Question: 3. Worm. A program that reproduces itself without being attached to other instructions within the computerff5 4. Digital Hiding When digital files can be altered
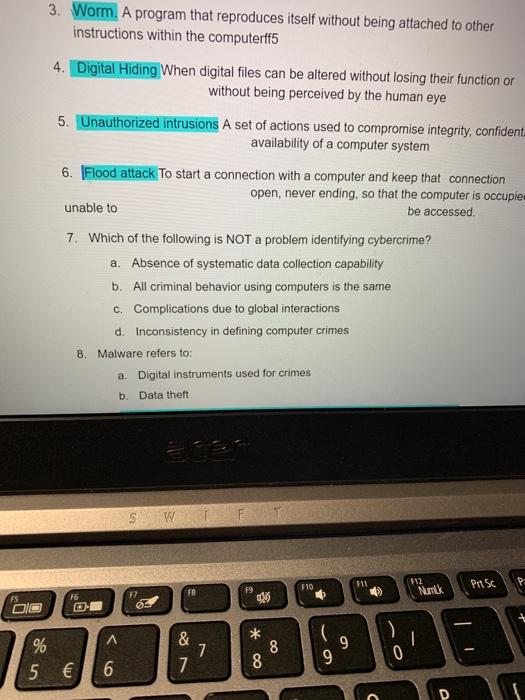
3. Worm. A program that reproduces itself without being attached to other instructions within the computerff5 4. Digital Hiding When digital files can be altered without losing their function or without being perceived by the human eye 5. Unauthorized intrusions A set of actions used to compromise integrity, confident availability of a computer system 6. Flood attack To start a connection with a computer and keep that connection open, never ending, so that the computer is occupie unable to be accessed. 7. Which of the following is NOT a problem identifying cybercrime? a. Absence of systematic data collection capability b. All criminal behavior using computers is the same C. Complications due to global interactions d. Inconsistency in defining computer crimes 8. Malware refers to: a. Digital instruments used for crimes Data theft b w 111 F10 512 Nurrik Presc F9 88 F2 S fo * ) % & 7 7 8 8 9 5 6 D
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


