Question: 3 Your task This assignment will give you an oppurtunity to work with inheritance, polymorphism, aggregation, exception handling, and cryptography. You will create multiple classes
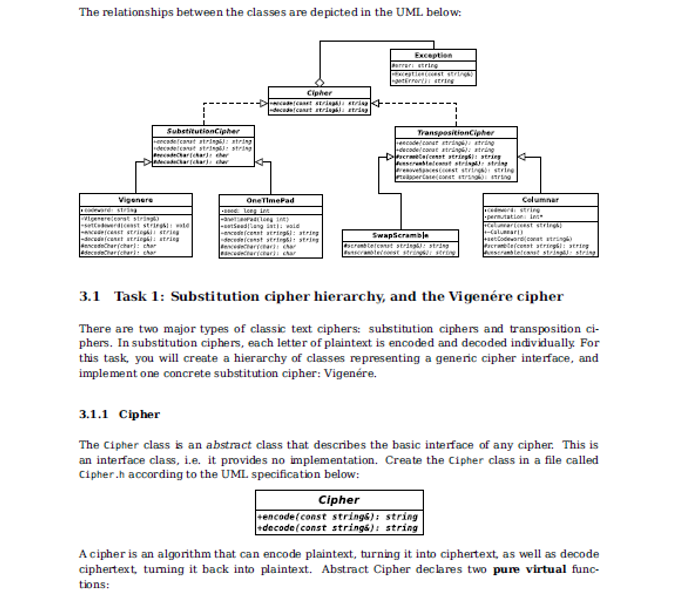
3 Your task This assignment will give you an oppurtunity to work with inheritance, polymorphism, aggregation, exception handling, and cryptography. You will create multiple classes that interact 1 through inheritance and aggregation. Create the classes as they are discussed for each task below. Test your work for each task thoroughly before submitting to the corresponding automarker upload slot and moving on to the next task. Each task is evaluated separately, but will rely on the classes you created in previous tasks. The classes you will create for each task are: 1. Cipher, SubstitutionCipher, Exception, Vigenere 2. OneTimePad 3. TranspositionCipher, SwapScramble 4. Columnar The relationships between the classes are depicted in the UML below:
string encode(const string&) This function is abstract and must be overridden by the derived classes. The function will receive plaintext (string) as input, encrypt it, and return encrypted ciphertext (string). 2 string decode(const string&) This function is abstract and must be overridden by the derived classes. The function will receive ciphertext (string) as input, decode it, and return decoded plaintext (string).
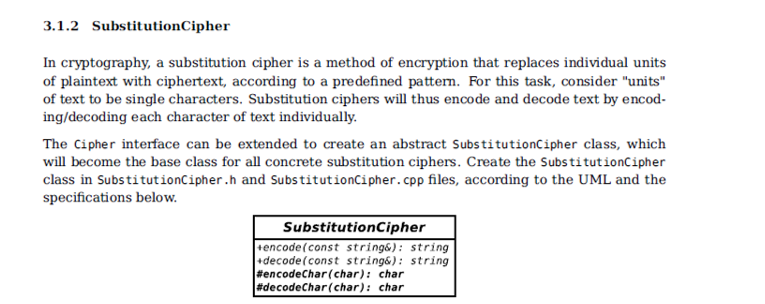 Since characters are going to be encrypted and decrypted individually, two protected functions can be added to the SubstitutionCipher class: char encodeChar(char) This function is abstract (pure virtual) and must be overridden by the derived classes. The function will receive a plaintext character (char) as input, encrypt it, and return ciphertext character (char). char decodeChar(char) This function is abstract (pure virtual) and must be overridden by the derived classes. The function will receive a ciphertext character (char) as input, decode it, and return plaintext character (char). The functions are protected because the user is expected to interact with the class via the inherited public interface of the parent class (Cipher). The abstract functions inherited from the parent class Cipher can be overidden and implemented now: string encode(const string&) This function receives plaintext (string) as input, encrypts it by applying encodeChar function to each character of plaintext, and returns the ciphertext (string). string decode(const string&) This function receives ciphertext (string) as input, decodes it by applying decodeChar to every character of ciphertext, and returns plaintext (string). Note that the SubstitutionCipher is still an abstract class, because it has two pure virtual functions. However, it does implement some of the functionality according to the interface of the Cipher class. The non-abstract encode and decode functions make use of the abstract encodeChar and decodeChar functions. When a child class implements encodeChar and decodeChar as prescribed by the SubstitutionCipher, the SubstitutionCipher will already know how to apply these functions to plaintext and ciphertext. Such interaction between the classes in the hierarchy allows for modular design and distributed implementation, making it a well-known object-oriented design pattern. This design pattern is known as the Template Method pattern, and you are encouraged to read more about it: https://en.wikipedia.org/wiki/Template_method_pattern. 3
