Question: 5. Briefly describe management, operational, and technical controls, and explain when each would be applied as part of a security framework. 6. Using the following
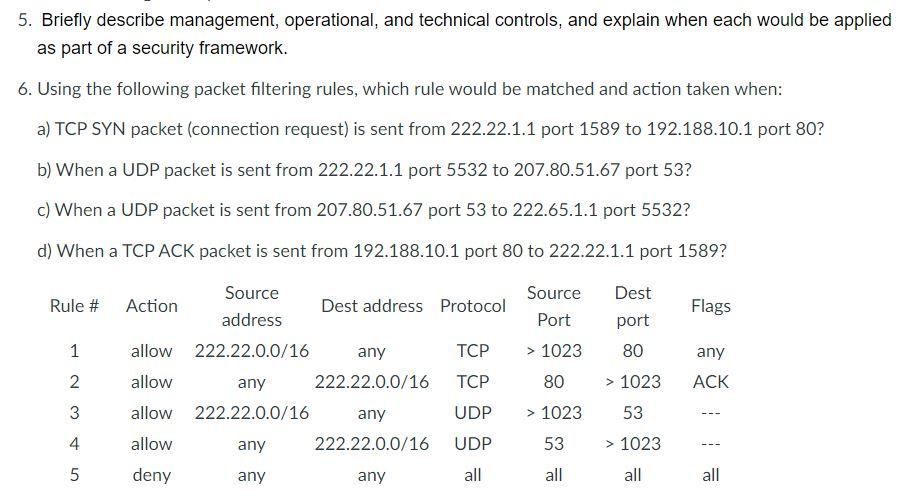
5. Briefly describe management, operational, and technical controls, and explain when each would be applied as part of a security framework. 6. Using the following packet filtering rules, which rule would be matched and action taken when: a) TCP SYN packet (connection request) is sent from 222.22.1.1 port 1589 to 192.188.10.1 port 80? b) When a UDP packet is sent from 222.22.1.1 port 5532 to 207.80.51.67 port 53? c) When a UDP packet is sent from 207.80.51.67 port 53 to 222.65.1.1 port 5532? d) When a TCP ACK packet is sent from 192.188.10.1 port 80 to 222.22.1.1 port 1589? Source Port > 1023 Dest port Flags 80 Source Rule # Action Dest address Protocol address 1 allow 222.22.0.0/16 any TCP 2 allow any 222.22.0.0/16 TCP 3 allow 222.22.0.0/16 any UDP 4 allow any 222.22.0.0/16 UDP 5 deny any any all any ACK 80 > 1023 > 1023 53 53 > 1023 all all all
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


