Question: ( 5 ) Diane McCann ( Instructor ) Jul 2 7 7 : 1 0 am Last reply Jul 2 8 3 : 0 2
Diane McCann
Instructor
Jul :am Last reply Jul :am
Class let's begin with the opening question on fact or myth:
Have you ever believed information you read on the Internet or was sent to you by a friend and later discovered the information was fake? When something appears to be true, do you ever do a 'factcheck' on the information? Where do you go to find credible sources?
Dr McCann
diane.mccann@devry.edu
larr Reply I Like I Mark as Unread I Reply
Class let's begin with the opening question on fact or myth:
Have you ever believed information you read on the Internet or was sent to you by a friend and later discovered the information was fake? When something appears to be true, do you ever do a 'factcheck' on the information? Where do you go to find crdible sources
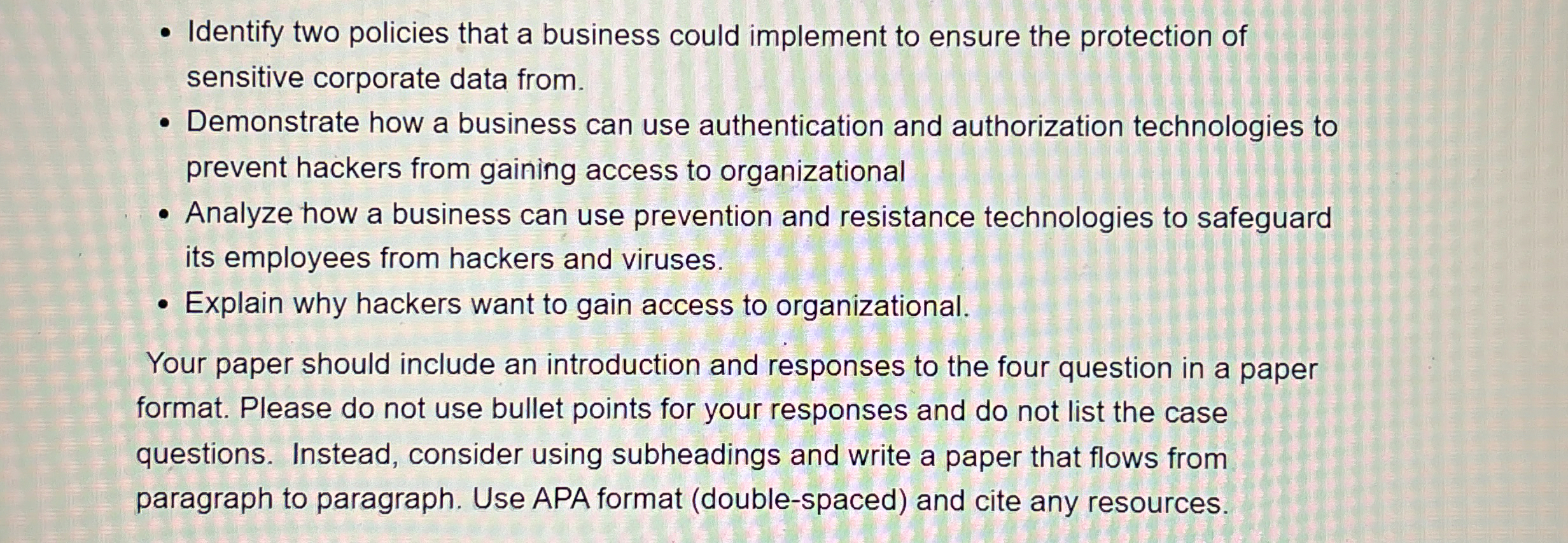
Identify two policies that a business could implement to ensure the protection of sensitive corporate data from.
Demonstrate how a business can use authentication and authorization technologies to prevent hackers from gaining access to organizational
Analyze how a business can use prevention and resistance technologies to safeguard its employees from hackers and viruses.
Explain why hackers want to gain access to organizational.
Your paper should include an introduction and responses to the four question in a paper format. Please do not use bullet points for your responses and do not list the case questions. Instead, consider using subheadings and write a paper that flows from paragraph to paragraph. Use APA format doublespaced and cite any resources.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