Since characters are going to be encrypted and decrypted individually, two protected functions can be added to the SubstitutionCipher class: char encodeChar(char) This function is abstract (pure virtual) and must be overridden by the derived classes. The function will receive a plaintext character (char) as input, encrypt it, and return ciphertext character (char). char decodeChar(char) This function is abstract (pure virtual) and must be overridden by the derived classes. The function will receive a ciphertext character (char) as input, decode it, and return plaintext character (char). The functions are protected because the user is expected to interact with the class via the inherited public interface of the parent class (Cipher). The abstract functions inherited from the parent class Cipher can be overidden and implemented now: string encode(const string&) This function receives plaintext (string) as input, encrypts it by applying encodeChar function to each character of plaintext, and returns the ciphertext (string). string decode(const string&) This function receives ciphertext (string) as input, decodes it by applying decodeChar to every character of ciphertext, and returns plaintext (string). Note that the SubstitutionCipher is still an abstract class, because it has two pure virtual functions. However, it does implement some of the functionality according to the interface of the Cipher class. The non-abstract encode and decode functions make use of the abstract encodeChar and decodeChar functions. When a child class implements encodeChar and decodeChar as prescribed by the SubstitutionCipher, the SubstitutionCipher will already know how to apply these functions to plaintext and ciphertext. Such interaction between the classes in the hierarchy allows for modular design and distributed implementation, making it a well-known object-oriented design pattern. This design pattern is known as the Template Method pattern, and you are encouraged to read more about it: https://en.wikipedia.org/wiki/Template_method_pattern. 3

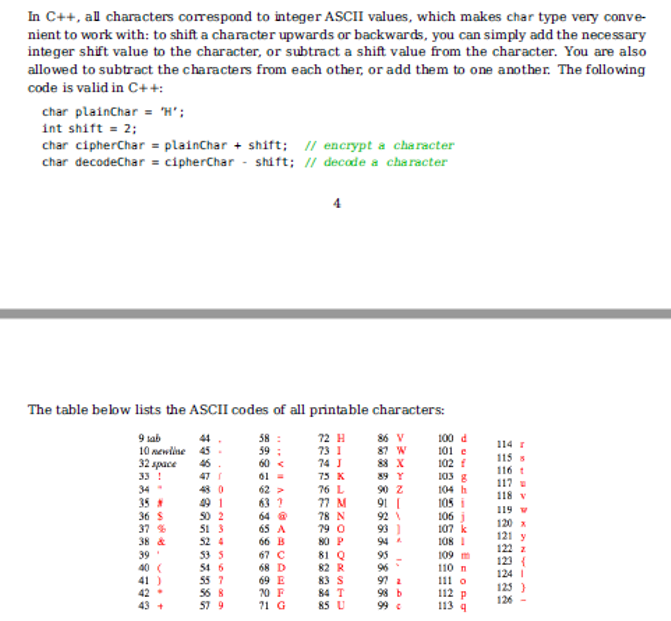 Tabs and newlines (ASCII codes 9 and 10) add too much of a visual distortion and are not convenient to work with, therefore for this assignment we will limit the available range of codes to [32,126]. Thus, the available alphabet is made of 126 - 32 + 1 = 95 symbols. Space character (ASCII value 32) will be treated as the first letter of the alphabet. What will happen if you try to shift } (ASCII code: 125) by 3 positions forward? 125 + 3 = 128, which is out of the printable range. In this case, encoding has to be wrapped around the ASCII table: once you reach the end, go back to the beginning (code 32). Thus, shifting } by 3 positions should take you to !. Same applies to decoding: if subtracting a shift value produces an out-of-printable-range code, wrap it around the table. Decoding ! should give you }. Implement the Vigenere class according to the UML and the specifications below:
