Question: 4. * A forgery attack on UMTA/4G-LTE integrity check and authentication. Let a small size UIA2/EIA1 be defined over a finite field GF(31) where
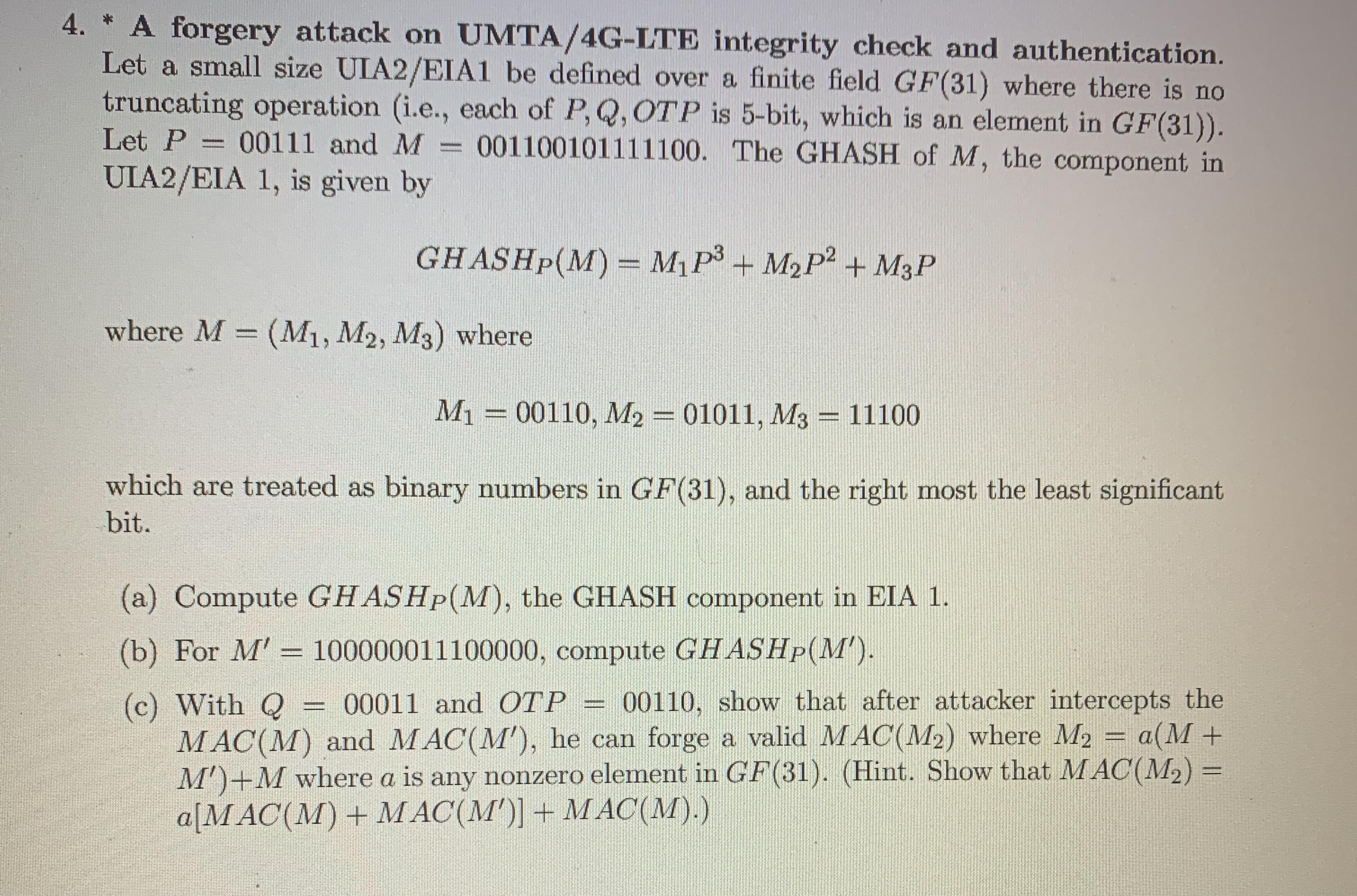
4. * A forgery attack on UMTA/4G-LTE integrity check and authentication. Let a small size UIA2/EIA1 be defined over a finite field GF(31) where there is no truncating operation (i.e., each of P, Q, OTP is 5-bit, which is an element in GF(31)). Let P = 00111 and M = 001100101111100. The GHASH of M, the component in UIA2/EIA 1, is given by GHASHP(M) = MP + MP + M3P where M = (M1, M2, M3) where M = 00110, M2 = 01011, M3 = 11100 which are treated as binary numbers in GF(31), and the right most the least significant bit. (a) Compute GHASHp(M), the GHASH component in EIA 1. (b) For M' = 100000011100000, compute GHASHp(M'). (c) With Q = 00011 and OTP 00110, show that after attacker intercepts the MAC(M) and MAC(M'), he can forge a valid MAC(M) where M a(M + M')+M where a is any nonzero element in GF(31). (Hint. Show that MAC(M) = a[MAC(M) + MAC(M')] + MAC(M).) CREADO
Step by Step Solution
3.25 Rating (160 Votes )
There are 3 Steps involved in it
a GHASHPM MP3 M2P2 M3P 00110P3 01011P2 11100P 2631P3 1021P2 3025P 14795P3 16676P2 311P 160671P3 1834... View full answer

Get step-by-step solutions from verified subject matter experts


