Question: 3.4-2 The rdt 2.0 protocol. Consider the rdt 2.0 sender and receiver shown below, with FSM transitions at the sender labeled S1, S2, and S3;
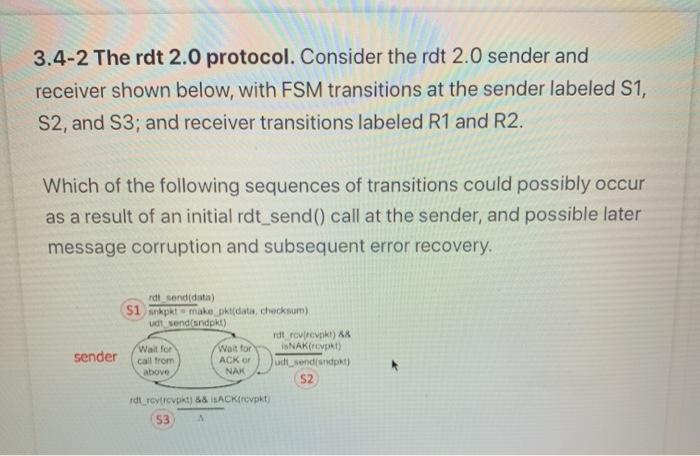
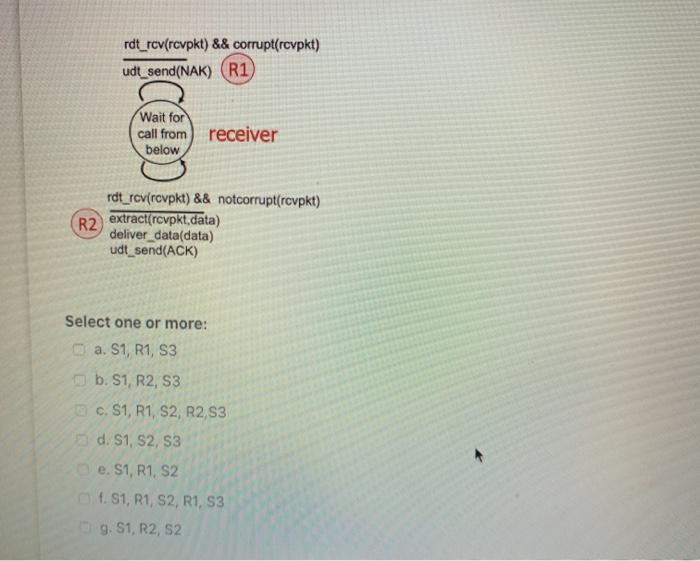
3.4-2 The rdt 2.0 protocol. Consider the rdt 2.0 sender and receiver shown below, with FSM transitions at the sender labeled S1, S2, and S3; and receiver transitions labeled R1 and R2. Which of the following sequences of transitions could possibly occur as a result of an initial rdt_send() call at the sender, and possible later message corruption and subsequent error recovery. rdt send(data) si spt make philata, checksum) di vend(sndpkt) Ydt revirkt) Wait for Wait for NAK (1) sender call from ACK OF udt sendandpkt) above NAK S2 di tovrekt) && LACKrepkt) 53 rdt_rcv(revpkt) && corrupt(revpkt) udt_send(NAK) (R1 Wait for call from below receiver rdt_revrcvpkt) && notcorrupt(revpkt) (R2) extract(revpkt, data) deliver_data(data) udt_send(ACK) Select one or more: a. S1, R1, S3 b. S1, R2, S3 c. S1, R1, S2, R2,83 d. S1, S2, S3 e. S1, R1, S2 f. S1, R1, S2, R1, S3 9. S1, R2, S2
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