Tabs and newlines (ASCII codes 9 and 10) add too much of a visual distortion and are not convenient to work with, therefore for this assignment we will limit the available range of codes to [32,126]. Thus, the available alphabet is made of 126 - 32 + 1 = 95 symbols. Space character (ASCII value 32) will be treated as the first letter of the alphabet. What will happen if you try to shift } (ASCII code: 125) by 3 positions forward? 125 + 3 = 128, which is out of the printable range. In this case, encoding has to be wrapped around the ASCII table: once you reach the end, go back to the beginning (code 32). Thus, shifting } by 3 positions should take you to !. Same applies to decoding: if subtracting a shift value produces an out-of-printable-range code, wrap it around the table. Decoding ! should give you }. Implement the Vigenere class according to the UML and the specifications below:
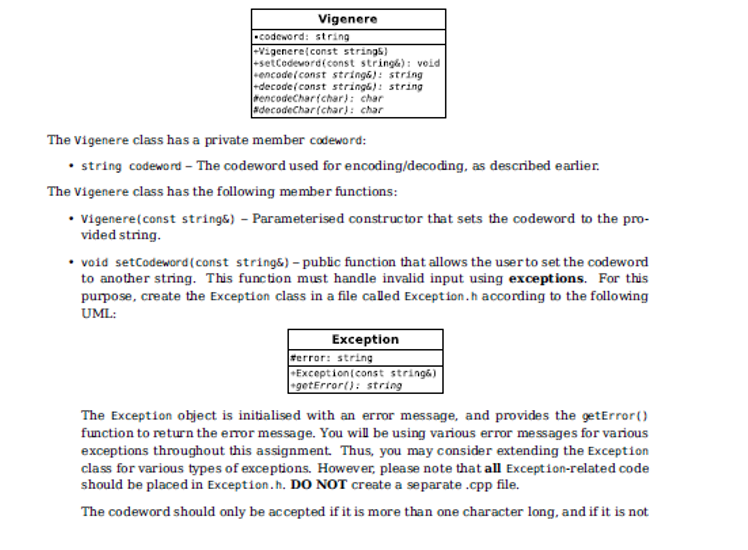
made entirely of (space) characters. The space character (ASCII code 32) is the first printable character in the given range, thus a codeword made entirely of spaces would result in shifts of zero, and the text will not be encrypted. If the codeword is either too short, or made out of spaces, throw an Exception object initialised with the following message: The codeword provided is not going to generate a safe encryption. The message should contain no punctuation and no new line characters. char encodeChar(char) this function implements Vigenre encoding. A plaintext char is received as input and shifted according to the current place in the codeword. The shifted char is returned. No error-checking has to be done in this function. char decodeChar(char) this function implements Vigenre decoding. A ciphertext char is received as input, and the decoded char is returned. No error-checking has to be done in this function. Note that encode(string) and decode(string) are also listed in the UML. You may override these functions if you need to add extra functionality to them. Remember that child classes have access to the base class implementations for the purpose of code re-use. Vigenere class is not an abstract class, therefore you can instantiate a Vigenere object and test your code. Test your encoding thoroughly before submitting for marking! Here are some examples for different codewords:

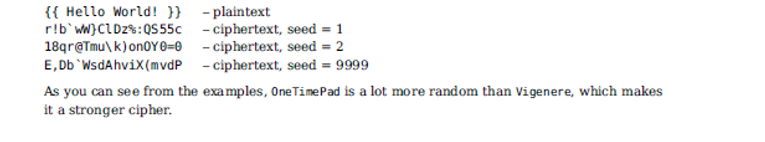
3.1.4 Test and submit for marking Test your code. When you are certain the code works as expected, compress all of your code (.h and .cpp) into a single archive (either .tar.gz, .tar.bz2 or .zip make sure there are no folders or sub-folders in the archive) and submit it for marking to the appropriate upload slot (Assignment 3, Task 1) before the deadline. Note that you do not need to upload a makefile for this assignment. Also note that the number of uploads is limited and should be used wisely. 3.2 Task 2: One-Time Pad cipher Vigenre cipher is simple, and therefore not very secure, especially if a short and simple codeword is used. You are going to create a much stronger substitution cipher: the one-time pad. In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked if used correctly. In this technique, a random sequence of shifts is used in place of a codeword. If the sequence is truly random, is at least as long as the plaintext, is never reused in whole or in part, and is kept completely secret, then the resulting ciphertext will be impossible to decode or break. One-time pads were employed by Soviet espionage agencies for covert communications with agents and