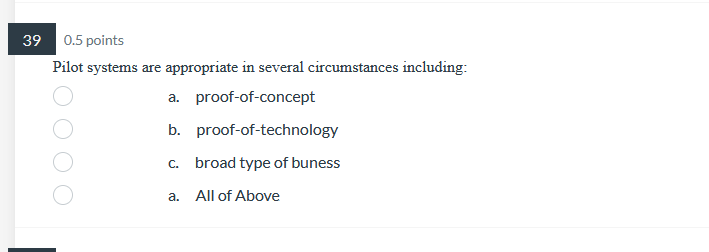
Question: 39 0.5 points Pilot systems are appropriate in several circumstances including: a. proof-of-concept b. proof-of-technology oooo C. broad type of buness a. All of Above26
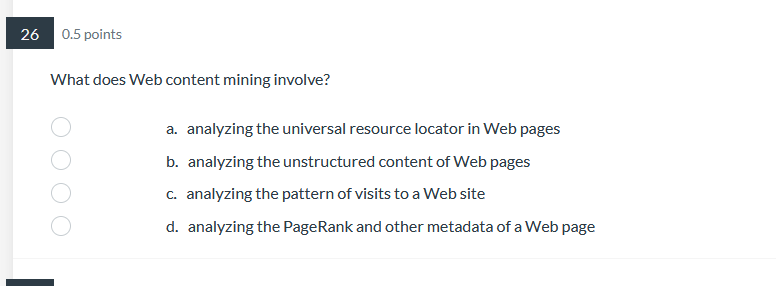
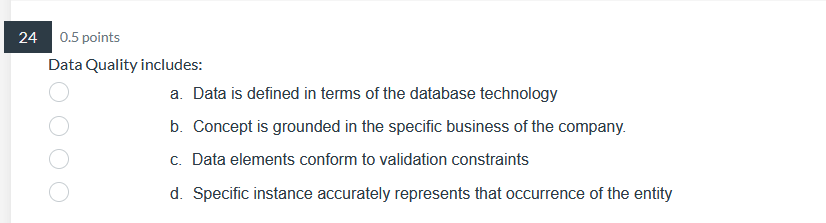
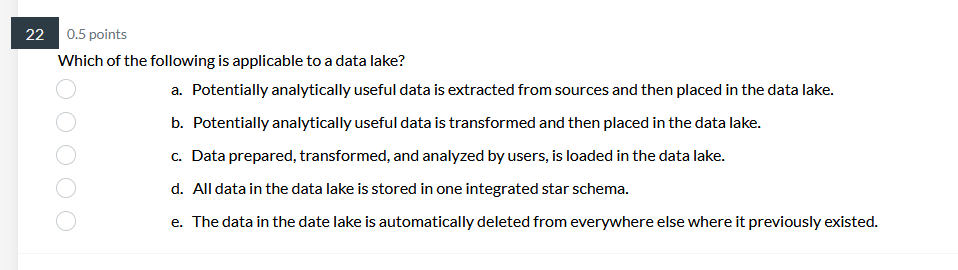
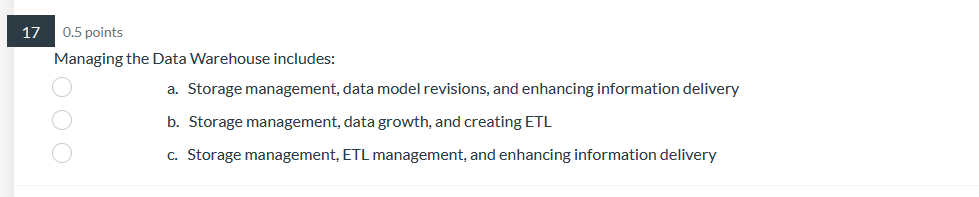
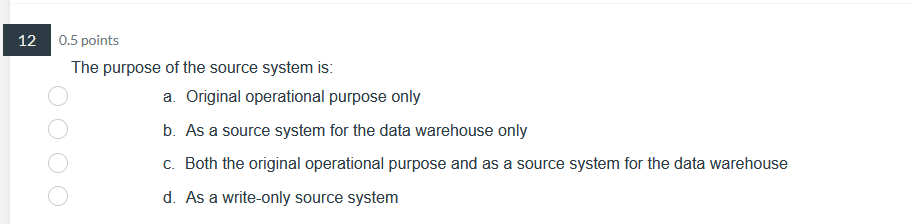
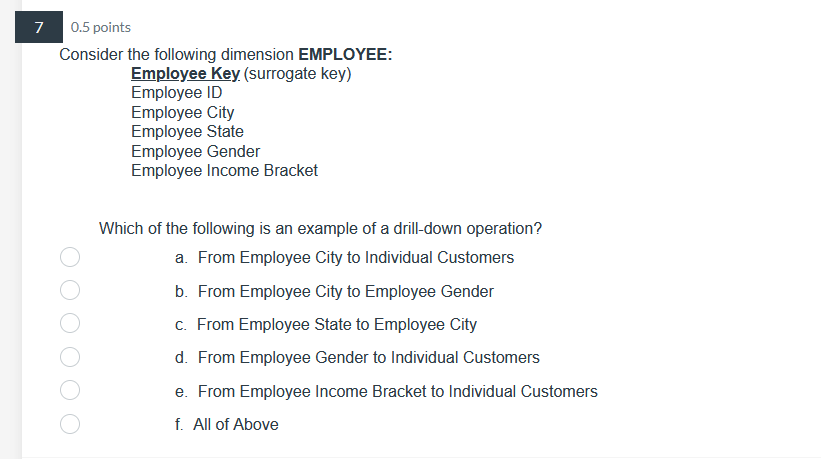
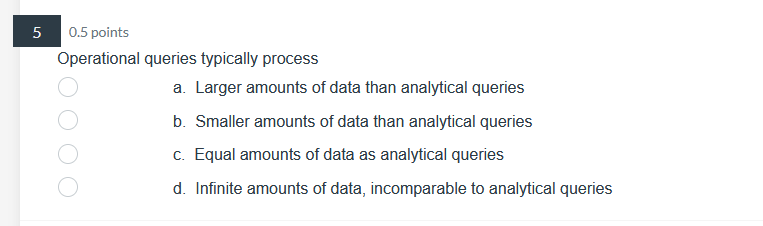
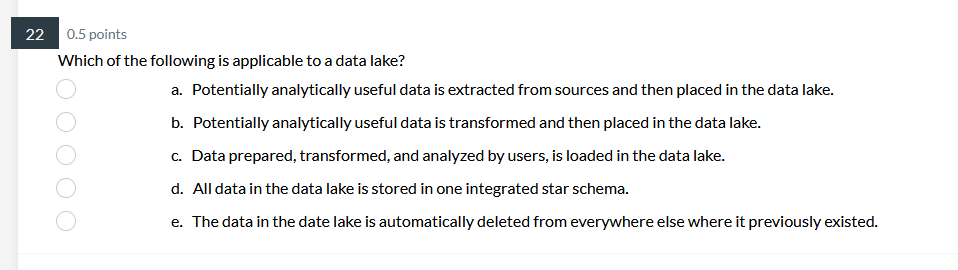
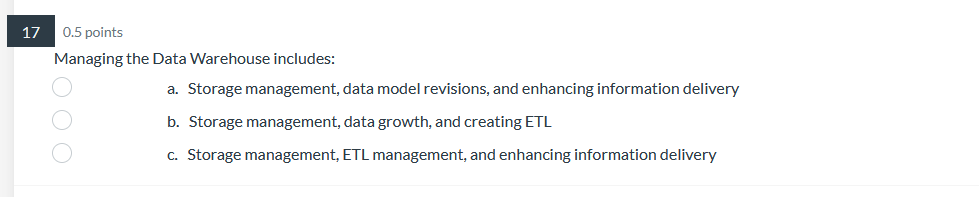
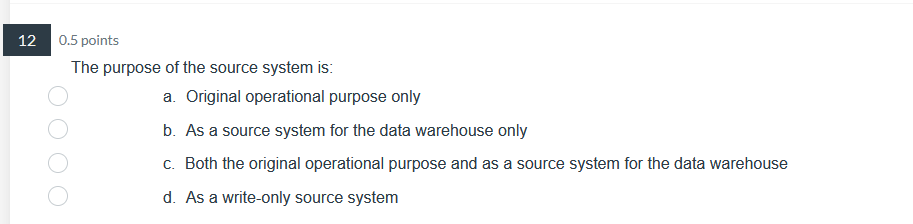
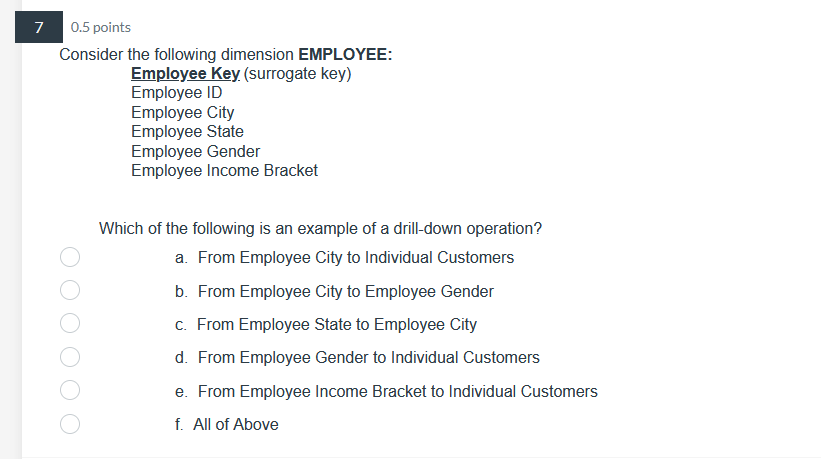
39 0.5 points Pilot systems are appropriate in several circumstances including: a. proof-of-concept b. proof-of-technology oooo C. broad type of buness a. All of Above26 0.5 points What does Web content mining involve? a. analyzing the universal resource locator in Web pages b. analyzing the unstructured content of Web pages ooOO c. analyzing the pattern of visits to a Web site d. analyzing the PageRank and other metadata of a Web page24 0.5 points Data Quality includes: a. Data is defined in terms of the database technology b. Concept is grounded in the specific