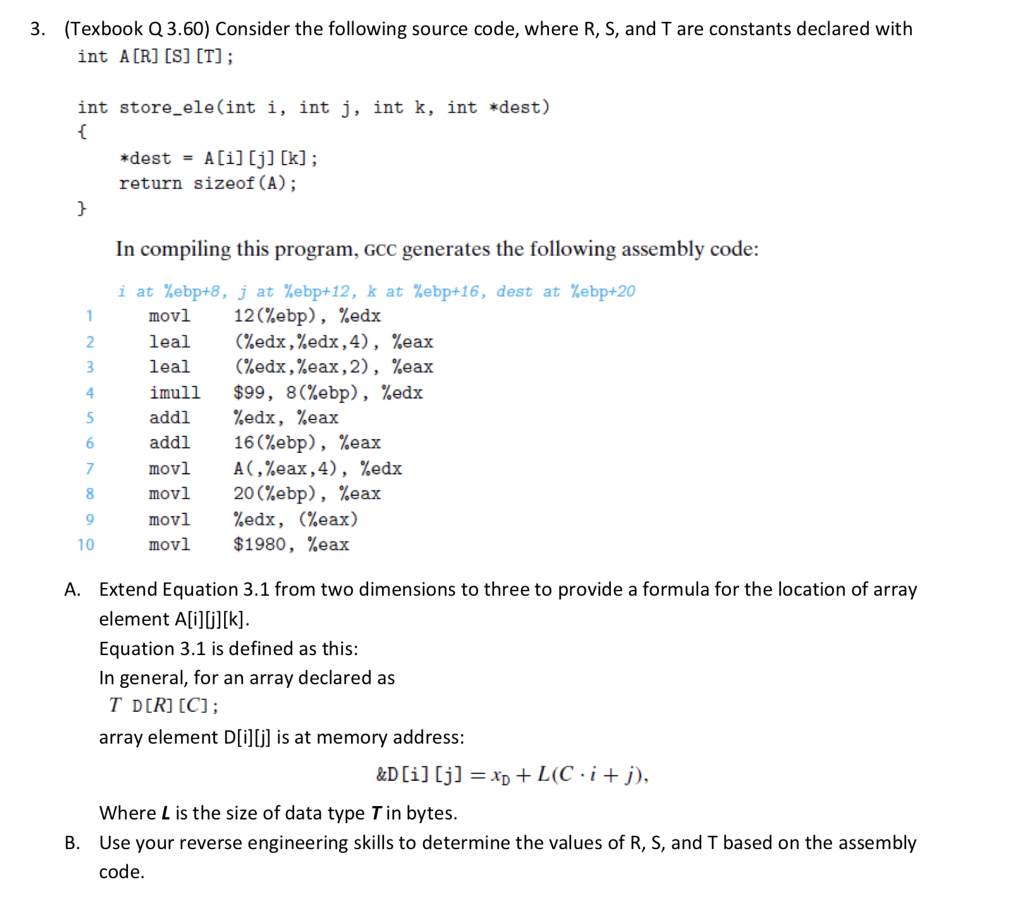
3. (Texbook Q 3.60) Consider the following source code, where R, S, and T are constants declared with int ACR] [S] [T]; int store_ele(int i, int j, int k, int *dest) *dest-A[i] [j] [k]; return sizeof (A); In compiling this program, GcC generates the following assembly code: %ebpt8, mov1 12(%ebp) ,%eax leal (%edx , %edx ,4), %eax leal (%eax , %eax , 2), %eax mull $99, 8(%ebp), %eax addl %eax , %eax addl 16(/ebp), eax mov! A(,%eax , 4), %edx movl 20(%ebp) ,%eax movl %eax ,(%eax) movl $1980 ,%eax i at J at %ebp+12, k at %ebp+16, dest at %ebp+20 Extend Equation 3.1 from two dimensions to three to provide a formula for the location of array element Ali0l[k]. Equation 3.1 is defined as this: In general, for an array declared as A. T DDR] [C]; array element D[i](j] is at memory address Where L is the size of data type T in bytes Use your reverse engineering skills to determine the values of R, S, and T based on the assembly code. B. 3. (Texbook Q 3.60) Consider the following source code, where R, S, and T are constants declared with int ACR] [S] [T]; int store_ele(int i, int j, int k, int *dest) *dest-A[i] [j] [k]; return sizeof (A); In compiling this program, GcC generates the following assembly code: %ebpt8, mov1 12(%ebp) ,%eax leal (%edx , %edx ,4), %eax leal (%eax , %eax , 2), %eax mull $99, 8(%ebp), %eax addl %eax , %eax addl 16(/ebp), eax mov! A(,%eax , 4), %edx movl 20(%ebp) ,%eax movl %eax ,(%eax) movl $1980 ,%eax i at J at %ebp+12, k at %ebp+16, dest at %ebp+20 Extend Equation 3.1 from two dimensions to three to provide a formula for the location of array element Ali0l[k]. Equation 3.1 is defined as this: In general, for an array declared as A. T DDR] [C]; array element D[i](j] is at memory address Where L is the size of data type T in bytes Use your reverse engineering skills to determine the values of R, S, and T based on the assembly code. B
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