agent controllers. For this assignments approach to one-time pads, you will create a sequence of random shifts. Every character of plaintext will be encoded similarly to the Vigenre cipher, but the shift value for each character will be generated using a random number generator. The randomly generated shifts must adhere to the [1,94] range (inclusive), and should wrap around the ASCII table in the same fashion as used in the Vigenere cipher. To decipher a one-time-pad ciphertext 6 message, the same sequence of random numbers will have to be used. Random number sequence returned by rand() (http://www.cplusplus.com/reference/cstdlib/rand/) is determined by the seed value, therefore, the seed value will have to be stored. Create the OneTimePad class in OneTimePad.h and OneTimePad.cpp files. Implement the OneTimePad class according to the specifications and the UML below:
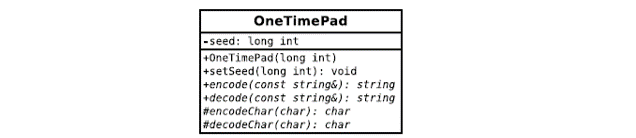
The seed is stored in a private member variable: long int seed The seed value used to generate the random shifts. OneTimePad adds two extra functions to the inherited interface: OneTimePad(long int) OneTimePads only constructor; sets the seed value to the specified seed. void setSeed(long int) Sets the seed value to the specified seed. Only non-negative values can be accepted. If a negative value is given as input, throw an Exception object initialised with the following message: Negative number provided. Inherited encodeChar() and decodeChar() functions must be overidden in the OneTimePad to implement random one-time-pad shift algorithm as described above. Note that any of the inherited functions can be overidden in the derived classes as necessary, and you are free to do so. OneTimePad class is not an abstract class, therefore you can instantiate a OneTimePad object and test your code. Test your encoding thoroughly! Here are some examples for different seeds (random number generators are platform-dependent, and encryptions may differ on your machine):



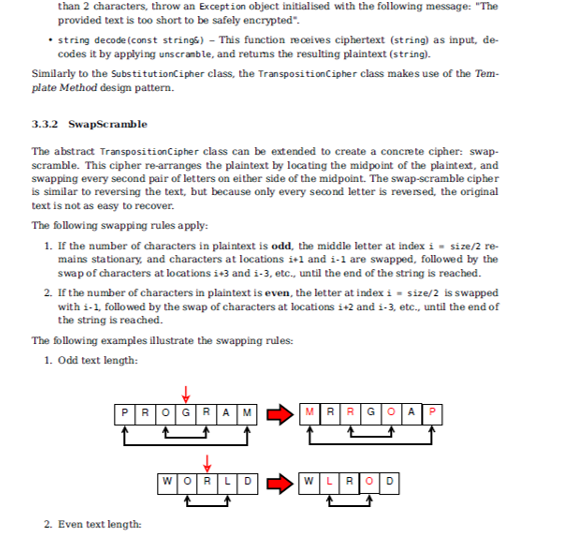
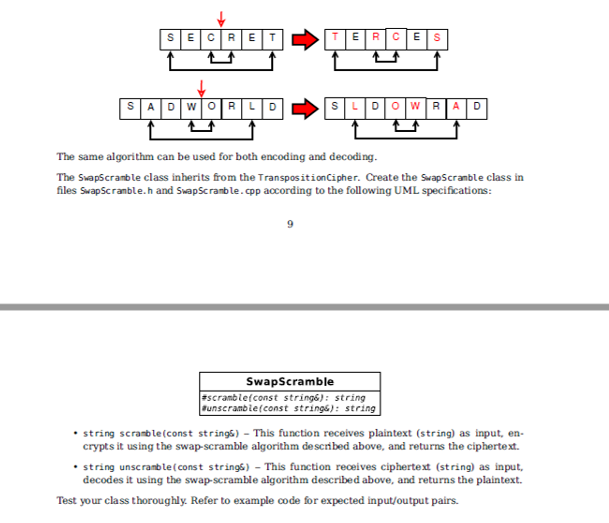
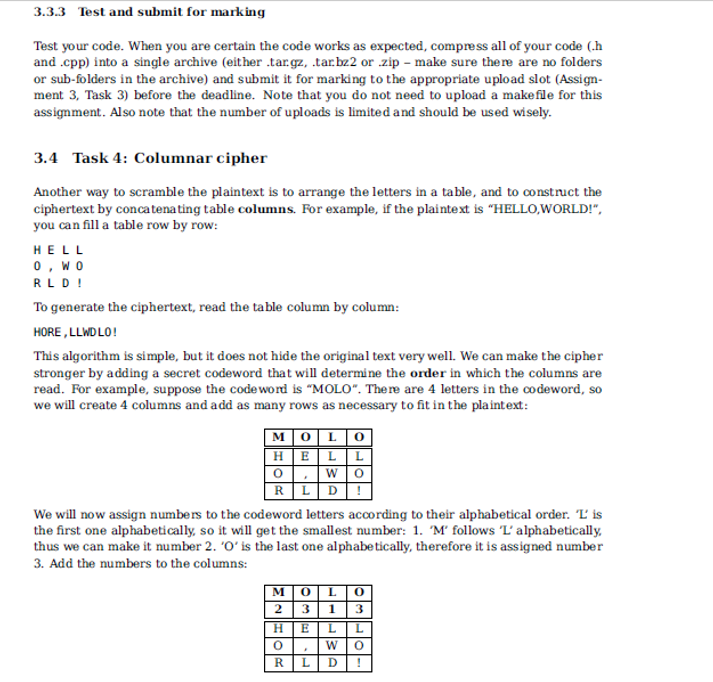
Now that the columns have been numbered, we can read the text columns-wise according to the assigned numbers: first the L column, then the M column, and finally both O columns. To make the cipher stronger still, a special rule will be imposed on the columns that have the same number: the text will be read row-wise from the set of columns that share the same index. The resulting ciphertext is then: LWDHOREL,OL! (1st column: LWD, 2nd column: HOR, 3rd and 4th columns: EL,OL!, where the blue characters correspond to the second O column.) Now the plaintext has been safely scrambled. How do you recover the plaintext from the ciphertext? Well, if you know the codeword, the task is easy: create a table of the correct size, use the codeword indices to fill the table in the correct order. Once the table has been filled, read the text row-wise. Lets decode the ciphertext generated earlier: LWDHOREL,OL! We know that the codeword is MOLO. If you divide the length of the ciphertext by the length of the codeword, you will get the number of rows necessary to store the text: 12/4 = 3. Create a 3x4 table: 