business of the company. ooOO c. Data elements conform to validation constraints d. Specific instance accurately represents that occurrence of the entity0.5 points Which of the following is applicable to a data lake? a. Potentially analytically useful data is extracted from sources and then placed in the data lake. b. Potentially analytically useful data is transformed and then placed in the data lake. c. Data prepared, transformed, and analyzed by users, is loaded in the data lake. d. All data in the data lake is stored in one integrated star schema. e. The data in the date lake is automatically deleted from everywhere else where it previously existed. 17 0.5 points. Managing the Data Warehouse includes: a. Storage management, data model revisions, and enhancing information delivery b. Storage management, data growth, and creating EFL c. Storage management, EFL management, and enhancing information delivery 0.5 points The purpose of the source system is: a. Original operational purpose only b. As a source system for the data warehouse only c. Both the original operational purpose and as a source system for the data warehouse {1. As a writeonly source system 7 0.5 points Consider the following dimension EMPLOYEE: Employee Key (surrogate key) Employee ID Employee City Employee State Employee Gender Employee Income Bracket Which of the following is an example of a drill-down operation? a. From Employee City to Individual Customers b. From Employee City to Employee Gender c. From Employee State to Employee City oooOOO d. From Employee Gender to Individual Customers e. From Employee Income Bracket to Individual Customers f. All of Above5 0.5 points Operational queries typically process a. Larger amounts of data than analytical queries b. Smaller amounts of data than analytical queries ooOO c. Equal amounts of data as analytical queries d. Infinite amounts of data, incomparable to analytical queries3 0.5 points The steps in the construction of data mining include: a. Identify the infrastructure, determine the detail level, analyze the patterns, and use the results. b. Identify the infrastructure, determine the aggregation, analyze the patterns, and use the results. OOOO c. Identify the infrastructure, determine the detail level, analyze the patterns, and interpret the input. d. Identify the infrastructure, determine the detail level, analyze the patterns, and modify the results
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