HINT: The columnar cipher relies on putting the text into a table/matrix, and reading from that table/matrix in a particular way. You can make the implementation a lot simpler by adding extra helper functions to the Columnar class to assist you with creating and deleting 2D arrays. For example, you may consider writing a private createMatrix(int, int) function to allocate a 2D array of the given dimensionality; it will also be convenient to have a deleteMatrix(char **, int) function to deallocate the 2D array, and a fillMatrix(char **, int, int, string) function to fill the empty matrix with the characters of the given string. None of these functions are required, they will not be tested by the automarker. However, you will find that working with modular code is a lot easier! Test your class thoroughly. Refer to example code for expected input/output pairs. 3.4.1 Test and submit for marking Test your code. When you are certain the code works as expected, compress all of your code (.h and .cpp) into a single archive (either .tar.gz, .tar.bz2 or .zip make sure there are no folders or 12 sub-folders in the archive) and submit it for marking to the appropriate upload slot (Assignment 3, Task 4) before the deadline. Note that you do not need to upload a makefile for this assignment. Also note that the number of uploads is limited and should be used wisely. The End
The relationships between the classes are depicted in the UML below: Exception Cipher SubetitutionCipher ipy string 3.1 Task 1: Substitution cipher hierarchy, and the Vigenre cipher There are two major types of classic text ciphers: substitution ciphers and transposition phers. In substitution ciphers, each letter of plaintext is encoded and decoded individually For this task, you will create a hierarchy of classes representing a generic cipher interface, and implement one concrete substitution cipher: Vigenre. 3.1.1 Cipher The Cipher class is an abstract class that describes the basic interface of any cipher. This is an interface class, i.e. it provides no implementation. Create the Cipher class in a file called Cipher.h according to the UML specification below: Cipher code(const string):string e(const string) string A cipher is an algorithm that can encode plaintext, turning it into ciphertext, as well as decode ciphertext, turning it back into plaintext. Abstract Cipher declares two pure virtual func- tions: The relationships between the classes are depicted in the UML below: Exception Cipher SubetitutionCipher ipy string 3.1 Task 1: Substitution cipher hierarchy, and the Vigenre cipher There are two major types of classic text ciphers: substitution ciphers and transposition phers. In substitution ciphers, each letter of plaintext is encoded and decoded individually For this task, you will create a hierarchy of classes representing a generic cipher interface, and implement one concrete substitution cipher: Vigenre. 3.1.1 Cipher The Cipher class is an abstract class that describes the basic interface of any cipher. This is an interface class, i.e. it provides no implementation. Create the Cipher class in a file called Cipher.h according to the UML specification below: Cipher code(const string):string e(const string) string A cipher is an algorithm that can encode plaintext, turning it into ciphertext, as well as decode ciphertext, turning it back into plaintext. Abstract Cipher declares two pure virtual func- tions
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


